As Fears of the Coronavirus Pandemic Spread, So Does COVID-19-Themed Malware

In these turbulent times, people are living in fear. It's a time of crisis as the cases of Coronavirus increase, and healthcare systems collapse one after the other. Many are afraid for their lives, and the lives of everyone they love. Most are merely trying to survive and move past the pandemic, while others see an opportunity. Cybercriminals have been exploiting the Coronavirus pandemic for months now, most recently with COVID-19-themed malware.
Malicious hackers prey on people's fears and unleash a plethora of COVID-19-related malware. A myriad of phishing scams, malicious emails, and fraudulent sites promise accurate, up-to-date information connected to Coronavirus – spreading, victims, quarantines, and so on. And, since people feverishly consume all news regarding COVID-19, they click the link, download the attachment, open the document, and, in doing so, fall prey to malicious individuals.
These cybercriminals push an agenda of infecting as many machines as possible by any means necessary. That's why, in a time of а global pandemic, they are not only fine with using COVID-19 as a way into your systems, but seem to be excelling at it. They're trying to flood your system with infections – ransomware, Trojans, malware of all sorts. And, that's all in an attempt to steal financial and personal information. Then, once these malicious individuals get a hold of it, they can either exploit it for themselves or pawn it off on the dark web.
Table of Contents
The COVID-19 phishing scam
Among the latest shams to hit the web, you find the COVID-19 phishing scam. It's a social engineering one that preys on people's lust for knowledge regarding the infectious outbreak.
Phishing scams are a pretty common technique for cyber attacks. You receive an email that appears legitimate but isn't, and you get baited into opening it, and following the instructions it provides – opening a link or a document, downloading an attachment, and so on. COVID-19 is the lure that gets you, hook line and sinker.
Phishing scams playing on COVID-19-related news have been going around for months now. They surged around January 2020, and have been increasing ever since. Organizations like the World Health Organization (WHO) and the US Centers for Disease Control and Prevention (CDC) are prime targets for impersonation in such emails, documents, maps, et cetera. Cybercriminals use their logos and data (documentation or infection maps) and pass them along to their targets, corrupted and malware-ridden.
In February 2020, in a well-known cybercrime forum called XSS, full of Russian-speaking cybercriminals, the newly-crafted COVID-19-themed phishing scheme got advertised. The hacker behind the advertisement shared the infiltration method – an email attachment, disguised as a distribution map of the virus's outbreak. The map claimed to contain real-time data from WHO. Of course, it was NOT a real map but an impersonation of an actual one – one by the Johns Hopkins Center for Systems Science and Engineering (CSSE). That bogus map was to get used as means to deliver the malware into the targeted systems. The cyber attacker behind the post shared prices, as well. You can purchase the offer for $200 if you wish a 'private build,' and for $700 if you also need a Java CodeSign certificate. If you do need such a license, the hacker will allow you to use theirs, which is why the price spikes as much as it does.
