Shade Ransomware No Longer a Threat: Malicious Actors Shut Down All Operations and Released Over 750K Decryption Keys

Shade ransomware is a dreadful cryptor, which began its invasion back in 2014. Over time, the threat (also known as Troldesh or Encoder.858) began to distribute other malware on affected machines after encrypting the victim's files and demanding payment in exchange for their decryption. It seems that after six years of malicious practice, the Shade ransomware operators have decided to call it quits.
Table of Contents
Cyber Criminals Pull the Plug On Their Shade Malware Operations After Six Years of Malicious Activity
In April, the Shade gang created a GitHub repository where they announced that they've stopped spreading the ransomware at the end of 2019. Their statement explains the suspicious drop rate of victims affected by Shade ransomware in late 2019 and early 2020 (Fig.1), as opposed to previous years.
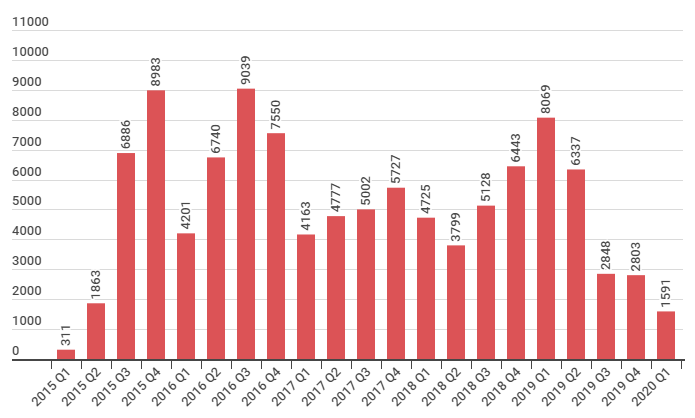
Figure 1: Image shows a sudden decline in Shade ransomware cases that starts from the 3rd quarter of 2019. The drop rate continues throughout the rest of 2019 and the beginning of 2020. Source: Kaspersky
"We are the team which created a trojan-encryptor mostly known as Shade, Troldesh or Encoder.858. In fact, we stopped its distribution in the end of 2019. Now we made a decision to put the last point in this story and to publish all the decryption keys we have (over 750 thousands at all). We are also publishing our decryption soft; we also hope that, having the keys, antivirus companies will issue their own more user-friendly decryption tools. All other data related to our activity (including the source codes of the trojan) was irrevocably destroyed. We apologize to all the victims of the trojan and hope that the keys we published will help them to recover their data," states their post on GitHub.
The Shade Team repository is no longer available, but the screenshot below (Fig.2) will give you an idea of what it looked like before.
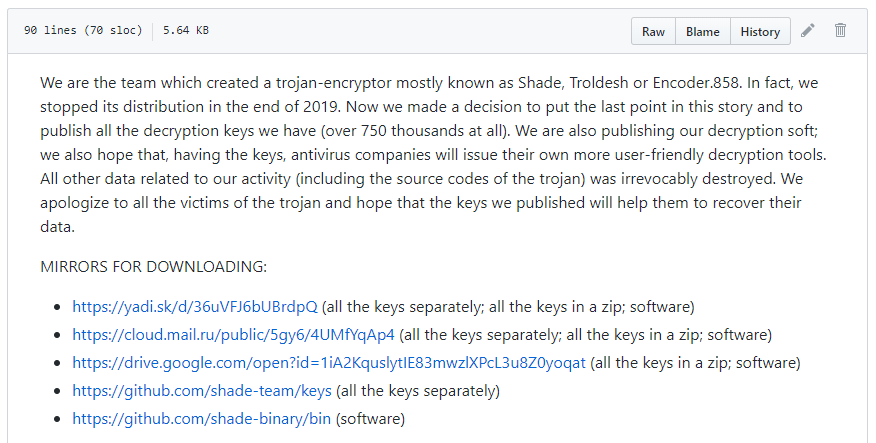
Figure 2: Image shows Shade Team's GitHub repository, which includes a note, decryption key download links, and instructions for file decryption.
Over 750K Decryption Keys Are Available For Shade Victims To Recover Their Lost Data
In their GitHub repository, the Shade gang included five master decryption keys and over 750K individual victim's decryption keys. They also provided links to their decryption software and instructions on how victims can recover their lost data. Unfortunately, as the malicious actors point out themselves, their decryption tool is not user-friendly. Because of this, some cybersecurity companies have started working on decryptor that can simplify the process for all affected users. That being said, every user that was unfortunate to fall victim to this malicious threat can now get their encrypted files back. To do that, simply search for available decryptors from reputable security companies.
Troldesh Ransomware Ranked As The Most Actively Distributed Malware Via Email Campaigns for 2019
According to research made by Group-IB’s Computer Emergency Response Team (CERT-GIB), Shade (Troldesh) ransomware was the most actively distributed threat through malicious email campaigns for the first half of 2019. CERT-GIB claims that during that time, the three of the most widespread tools used in attacks have been Troldesh (53%), RTM(17%), and Pony Formgrabber (6%).
