Ryuk Ransomware Creates Chaos: Targets Government and Hospital Institutions

Table of Contents
A Deep Look into Ryuk Ransomware
Ryuk ransomware is an advanced computer threat that has been leveraged in ways to infiltrate systems and specifically target government institutions and hospitals. Some may recognize the name from a popular Japanese manga. Be warned that it has nothing to do with said manga but its name.
After Ryuk ransomware strikes, you find all your files with an added ".ryk" extension. Once it's in place, your data becomes unusable. The infection locks your files with the help of RSA (asymmetric) and AES (symmetric) encryption algorithms. As soon as your data gets encrypted, you discover a ransom note on your Desktop. It also appears in each folder that contains locked data. It's called RyukReadMe, and it's either a ".html" or ".txt" file. The exact ransom message you get depends on the type of victim you are. To elaborate, Ryuk leaves different messages for companies or similar authorities (healthcare institutions, governments, and so on). The two different notes are as follows:
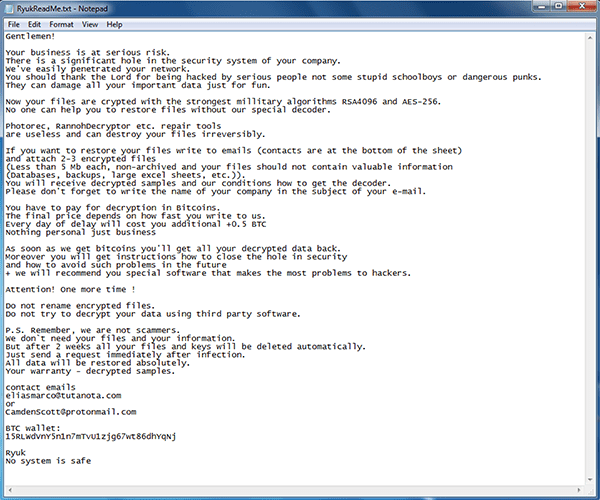

You face a difficult choice. You must decide whether to trust the reliability of cyber extortionists and pay the ransom. Or, not to do so, and forsake your files. Experts urge you to pick the latter. Always remember you're dealing with cybercriminals, and they can't be trusted.
Ryuk Ransomware Outbreaks
Ryuk has claimed an impressive list of victims in its relatively short lifespan. It was first discovered in August 2018, and in 2019, it accounted for over 18% of ransomware attacks.
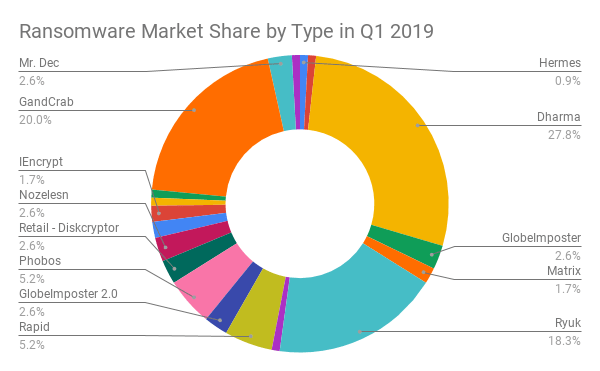
Ryuk's share of the ransomware market in 2019 - Source: Coveware.com.
Below is a list of some of Ryuk's targets:
- Riviera Beach (May 2019)
- Lake City (June 2019)
- Tampa Radio (June 2019)
- Georgia Courts (June 2019)
- La Porte County (July 2019)
- Syracuse School (July 2019)
- Onondaga County Library (July 2019)
- Butler County Library (July 2019)
- Collierville, TN infected (July 2019)
- Henry County, GA (July 2019)
- Lawrenceville, GA police department (July 2019)
From the Riviera Beach attack, it got $600,000. The Lake City one brought in $460,000, and La Porte – $130,000. The exact ransom amount, the threat demands, varies between victims. It has been estimated that, so far, Ryuk has made demands for payments close to $300 million.
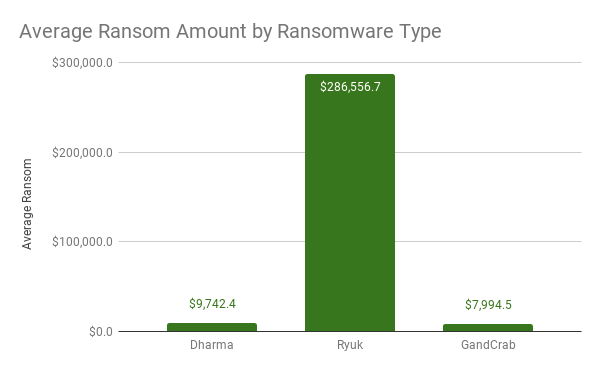
Ryuk surges above other well-known ransomware threats with its astounding ransom demands - Source: Coveware.com.
