Russian Hackers Spread VegaLocker Ransomware with Mass Malvertising Campaigns

VegaLocker is known as a ransomware threat that was first noticed on February 11, 2019, when it hit the web and claimed its first cyber victims. At the time, no one could have predicted it would prove to be such a persistent threat. The malicious infection not only survived but thrived as it gave birth to an array of code variations. Because of VegaLocker, so far, web users have been hit with the ransomware threats Jumper (Jamper), Buran, and Zeppelin. These infections came to be because of VegaLocker's code.
The cybercriminals behind the original threat kept modifying it, making improvements, giving it different names, so it can continue to plague Internet users. Due to these modifications, the VegaLocker ransomware is proving difficult to deal with for security experts. As soon as they come up with a method to fight the dreadful infection, it gets updates and "evolves" and continues to infect system after system. VegaLocker is ever-changing and improving its code. It's continually modifying its performance. And, every time a malware expert gets too close to tackling the threat, the hackers behind it update and improve. And, if the need comes to be, rebrand. After all, that's how Jumper (Jamper), Buran, and Zeppelin came to be.
Table of Contents
An analysis of VegaLocker
The hackers behind the ransomware have programmed it in the Delphi language. That in itself provides an obstacle for tackling the VegaLocker threat – it's tough to reverse-engineer that language.
The infection is a fusion of different viruses. It contains elements from an array of various threats. For example, in the VegaLocker code, there was found residual code from the Scarab ransomware family. Source code was shared with notorious infections, like Amnesia and Gloverabe2. This discovery can mean one of two things: either the same people who created those threats created VegaLocker using the same code as a base, and plan to use it for themselves, or they crafted the VegaLocker ransomware as a custom order for different hackers.
How did VegaLocker slither into your system?
Security researchers have performed analysis on the threat, and have found that it starts with a security bypass module. That module makes sure to scan the local system for any sign of security programs and engines, anything that can block the normal VegaLocker execution.
It looks for signatures of the following engines:
| Habbo, Rebhip, The Qt Company Ltd, Microsoft Corporation, Delphi Libraries, SMART INSTALL MAKER, InnoSetup, James Jackson-South, Microsoft Visual C/C++ Libraries, libczmq3, Adobe Systems Incorporated, Mercury Interactive, NSIS, Splinterware Software Solutions and StockSharp LLC. |
If it finds anything it deems troublesome, it disables or removes it. Once it completes that first step, it proceeds to deal with boot options modifications. VegaLocker reconfigures the operating system's configuration files and makes it, so the virus file starts as soon as the machine is powered. To solidify its grip over the boot options, it disables access to the recovery boot options and menus. That hinders the user's attempts at manual recovery guides.
VegaLocker doesn't stop with just disabling access. It also removes crucial data from your system. It targets data used by the operating system – Backups, System restore points, Shadow Volume Copies. VegaLocker is quite thorough in removing anything it deems can prove an obstacle in its attack.
The notorious infection evades detection at any cost – sometimes even at the price of self-deletion. The ransomware follows programming to evade virtual machine hosts. How? It regularly monitors the machine's running processes, looking for a sign of strings related to hypervisors or guest additions. Should it find any, it stops or even deletes itself from the machine.
VegaLocker can not only encrypt your data but even extract it, as well! It can acquire personal and financial information and then use it for nefarious purposes – identity theft, financial abuse, blackmail. The ransomware also meddles with a variety of system settings. It modifies your Windows Registry, and creates entries for itself or modifies the already existing ones. That meddling leads to your system's performance deteriorating. You suffer lag, errors, warnings, and alert pop-ups. The ransomware's usual M.O. is to cause severe issues with your system's performance. That way, your machine becomes close to unusable for as long as the infection remains on board.
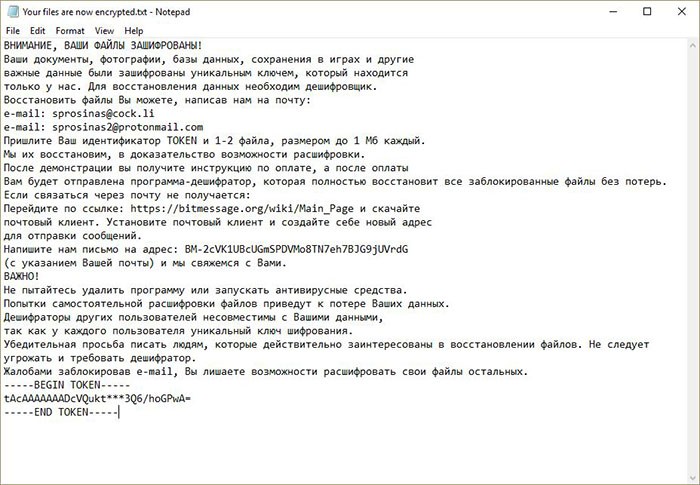
Image of VegaLocker Ransomware ransom note text file
VegaLocker's meddling on infected systems is rather vast. The ransomware engine searches for an active remote desktop configuration service. If one such file has already been made, the ransomware accesses it and edits it. It adds credentials, which the hackers can then use. That's not a step all ransomware threats take. Only advanced ones, like VegaLocker, are known to do it and then exploit it. They can install more malicious threats on your computer, like Trojans. Or, they can even allow a cryptocurrency miner on your machine, and not only extort you for money but make money off of your computer's resources, as well. The miner can come in a myriad of forms, like code attached to other files, or a stand-alone application. As soon as you execute or enact it, you'll feel the consequences of its stay. It takes a toll on components like the memory, CPU or GPU, and hard disk space.
