Updated HawkEye Keylogger Exploits Coronavirus Scare for Profit

The HawkEye keylogger has been making the rounds on the web since 2013. In 2019, there was a newly-released update of the threat – HawkEye Reborn v9. Now it's back on security experts' radars, and it appears to have joined the long list of infections, taking advantage of the Coronavirus panic.
Preying on Coronavirus fears seems to have become the norm when it comes to malware. By now, it's a well-established social-engineering tactic, causing damage in its path. Cybercrooks use all in their power to profit off the horrific COVID-19. They turn to malware attacks, credential-stuffing scams, corrupted URLs, their possibilities seem limitless. That's because people are scared, and in their fear, turn to every source of information in their path. Unfortunately, most of the sources they come across are malicious and run by ill-intentioned cybercrooks.
There's a 40% increase in cyberattacks, as reported by malware researchers. They seem to focus on companies that have allowed their workers to work remotely. Most home computers and laptops don't have the defenses that their office ones provide, which leaves them exposed and at a higher risk of catching malware.
These malicious campaigns have taken their toll globally. As you can see below, people in the UK receive a staggering number of over 41,000 malware and spam attacks. France follows close behind, at almost 24,000 for malware and about 23,000 for spam. The US and Canada still manage to stay below the mark of 20,000, but there are no signs of cybercriminals slowing down with these campaigns, so who could say how long that number will remain low.

Coronavirus-related malware and spam attacks in France and the UK. Source: trendmicro.com