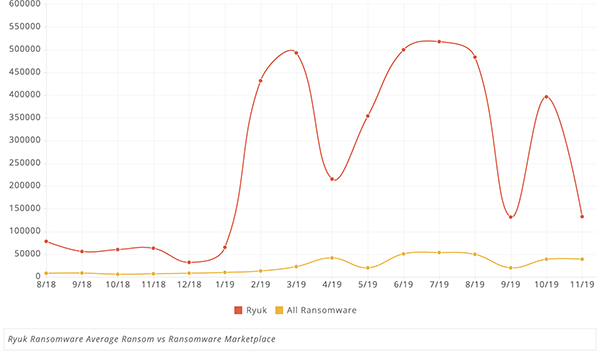
Ryuk Ransomware Average Ransom compared to Ransomware Marketplace - Source: Coveware.com.
When it comes to ransomware, ransom payment doesn't always equal data decryption. Most similar threats tend not to follow through on their promises to send you the decryption key upon receiving your money. According to cyber researchers, Ryuk tends to be more reliable in that sense than other such infections. In 88% of cases, payment leads to successful decryption.
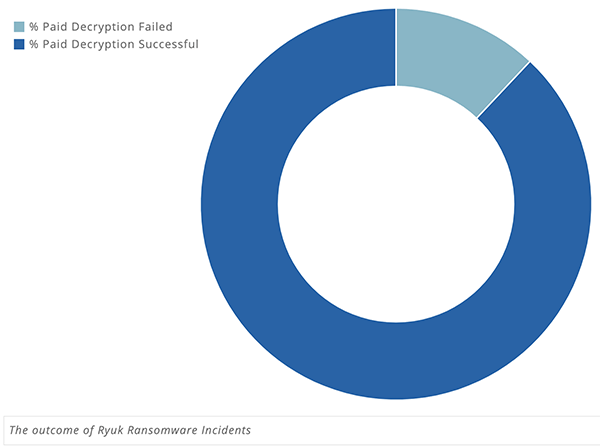
The outcome of 'Ryuk ransomware' - Source: Coveware.com.
Ryuk Hacked 80,000 Computers in 110 Nursing Homes and Hospitals in the U.S.
The Ryuk cyber plague was launched by Russian hackers. On November 17, 2019, the cloud hosting company Virtual Care Provider Inc. (VCPI), based in Milwaukee, Wisconsin, became a victim of the ransomware. That attack wrought terrible consequences. According to a representative from Virtual Care Provider Inc., the attack on them resulted in the corruption of over 80,000 computers. And, 110 hospitals and nursing homes were crippled, and couldn't provide adequate patient care.
Fundamentally, the systems attacked by Ryuk at several nursing homes and hospitals left lives hanging in the balance. The attack reached across 45 states and, at the time, halted the ability for those facilities to care for their clients and patients. Fortunately, for some of the facilities, they had the money on hand to pay the ransom demands, but others look to have lost some of their critical data.
How Did Ryuk Ransomware Make Its Way into the Company Servers?
Ryuk ransomware used deception and finesse to invade the servers. It took the hackers months of sending phishing emails to employees. The emails contained malicious attachments, and by clicking them, the employees offered the ransomware a way into the company's internal servers. It allowed the Russian hackers to seize control bit-by-bit.
That's a strategy Ryuk often turns to – phishing emails. Another one involves the use of Remote Desktop Protocol access. Companies that allow employees to access their networks through remote access, without taking the proper protections, are more prone to attacks from threats like Ryuk.
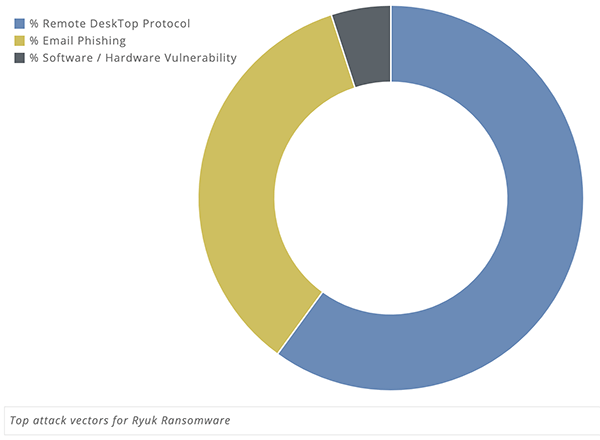
Ryuk Ransomware Common Attack Vectors - Source: Coveware.com.
