Buran Ransomware Continues the Destructive Legacy of Its Predecessor VegaLocker
Buran ransomware first began making headway in May 2019. The malware infection is a Ransomware-as-a-Service threat, or RaaS. Leveraging RaaS threats is a rather common way for cybercriminals to make money. The simplest way to explain such a process is to understand that a RaaS attack is part of a subscription-based model that allows even the most unskilled cyber attacker to launch a ransomware threat onto the web. That's not a new, up-and-coming scheme either. It's been available online for quite some time. You can even come across a multitude of RaaS packages on the market, ones that completely cut out the need to code malware.
That's why it's a perfect service for people who want to launch a malicious infection and wreak havoc online but don't have the technical knowledge to do so. The model lets anyone become an 'affiliate' of a RaaS package. The process involves affiliates distributing the ransomware to unsuspecting victims, and, the ransomware's creators get a cut of the profits from the extortion that follows. Other notorious RaaS threats include popular names like REVil, GandCrab, Phobos. The list of such threats is rather extensive, including Buran’s predecessor known as VegaLocker ransomware.
The entire affiliate-RaaS system works on the grounds of a collaboration. It's a system of trust between the malware code author, and the person using said code to unleash it onto unsuspecting victims. The person who crafted the malicious code gets a commission of the income earned from the ransomware attacks. Most RaaS threats charge anywhere between 30% to 40%. Buran demands only 25%, which undercuts its competitors' prices quite well. What's more, Buran's creators are open to negotiations. There is the potential to drop the commission amount even lower, making the idea of leveraging Buran even more attractive to cybercriminals.
Buran ransomware even has ads! They announce that each potential affiliate gets to make a personalized deal with the malware code creator. The ransomware was advertised in a popular Russian forum in an attempt to garner additional attention. The message is as follows:
| Buran is a stable offline cryptoclocker, with flexible functionality and support 24/7. Functional: Reliable cryptographic algorithm using global and session keys + random file keys; Scan all local drives and all available network paths; High speed: a separate stream works for each disk and network path; Skipping Windows system directories and browser directories; Decryptor generation based on an encrypted file; Correct work on all OSs from Windows XP, Server 2003 to the latest; The locker has no dependencies, does not use third-party libraries, only mathematics and vinapi; The completion of some processes to free open files (optional, negotiated); The ability to encrypt files without changing extensions (optional); Removing recovery points + cleaning logs on a dedicated server (optional); Standard options: tapping, startup, self-deletion (optional); Installed protection against launch in the CIS segment. Conditions: They are negotiated individually for each advert depending on volumes and material. Start earning with us! |
As it reads above, the ad claims that Buran has ''installed protection against launch in the CIS segment.'' In case you're unfamiliar, CIS is the Commonwealth of Independent States, fundamentally a confederation of countries that were once part of the Soviet Union. The countries included in the confederation are Armenia, Belarus, Kazakhstan, Kyrgyzstan, Moldova, Russia, Tajikistan, Turkmenistan, Ukraine, and Uzbekistan. The exclusion from Buran's potential attack may as well be a clue that its creators belong to one of the listed countries.
Researchers performed thorough checks to verify the statement of exclusion for the ten confederation countries. Only three were confirmed to be truly safe from Buran's clutches. As soon as the ransomware slithers into your system, it runs a check – it attempts to find out where your machine is registered. And, if it's revealed to be registered into Belarus, Russia, or Ukraine, Buran exits and has no apparent effect.
An exaggeration on Buran's part is its statement ''Correct work on all OSs from Windows XP, Server 2003 to the latest.'' Despite these claims of 'inclusivity,' researchers have proven this to be deceitful. However, Windows XP seems to be immune to attacks from Buran.
Table of Contents
The Evolution of Buran Ransomware
You cannot talk about Buran ransomware without mentioning the Jumper (Jamper) threat, and the VegaLocker menace. Buran ransomware is an evolution of the previous two. VegaLocker ransomware was first discovered in February 2019, Jumper – in March 2019. And, as stated, Buran ransomware came to be in May 2019. Those three infections are part of what's known as a 'malware family.' One is the original, which gave way for the other two to be created and plague web users.
VegaLocker, Jumper, and Buran ransomware are linked together with many similarities. All three of the threats are known to modify the Registry – they create multiple registry keys in an attempt to latch onto your PC and render removal difficult. The threats also create and store files on temporary folders, in the same way. They share the same base code, which gets modified with each evolution of the threat. Malware authors modify their malware code to make it better at its job (invading your system and wreaking havoc as efficiently as possible). They're attempting to pivot around anti-virus programs and avoid detection at the hands of security researchers. That's the most probable reason why VegaLocker has had as many revisions as it has. Buran is only the latest reiteration of the code.
Buran ransomware can scan local drives and network paths. It can encrypt files without changing extensions, as well as remove recovery points, clear logs, and delete the backup catalog. Buran can also self-delete, if it ever has the need to hide itself to evade detection.