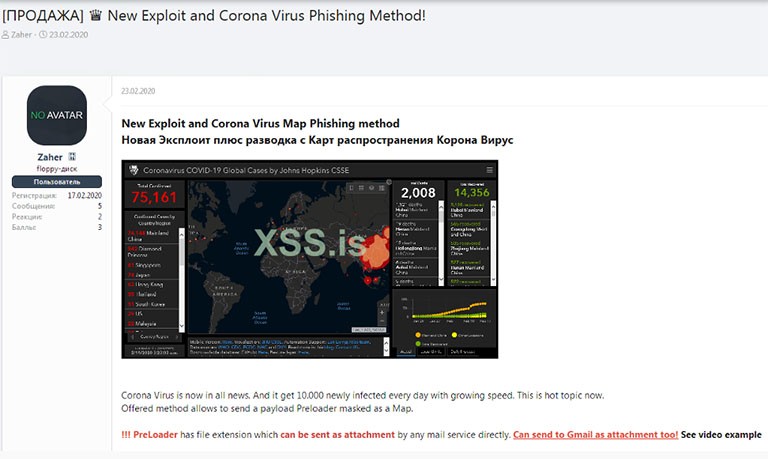
XSS post advertising the sale of the COVID-19-related phishing scam. Source: digitalshadows.com
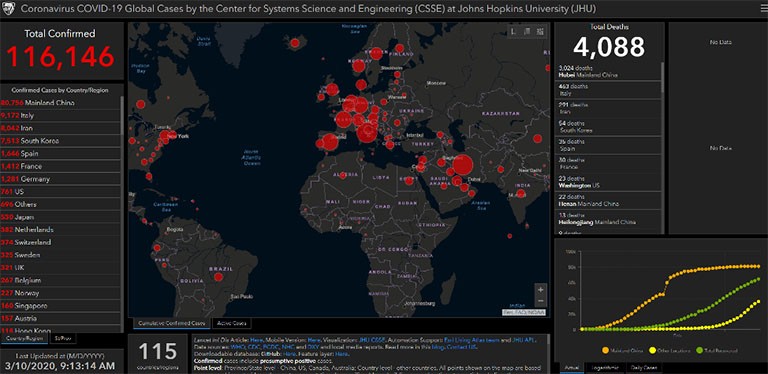
The legitimate Johns Hopkins COVID-19 distribution map, the hacker, impersonates for the scam. Source: digitalshadows.com
COVID-19 infection kit for sale – what is it?
As mentioned, the COVID-19 map carrying malware got advertised on a Russian cybercrime forum. The weaponized map appeared to infect its targets with a variant of AZORult. AZORult is a dangerous and harmful malware, whose primary objective is to steal information for later exploitation.
The malicious map appears as a live and interactive one. It's part of an infection kit, which got designed for a Java-based malware deployment operation. If you browse through the thread below the sales offer, you'll see an array of claims made by the seller. Supposedly, the attacker's malware payload can get bundled with the Java-based map into a filename in a way that would ensure most Webmail providers permit the message to reach its target successfully.
The map initially got discovered on a domain called www.Corona-Virus-Map[.]com. It has the appearance of a legitimate and convincing helpful tool, but it is NOT. It shows an image of the world and displays all the viral outbreaks with red dots. They differ in size, depending on the number of infected cases. Not only that, but it also tallies all the confirmed cases, recoveries, and deaths by country and city. And, if that seems like a lot of work for a bogus map, in reality, it got ripped off by the actual legitimate map offered by Johns Hopkins University's Center for Systems Science and Engineering.
The malware itself appears to be within a file called corona.exe and carries some standard AZORult functionalities. It can steal all manner of information: cookies, IP addresses, credit card/s and bank account/s data, search history, and clicks. As if that's not bad enough, reports have come in that the infection also seeks out cryptocurrency wallets, including ones for Electrum and Ethereum, as well as Steam accounts and the Telegram desktop application. The malware can take screenshots without getting authorization to do so, and collect all manner of data related to your Operating System – architecture, hostname, and username.
Apart from getting a hold of that information, the malicious software can also exfiltrate it to a command-and-control (C&C) server. As soon as the person behind the attack gets that information in their hands, they can use it as they see fit.
The malicious tool makes researching it a difficult feat since it uses several layers of packing, and a multi-sub-process technique on top of that, too.
What is a phishing email?
As briefly mentioned, a phishing email is one that tries to bait you into unknowingly acting against your better interest and, in the process, to unwittingly invite malware into your PC. So far, malware researchers have spotted infections like Lokibot, TrickBot, and AgentTesla getting distributed via this method.
You receive an email that bodes the name of a well-known sender. The list of most commonly used names used to include the likes of Amazon, DHL, and PayPal. Nowadays, there's a shift – healthcare providers, government officials, et cetera. The email usually boasts a subject-line aimed to reel you in and lure you into opening it. Understand that these emails get crafted and modified per each target. American targets may get an email pretending to come from WHO with a tag-line 'What to do in time of a pandemic' that instructs you to download a Word document with detailed instructions. If you do, you've fallen victim to the scam, and without knowing it, invited malware into your machine. You must be wary. Do your best to stay level-headed, and don't give in to panic. Cybercriminals exploit the fear-frenzy, so try not to give into it. Examine emails and senders with grave caution before opening them, and especially, before clicking or downloading anything they contain.