The Ryuk dropper contains both 32-bit and 64-bit payloads. It chooses which one to use, depending on the targeted system. Before dropping the payload, it also checks the version of the operating system and then acts in accordance.
Once inside, the threat terminates and disables a variety of processes and services. These are usually contained on a predefined list, and tend to be in the realm of antivirus tools, databases, backups, and other software.
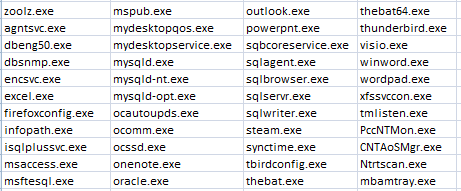
List of services disabled by the Ryuk ransomware - source: Zscaler.com.
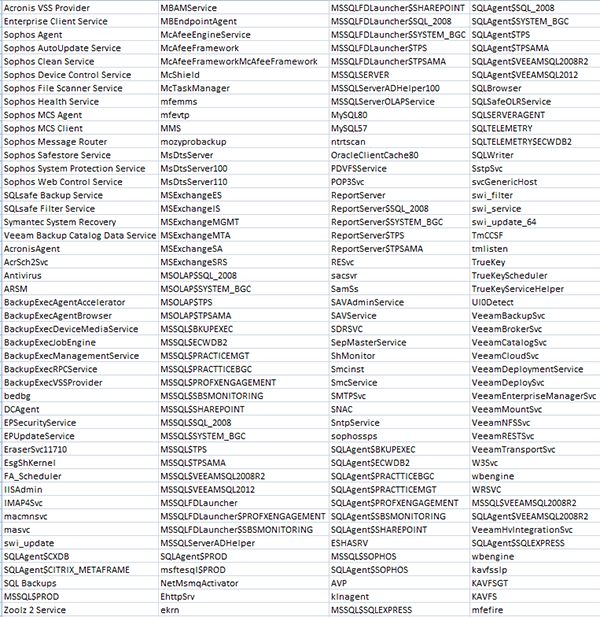
List of processes terminated by the Ryuk ransomware - source: Zscaler.com.
Patients Left Uncared for Because of Ryuk Ransomware
The ransomware attacked the cloud data hosting company, which stores the hospital's servers. The data hosting company encrypts all the data, which includes medical records and medication administration data. After Ryuk ransomware took control of the company's servers, VCPI was unable to access patient records, billing data, email and phone systems, payroll operations, and even basic Internet service. The cyber kidnappers demanded a $14 million ransom. Since that price was too steep for VCPI, they didn't pay up. That led to countless patients not getting the care they needed. Ryuk ransomware effectively endangered the lives of numerous people.
A private security company, called Prosegur, also fell victim to Ryuk ransomware. The infection's attack led to the firm's websites being taken offline in multiple regions. Because of the ransomware, security alarms aren't working! Prosegur customers have taken to Twitter to share that their alarms aren't working, and they don't feel safe in their homes anymore. They have Ryuk ransomware to thank for that.
Experts believe that Ryuk ransomware's objective is not to steal data per se, but rather to disable infrastructure, more specifically servers, and create a carfuffle. According to reports from the Netherlands' National Cyber Security Center, Ryuk ransomware has attacked around 1,800 large organizations around the world. Ryuk ransomware has a "type" of a preferred victim. The cybercriminals behind it tend to use to carry out attacks on government, education, and healthcare institutions, institutions that deal with the distribution of energy, water, utilities – industries in fields like construction, chemical, healthcare, food, entertainment, and critical infrastructure.
In March 2019, a County in Georgia, USA, was taken for $400,000 by Ryuk ransomware. The ransomware locked their data, and demanded the steep ransom amount, as ransomware threats commonly do. Since they didn't have backups, they complied and paid up. Thankfully, the County received the proper decryption key and managed to gain back all their data. However, that's not the case with most other ransomware attacks. Usually, it doesn't matter if you pay or not. That's why experts advise against compliance and recommend that you always backup your data and utilize the necessary antimalware resources to help eliminate ransomware attacks.