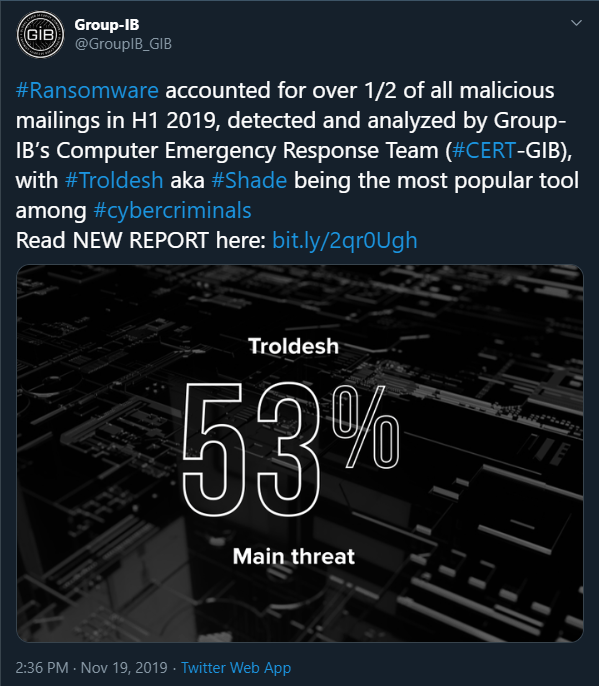
Figure 3: Image shows Group-IB's post on Twitter regarding their research on the most prevalent threat for the first half of 2019. Source: Group-IB
Shade ransomware is a threat known to target European countries like France, Germany, the UK, Italy, Ukraine, and Russia. Researchers report that Russia is the country that has suffered the most significant losses from Shade malware attacks. It appears that 52% of the Shade team's malicious email attachments went to Russian addresses specifically. This information comes as no surprise since most reports support the theory that Shade ransomware started as a Russian-oriented threat spread via spam campaigns.
Once the infection has access to the victim's computer, it will encrypt all valuable files like photos, documents, media files, as well as other data, and attach different extensions to them. Here's a list of known extensions used by Shade ransomware:
- .xtbl
- .ytbl
- .breaking_bad
- .heisenberg
- .better_call_saul
- .los_pollos
- .da_vinci_code
- .magic_software_syndicate
- .windows10
- .windows8
- .no_more_ransom
- .tyson
- .crypted000007
- .crypted000078
- .rsa3072
- .decrypt_it
- .dexter
- .miami_california
After that, Shade will change the desktop background (Fig.4) and drop a README.txt file that serves as a ransom note containing text in two languages – English and Russian.
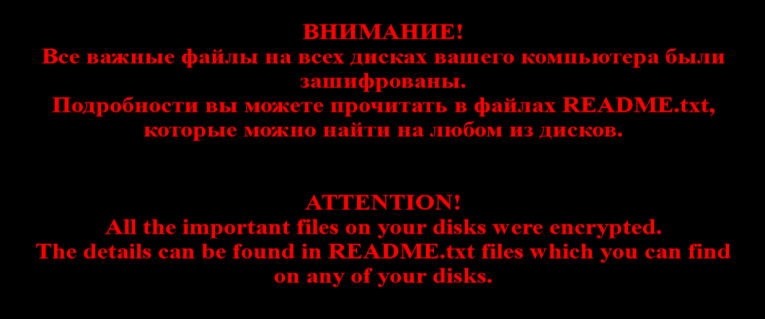
Figure 4: Image shows the wallpaper used by Troldesh (Shade) to replace the desktop background of the victim's computer.
What's interesting about this threat is that it was programmed for more than file encryption. It was discovered that Shade ransomware could be used for cryptocurrency mining, as well as means for generating and increasing online traffic, in order to receive revenue from ad campaigns. As previously mentioned, Troldesh can also act as a 'carrier' for other malicious software. Over time, it began installing a remote administration tool (RAT) on the victim's PC. Another interesting fact is that once the ransomware infiltrates the system, it will scan for a particular type of data, which would indicate that the device is used by Russian accounting departments. If such data is found, the malware will launch a Teamspy Trojan attack, instead of a ransomware one. In addition, Shade will drop modified versions of tools like TeamViewer, 7ZIP, NirCmd, RDP Wrapper, and TeamViewer VPN driver, to change the OS's settings and gain remote access over the computer.
Is This Really the End of Shade Ransomware?
While it was established that the decryption keys are real, some security researchers are not entirely sure that it was the real Shade gang who shared them. After all, decryption keys can be stolen and shared on the internet by someone pretending to be the real Shade operators. For all we know, a rival gang could've done it.
People shouldn't play it safe and rely on the fact that there's decryption software available. Just because users can now recover lost data with available decryption tools, doesn't mean that they are protected. It's best not to interact with spam email messages, especially if they contain file attachments. Also, checking the email credentials of the sender can go a long way. Anyone can claim everything in the Subject Title, and pretend to be a well-known company or organization. However, they cannot use the actual email address of the person or company they're impersonating. The receiver of the message should compare the given address with the legitimate one, before opening the email. If the addresses do not match, it would mean that the message is part of a scam, and the sender is not who they claim to be.