The power of misinformation
The Internet has become a whirlwind of inaccurate information about Coronavirus. Users are drowning in sensationalist news, trying to determine what they can believe and what they should disregard. Despite the best efforts of several major organizations, misinformation keeps spreading like wildfire.
In an attempt to combat that spread and help users from allowing malware into their machines on accident, at least to some extent, official government entities have begun taking steps – they release press releases, make speeches, and even turn to social media. Below is a Facebook post by an Australian Member of Parliament denouncing a social media post that tried to impersonate the Australian Department of Health.
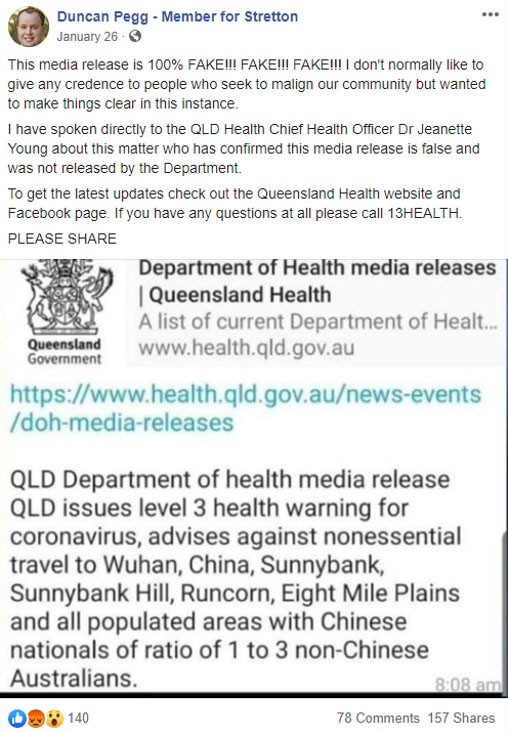
Australian MP's post that's combating the spread of misinformation. Source: www.digitalshadows.com
Since January 2020, over 1,400 COVID-19-related domains have gotten registered. You can see the significant spike in registration depicted in the chart below. Although it's fair to say that at least some of them may get used for legitimate purposes, it should get noted that many of them will not.
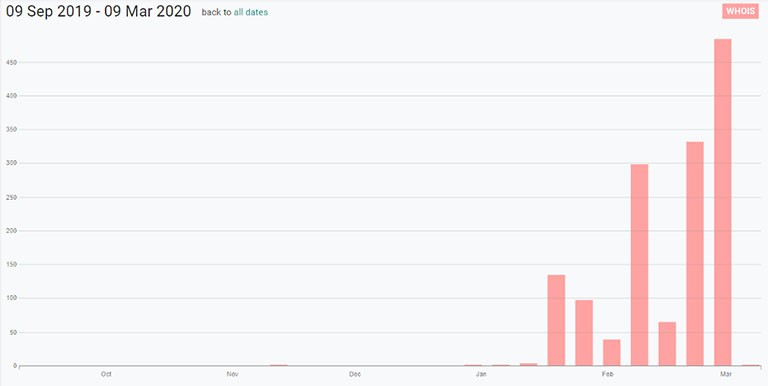
COVID-19-related domains registered since January. Source: www.digitalshadows.com
Malicious domains help cybercriminals show credence to their claims. They can use them to spread all manner of misinformation, impersonate legitimate brands, host phishing pages, and so on. The list of possibilities, these malicious individuals can benefit from, in this time of crisis is extensive. The UK's National Fraud Intelligence Bureau (NFIB) reported that only in March 2020, there have been over twenty-one cases of COVID-19-related fraudulent scams. These twenty-one schemes resulted in losses of over £800,000 in the United Kingdom alone.
Remember that cybercriminals look at this pandemic as nothing more than an opportunity for a quick cash-grab. Do your best to remain vigilant. Don't give in to the frenzy – be cautious but not panicked. Vigilance can save you an array of trouble.







