Ransomware Operators Can Now Steal Your Data Before Encrypting It

Ransomware has proven time and again to be one of the most powerful weapons in the cybercriminals' arsenal. Initially, hackers would need to create their own family of file-encrypting malware, which isn't exactly a walk in the park, but right now, renting or downloading free-to-use strains is easy. Most users are still not fully aware of the dangers that lurk around every corner of the internet, which means that the infection rates are usually pretty good, and the same lack of awareness means that many don't keep regular backups of their files which, in turn, has a positive effect on the balance in the crooks' cryptocurrency wallets.
It's a tried and tested business model that has worked for many. This doesn't mean that the threat isn't evolving, though. Far from it, in fact.
In the past, ransomware was used mostly in spray-and-pray campaigns primarily targeted at home users. In recent months, however, the cybercriminals have realized that the profits from hitting large organizations could be bigger, and the focus has shifted somewhat. Cybersecurity experts have now spotted another, more worrying trend.
Table of Contents
Zeppelin ransomware steals organizations’ data before encrypting it
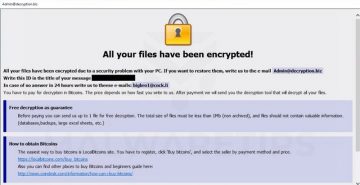
In early December, Morphisec researchers witnessed an attack on a customer of theirs working in the real estate sector. After a closer investigation, they realized that the hackers were trying to infect the company with the Zeppelin ransomware, the latest version of the VegaLocker ransomware-as-a-service family. The attackers were exploiting a remote desktop application by the name of ConnectWise Control (f.k.a. ScreenConnect), and in general, there was nothing too unusual about the infection chain.
The researchers noticed, however, that once it found itself on one of the victim's Windows database servers, the ransomware tried to create a copy of the data and then send it to the crooks' Command & Control (C&C) server. After that, it tried to propagate further down the network, and it finally deployed the file-encrypting module.
In other words, the Zeppelin ransomware tried to steal the company's data before locking it and holding it for ransom. According to ZDNet's Catalin Cimpanu, this is far from the only ransomware strain to employ such tactics. He said that attackers using the Maze, REvil, and Snatch ransomware samples have also engaged in similar activities. But why have they suddenly decided that this is a good idea?
A more reliable restore mechanism
If you think about it, for hackers, stealing the files before encrypting them and demanding a ransom makes a lot of sense. They do indeed run the risk of raising suspicion while trying to exfiltrated a lot of data, but the likelihood of getting caught usually isn't that high. And when you take a look at the advantages the additional step brings, you'll even start to wonder why they didn't think of it earlier.
In a regular ransomware attack, when the victim decides to pay the ransom, they send bitcoins to the crooks' wallet, and in return, they expect a program that decrypts the locked files. In some cases, the crooks just take the money and run, but there are plenty of ransomware operators that do have the genuine intention to give victims their data back once they've received the payment. They do need to write their own decryptors, though, and unfortunately, they sometimes make mistakes.
We've heard plenty of stories of people who have lost data despite paying the ransom because of a faulty decryption tool. The users are the ones who lose money and data, but the impact is also negative for the crooks, who don't end up looking very trustworthy and are therefore less likely to get paid by future victims.
If the hackers have a copy of the unencrypted data, however, they can simply send it back to the victims after the payment and ensure that things will get back to normal relatively painlessly.
Mind you, if the victim has a backup, all this would be pointless. Unless, of course, the hackers threaten to leak the data if the ransom isn't paid.
More blackmail leverage
As we mentioned already, often, the targets are large organizations. Hackers can't steal holiday photos or embarrassing selfies from them, but they can exfiltrate trade secrets and other extremely valuable information. And when the attacked company says that it won't pay because it has backups, the crooks can easily threaten it to leak all the sensitive data.
According to ZDNet's report, ransomware operators have already used the stolen databases as a second extortion point, and the crooks running the Maze ransomware have even created a website in which they list all companies that refused to pay the ransom and subsequently had their data exposed by the group.
It must be said that not all hacking crews are capable of pulling off such a destructive attack. If they want to steal and encrypt information from many different users or companies, they will need a large C&C infrastructure, which could be expensive to set up and maintain. Those who manage to come up with the correct setup, however, will have a definite advantage.