Security experts have deduced that VegaLocker's primary distribution technique involves the use of malvertising campaigns. That's the easiest way for mass distribution with minimal effort. The hackers behind the infection unleash a myriad of malicious spam emails that contain a link you get asked to click, or an attachment you get invited to download. If you fall for these tactics, you end up with the nasty cyber threat on board.
Naturally, there’s more than one method of invasion the ransomware can resort to. It can also sneak in through infected application installers. The cybercriminals choose popular software that generates a lot of downloads by users. Then, they embed the installation scripts in the setup files of said software. They manage that trickery by taking the original files from the software vendors and then making their malicious addition.
Another viable option for infiltration is through infected documents – spreadsheets, presentations, databases, and so on. The installation code of the ransomware becomes part of the macros that are inserted in them. Then, once a document gets opened, a message pops up that asks for it to be enabled. If you do, you've got yourself the VegaLocker ransomware on your hands.
VegaLocker can also weasel its way in via fake user profiles. With the ever-increasing use of social media, that proves quite an effective invasive method. Posts on community forums, direct messages sent to a mass of people, and the profiles used for that can either be fake or real ones that got hacked. Always be wary when you see on your screen a link with the message, "click it." Vigilance is your friend.
What happens once VegaLocker invades?
As soon as the ransomware enters your system, it strikes. It carries out its attack using strong encryption algorithms. It has a built-in target list of extensions to lock.
- Backups
- Archives
- Databases
- Images
- Music
- Videos
List of file type extensions VegaLocker targets
If you think you'll have files of importance that will manage to avoid encryption, you're wrong. The ransomware's target list is extensive.
| .jpg, .jpeg, .raw, .tif, .gif, .png, .bmp, .3dm, .max, .accdb, .db, .dbf, .mdb, .pdb, .sql, .dwg, .dxf, .cpp, .cs, .h, .php, .asp, .rb, .java, .jar, .class, .py, .js, .aaf, .aep, .aepx, .plb, .prel, .prproj, .aet, .ppj, .psd, .indd, .indl, .indt, .indb, .inx, .idml, .pmd, .xqx, .xqx, .ai, .eps, .ps, .svg, .swf, .fla, .as3, .as, .txt, .doc, .dot, .docx, .docm, .dotx, .dotm, .docb, .rtf, .wpd, .wps, .msg, .pdf, .xls, .xlt, .xlm, .xlsx, .xlsm, .xltx, .xltm, .xlsb, .xla, .xlam, .xll, .xlw, .ppt, .pot, .pps, .pptx, .pptm, .potx, .potm, .ppam, .ppsx, .ppsm, .sldx, .sldm, .wav, .mp3, .aif, .iff, .m3u, .m4u, .mid, .mpa, .wma, .ra, .avi, .mov, .mp4, .3gp, .mpeg, .3g2, .asf, .asx, .flv, .mpg, .wmv, .vob, .m3u8, .dat, .csv, .efx, .sdf, .vcf, .xml, .ses, .qbw, .qbb, .qbm, .qbi, .qbr , .cnt, .des, .v30, .qbo, .ini, .lgb, .qwc, .qbp, .aif, .qba, .tlg, .qbx, .qby , .1pa, .qpd, .txt, .set, .iif, .nd, .rtp, .tlg, .wav, .qsm, .qss, .qst, .fx0, .fx1, .mx0, .fpx, .fxr, .fim, .ptb, .ai, .pfb, .cgn, .vsd, .cdr, .cmx, .cpt, .csl, .cur, .des, .dsf, .ds4, , .drw, .eps, .ps, .prn, .gif, .pcd, .pct, .pcx, .plt, .rif, .svg, .swf, .tga, .tiff, .psp, .ttf, .wpd, .wpg, .wi, .raw, .wmf, .txt, .cal, .cpx, .shw, .clk, .cdx, .cdt, .fpx, .fmv, .img, .gem, .xcf, .pic, .mac, .met, .pp4, .pp5, .ppf, .nap, .pat, .ps, .prn, .sct, .vsd, .wk3, .wk4, .xpm, .zip, .rar. |
The files VegaLocker ransomware targets in its attack
Once the infection locks your data, it makes its ransom demands. VegaLocker leaves a ransom note on your Desktop, and in every affected folder. It's a text file, called "ABOUT YOUR FILES.TXT" or "Your files are now encrypted.txt."