Malware researchers have discovered two versions of Buran ransomware floating around the web, that actively affect computer users. Both are written in Delphi, which makes reverse engineering a rather tricky process. They remain quite similar but do share a few key differences. For one, the updated Buran has two new features attributed at its disposal. Its creators have introduced two new processes – shadow copies delete process; and backup catalog deletion. The Buran ransomware seems to endure improvements from its creators every few months. It's fair to say that new variants of the ransomware, also similar to VegaLocker ransomware, cannot be excluded as an option. Other than updates, Buran might even get to endure another brand name change, if it gets too much pressure from security experts.
Buran Ransomware’s Invasion Strategy – How It Ends Up in Your System
Buran ransomware gets delivered into your PC via the Rig Exploit Kit. It uses Microsoft Internet Explorer VBScript Engine Engine RCE vulnerability (CVE-2018-8174) to exploit machines for deployment. Once the exploit is a success, it launches a series of commands that download Buran on your system.
When the Rig exploit kit drops the Buran executable on your PC, immediate execution follows. The ransomware then makes sure to copy itself to the file path %APPDATA%\microsoft\windows\ctfmon.exe, and launches. It proceeds with encryption but does not target every single file on your machine. Rather, it excludes certain extensions from encryption. They are as follows: .cmd, .com, .cpl, .dll, .msc, .msp, .pif, .scr, .sys, .log, .exe, .buran. It also excludes certain folders and files.
Excluded folders:
|
\windows media player\ \apple computer\safari\ \windows photo viewer\ \windows portable devices\ \windows security\ \embedded lockdown manager\ \reference assemblies\ :\windows.old\ :\inetpub\logs\ :\$recycle.bin\ :\$windows.~bt\ \application data\ \google\chrome\ \mozilla firefox\ \opera software\ \tor browser\ \common files\ \internet explorer\ \windows defender\ \windows mail\ \windows nt\ \windowspowershell\ \windows journal\ \windows sidebar\ \package cache\ \microsoft help\ :\recycler :\windows\ c:\windows\ :\intel\ :\nvidia\ \all users\ \appdata\ \boot\ \google\ \mozilla\ \opera\ \msbuild\ \microsoft\ |
Excluded files:
| !!! your files are encrypted !!!.txt boot.ini bootfont.bin bootsect.bak defender.exe desktop.ini iconcache.db ntdetect.com ntuser.dat.log unlocker.exe master.exe master.dat ntldr ntuser.dat ntuser.ini temp.txt thumbs.db unlock.exe |
The Rig Exploit Kit is not the only method of invasion Buran uses. There are also the usual tricks – freeware, spam email campaigns, corrupted links, sites, or torrents. Buran has been spotted using the IQY file attachment method, as well. When opened, these Microsoft Excel Web Query attachments execute a remote command. That command proceeds to install the ransomware onto the machine. In case you're unsure of what IQY files are, they are Excel Web Query documents. When you open such a document, it attempts to import data into a worksheet using external sources. Always be wary and cautious in doing so. Diligence prevents you from unwittingly inviting infections into your PC. In the end, using caution can save you a ton of trouble and the aggravation of potentially having to restore your system due to lost data.
German Companies Fall Victim to Buran Ransomware Attacks
In October 2019, reports came out that a myriad of German organizations became targets of a distribution campaign for Buran. They fell victim to a spam campaign that used an eFax lure, in addition to a malicious Word document. The ransom note was translated in German to accommodate the location.
The spam email these organizations received, used to initially spread the ransomware, contained links to a PHP page. That page then served the malicious Word documents, which would, afterwords, download the Buran threat. This use of hyperlinks, instead of attachments, indicates that the people that started the malicious campaign tried to avoid detection by malware scanners (scanners are usually set up to block spam emails).
The specific targeting of German companies is only one example that adds evidence to the idea that Buran is not an infection distributed in a hyper-targeted manner. It's adapted to the needs and desires of the affiliates behind each campaign. The malware is used in a way that has earned the name 'commodity malware.' That only means that its development is not reliant on a particular target. Targets do not mold it, but rather Buran molds it to fit the targets.
What to Expect from a Buran Ransomware Strike
After Buran ransomware initiates its attack on your PC, there are a few things you can expect to happen. The ransomware blacklists an array of files and folders. There's a purpose to its actions - the infection wants to ensure that it can perform as its creators expect, without breaking its functionality. Before it's recognized as a threat, Buran makes it a priority to encrypt the drive letters and folders.
As soon as Buran ransomware slithers its way into your system, it uses strong encryption algorithms to lock your data. It renders the targeted files inaccessible. Pictures, documents, archives, videos. Your files get renamed. The ransomware attaches your unique ID to the back of each file, and you find your files have a bunch of newly-appended numbers stuck to them. An example would be the file name 'sample.jpg' turning into 'sample.jpg.48E7EE9F-3B50-B177-0614-DF09178EE722.'