Coronavirus-related malware and spam attacks in the US and Canada. Source: trendmicro.com
Table of Contents
A brief history of the HawkEye keylogger infection
When it first popped up on the scene, the HawkEye keylogger made its way into computers via malvertising campaigns, more precisely, phishing emails. The malware appeared as a first-stage downloader for a cryptocurrency miner – CGMiner. CGMiner is an open-source cryptocurrency miner. The hackers behind the miner could then use it and mine for digital currency (Bitcoin, Monero, and so on) for their gain on someone else's computer. They exploit the victim's system and resources, leaving the victim to deal with the consequences, like lag, while they experience only benefits.
Let's take a closer look at how exactly the infiltration process occurred. The infection sent out its emails that all seemed to revolve around job applications. Every email contained a .zip archive, which, when opened, revealed a job applicant's resume. Or, so it seemed. In reality, when you open the .zip file, it delivers a sample of the HawkEye keylogger straight into your system. Experts consider it a pretty generic attack, but it does the trick.
So far, the malware ticks all the boxes of a standard representative of its category. Sometime after it got unleashed onto unsuspecting web users, its attack shifted tactics. Instead of it getting used for loading cryptocurrency miners, hackers began using HawkEye's most recent variant for espionage.
Once the malware finds itself on your PC, you're vulnerable to espionage. Keyloggers like HawkEye have a reputation for monitoring your activities for malicious purposes. They keep track of everything you do – every keystroke, all the sites you visit, data you input. Let that sink in for a moment. That includes all manner of personal and financial information. Like, passwords, credit card details, bank account information, and so much more. All that sensitive data is within reach of the HawkEye keylogger. And, once the malware deems it has gathered enough, it exfiltrates the data to a command-and-control (C&C) server that the attacker controls.
Malicious cybercriminals used the HawkEye keylogger malware for targeted attacks. Organizations in healthcare, agriculture, marketing, transportation and logistics, import and export, and a slew of other sectors, became prime targets. The attackers would aim at their employees, send them the corrupted emails, and await their chance to invade and strike.
If you wish to avoid getting stuck with a malicious tool, like the HawkEye keylogger, be vigilant. Stay cautious when receiving emails – do your best to examine and verify their authenticity. Be even more careful if they contain attachments or links, which they urge you to download and click. If you're attentive and thorough, it can save you an array of potential grievances.
An updated HawkEye keylogger takes advantage of the Coronavirus scare
There's a new variant of the HawkEye malware, plaguing users. One, attempting to benefit from the fear, surrounding Coronavirus. Among the infection's improvements, you find an expanded information-stealing capability.
The people behind it have a goal – to exploit the current times and the news revolving around the Coronavirus menace. The cybercriminals, using the latest HawkEye variant, prey on people's desire for knowledge on Coronavirus, and its strain COVID-19.
Most malware threats, seeking to benefit from the Coronavic scare, turn to malicious email campaigns to spread their infections. One of the most commonly used subject lines revolves around supposed 'Coronavirus updates.' You can see an example below. The malicious emails often claim to come from a reputable source and display valuable information and' updates.' That is not true. They're bogus and carry malware.
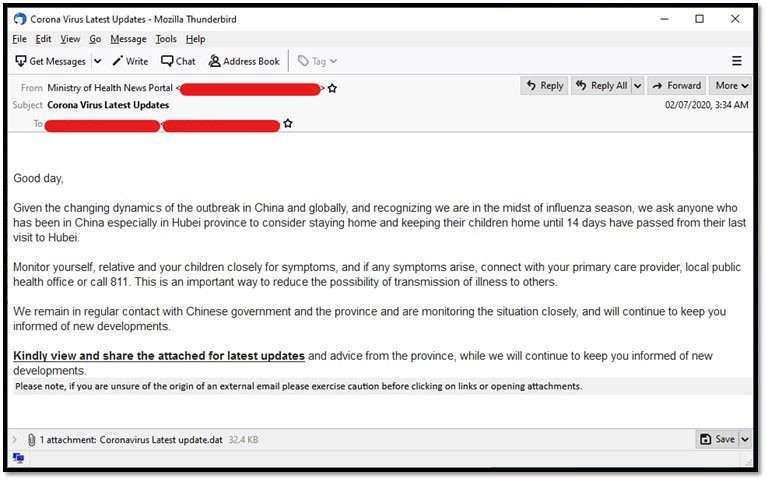
An email with a subject line 'Corona Virus Latest Updates' carrying malware. Source: trendmicro.com
When it comes to HawkEye keylogger, the people behind it follow that structure to a tee. They distribute malware via spam emails. This time, their emails don't revolve around job applications, but around Coronavirus' alerts.' Supposedly, they contain updates on the deadly virus and even offer drug advice. The email claims that these bogus alerts come from the Director-General of the World Health Organization (WHO). To clarify, they don't. It's all a scam, a ploy for malware to slither into your system. Do NOT believe the contents of the email, and, above all, do NOT follow any drug advice they offer you!
The malware's email campaign began not that long ago. Experts report that it started on March 19, 2020. Even in that short time, it has managed to claim an impressive amount of victims.
You get an email that appears personalized for you, and you alone. The salutations in the message body contain a username stripped out of the email address. Disregard that attempt at legitimacy. These emails are bogus and dangerous. Not only because they're trying to spread malware into your machine, but also because they're spreading false information that some people may look at as credible. It is not! Remember that you're dealing with cybercriminals, who wish to benefit from the misery surrounding Coronavirus.
The HawkEye keylogger has gotten updated to include additional anti-analysis techniques. It has received a plethora of changes to improve its obfuscation techniques, as well. But the infection's primary objective remains the same – theft of sensitive data.
The new sample of the malicious software aims to steal credentials from browsers and email clients. Like Mozilla, WaterFox, Flock, BlackHawk, CyberFox, PaleMoon, IceDragon, and an array of others.
As soon as the malware gets a hold of the credentials and any other data it manages to capture, it encrypts it all. Following encryption, it sends everything via the Simple Mail Transfer Protocol (SMTP) to the people behind it. If you're unaware, SMTP is a communication protocol that gets used for electronic mail transmission or, simply put, emails. The cybercriminals have coded the email address, as well as the password, within the malware itself. That way, they automate the delivery of stolen data.
A look into the workings of the updated malware
The HawkEye variant starts with a loader – a .net executable file, obfuscated by a combination of Cassandra protector and ConfuserEx. As soon as it gets executed, a few things will happen. It will search and run another .net executable, and load a bitmap image rgXREoRSAprmgvAqTsKhilTYhemNa.png in its resource section.
That second executable has the task of reading the bitmap image and extracting an encoded assembly code from it. Following that, after the cipher gets obtained, the executable file uses the first 16 bytes of the bitmap image as an XOR key to decode the rest of the picture. To elaborate, XOR is short for 'exclusive or,' and it gets used to cipher messages in a fast and straightforward manner. XOR operations are the basis of most cryptography. You can think of XOR as a toggle switch, allowing you to flip specific bits on and off.
Let's get back to what proceeds. The payload that gets decoded is another .net executable. It's a file called ReZer0V2.exe. It endeavors to turn off Windows Defender. It achieves that by changing a variety of registry items. It also runs a PowerShell command to discover the infected system's preferences for Windows Defender scans and updates before it turns them off, as well.
It then looks for Virtual Machines (VMs) and sandboxes (a virtual space that runs new or untested software or coding in secret). After that gets done, the sample uses process hollowing to inject its payload into files the .net framework directory. The technique of process hollowing is used by malicious software to load an authorized process with the sole purpose of acting as a vessel for hostile code. That final payload is, in actuality, the HawkEye keylogger.
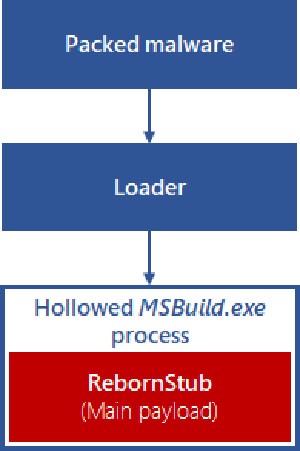
A depiction of the in-memory unpacking of a version of HawkEye malware using process hollowing. Source: cloudblogs.microsoft.com
The gravest risk, you face courtesy of the HawkEye keylogger, is data loss. The infection threatens to get a hold of your sensitive information, and then use it for malicious purposes. Once the attackers, behind the malware, have it, they can do with it as they wish – use it themselves or sell it through the dark web. In either case, they profit, and you suffer severe consequences.
There aren't enough ways to stress the importance of vigilance. Be thorough, be cautious, and don't get roped into clicking links or downloading attachments from emails that claim to contain Coronavirus-related news. Take everything with a grain of salt, and that extra attentiveness may spare you a lot of issues.