https://sensorstechforum.com/wp-content/uploads/2019/02/vegalocker-ransomware-image-senesorstechforum-com.jpg
VegaLocker's ransom note, source: sensorstechforum.com.
The text of the ransom note is as follows:
|
ВНИМАНИЕ, ВАШИ ФАЙЛЫ ЗАШИФРОВАНЫ! Ваши документы, фотографии, базы данных, сохранения в играх и другие важные данные были зашифрованы уникальным ключем, который находится только у нас. Для восстановления данных необходим дешифровщик. Восстановить файлы Вы можете, написав нам на почту: * e-mail: sup24@keemail.me, sup24@rape.lol * резервный e-mail: sup24@protonmail.ch, voprosi24@protonmail.ch Пришлите Ваш идентификатор TOKEN и 1-2 файла, размером до 1 Мб каждый. Мы их восстановим, в доказательство возможности расшифровки. После демонстрации вы получите инструкцию по оплате, а после оплаты Вам будет отправлена программа-дешифратор, которая полностью восстановит все заблокированные файлы без потерь. Если связаться через почту не получается: * Перейдите по ссылке: hxxps://bitmessage.org/wiki/Main_Page и скачайте почтовый клиент. Установите почтовый клиент и создайте себе новый адрес для отправки сообщений. * Напишите нам письмо на адрес: BM-2cVK1UBcUGmSPDVMo8TN7eh7BJG9jUVrdG (с указанием Вашей почты) и мы свяжемся с Вами. ВАЖНО! * Расшифровка гарантируется, если Вы свяжетесь с нами в течении 72 часов. * Выключение или перезагрузка компьютера может привести к потере Ваших файлов. * Не пытайтесь удалить программу или запускать антивирусные средства. * Попытки самостоятельной расшифровки файлов приведут к потере Ваших данных. * Дешифраторы других пользователей несовместимы с Вашими данными, так как у каждого пользователя уникальный ключ шифрования. Убедительная просьба писать людям, которые действительно заинтересованы в восстановлении файлов. Не следует угрожать и требовать дешифратор. Жалобами заблокировав e-mail, Вы лишаете возможности расшифровать свои файлы остальных. -----BEGIN TOKEN----- - -----END TOKEN----- |
As you can see, the note is in Russian. That hints at the ransomware creators possible Russian descent or the very least that Russian-speaking countries are their prime target.
The English translation is as follows:
|
ATTENTION, YOUR FILES ARE ENCRYPTED! Your documents, photos, databases, game saves and other important data was encrypted with a unique key that we have. To restore data, you need a decryptor. You can restore files by writing us to email: e-mail: sprosinas@cock.li e-mail: sprosinas2@protonmail.com Send us your ID token and 1-2 files, the size should be no more than 1 MB. We will restore them to prove there is decryption available. After the demonstration, you will receive payment instructions, and after payment you will receive a decryptor program that will restore your files completely without issues. IF you can't reach us via e-mail: Go to the site: https://bitmessage.org/wiki/Main_Page and download the e-mail client. Run the e-mail client and create an address. Send us an e-mail to: BM-2cVK1UBcUGmSPDVMo8TN7eh7BJG9jUVrdG (including your address) and we will contact you. |
Source for translation: www.enigmasoftware.com.
The cyber extortionists state that the only way to rid yourself of the encryption is with a unique key. A key, which is different for each victim, and is stored on a remote server. Therefore, the only way to get your hands on it is to comply, pay the ransom, and hope these people keep their word and send it to you. But you have no guarantees that they will. After all, they're malicious data kidnappers, extorting you for money. Why would they care about you after they get your money?
The exact ransom amount that VegaLocker demands is yet unknown. To know it, you must contact the hackers via email, and they'll send you one back with more detailed instructions on what you're expected to do. You're even given a deadline to increase the pressure on your decision-making. The cybercriminals threaten to delete your unique decryption key if you don't reach out within the first 72 hours of encryption. Security experts advise against that. Don't reach out, don't comply, and don't pay the ransom. Don't follow their instructions, because the chances of you regaining control over your data are slim, while those of wasting your money, time, and energy dealing with them are substantial.