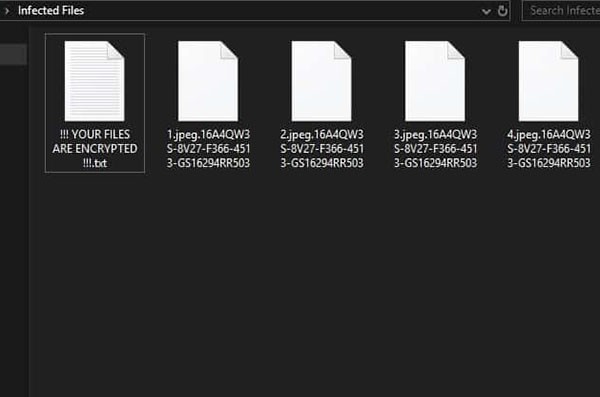
Example of renamed files after Buran ransomware encrypts them.
Once it finishes the encryption process, Buran leaves you the ransom note. It's a file called ''!!! ALL YOUR FILES ARE ENCRYPTED !!!.TXT.'' You can discover it in each folder that contains the locked files, as well as on your Desktop. There are a few ransom notes that victims of the attack have reported, and they have slight variations between them.
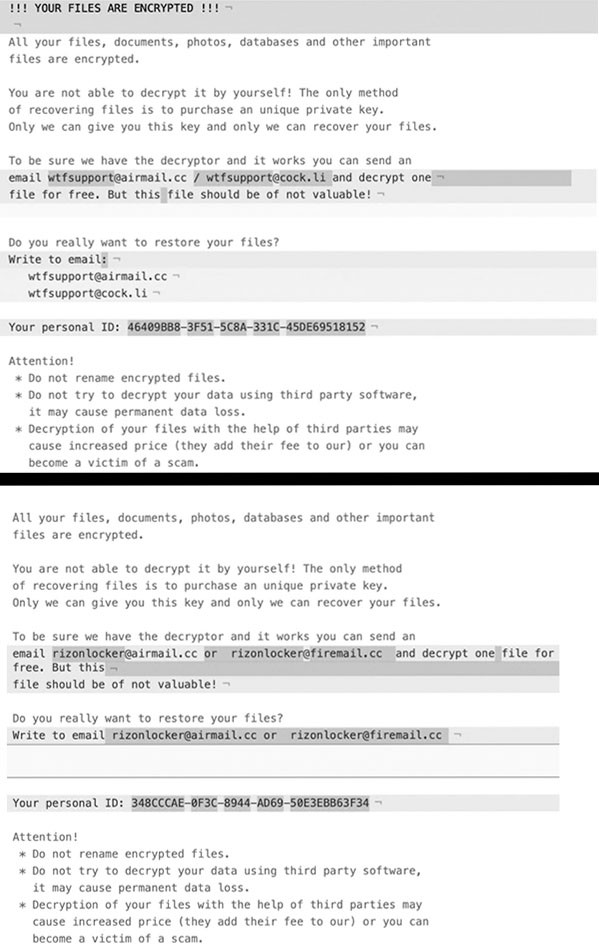
Example of the deviations between Buran's two ransom notes.
Text contents of a Buran ransom note:
| !!! YOUR FILES ARE ENCRYPTED !!! All your files, documents, photos, databases and other important files are encrypted. You are not able to decrypt it by yourself! The only method of recovering files is to purchase an unique private key. Only we can give you this key and only we can recover your files. To be sure we have the decryptor and it works you can send an email polssh1@protonmail.com and decrypt one file for free. But this file should be of not valuable! Do you really want to restore your files? Write to email polssh1@protonmail.com, polssh@protonmail.com, BhatMaker@protonmail.com, BhatMaker@tutanota.com, stopcrypt@cock.email, decryptor@cock.email, sofiasqhwells0gw@gmail.com, harveyjq9freemannl1@gmail.com Your personal ID: - Attention! * Do not rename encrypted files. * Do not try to decrypt your data using third party software, it may cause permanent data loss. * Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam. |
The note states that unless you pay up, your files will remain lost to you. That's because Buran creates a unique decryption key for each victim, and stores it on remote servers, where you, the victim, cannot access it. Buran does its best to back you into a corner with one remaining option – compliance. Supposedly, once you pay the ransom, you'll receive the key you need to decrypt everything. The thing is, with most, if not all, ransomware proves to be a con and may never relinquish the files. The infection fills your ears with what you want to hear and hopes you fall for it. Make sure you don't!
The exact ransom amount is not specified but it is presumed that it's around $500 and $1500, which is expected to be paid in some type of digital currency (Bitcoin, Monero, Ethereum, and so on). Despite Buran's promises, payment will prove futile. You're dealing with scammers – malicious cybercriminals, who prey on your naivety in hopes of making a quick buck. Don't fall victim to the trap they lay for you. Don't get scammed into payment. The only refuge you may have is a system backup of your files and particular antimalware resources to eliminate the threat in an effort to save and recover as much accessible data as you can.








