Hijacked Routers Used to Spread Coronavirus Malware-Ridden Apps

We are living through a pandemic, and in this time of unrest, panic surrounding Coronavirus has yet to subside. People feel uneasy and scared of what's to come. In these frightening times, cybercriminals thrive. Malicious individuals leverage COVID-19-themed cyberattacks and profit off of people's fear. Booby-trapped URLs, malware attacks, and credential-stuffing scams are on the rise. These crooks have seen it fit to spread data exfiltration malware via phishing emails, unbothered by morality. There is no shortage of scams and attacks.
The latest Coronavirus scam revolves around routers. Cybercriminals have stooped to hacking routers and changing DNS settings. Their objective is to spread Coronavirus malware, and their rampage has already claimed over a thousand victims. The malicious hackers have been using the Oski information-stealing malware to carry out their attacks.
Table of Contents
What is a DNS, and how does it work?
The domain name system, commonly known as DNS, translates names to internet protocol (IP) addresses. You can think of DNS as a naming database, which contains internet domain names, and turns them into IP addresses. DNS provides the information you need to connect users to remote hosts. If you type a website into a browser, unbeknownst to you, a server maps the name to its corresponding IP address. You can see a depiction of the process in the image below.
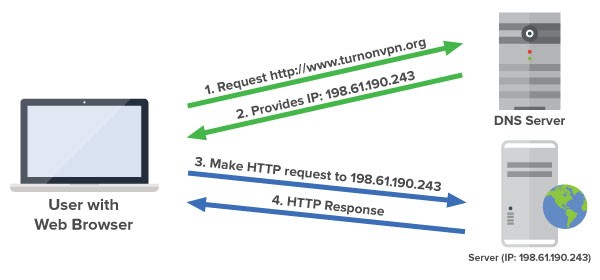
The process of DNS translating names to IP addresses. Source: devopedia.org
To carry out their attacks, hackers hijack the victim's router and change the DNS settings. They ensure that the victim gets redirected to websites, which they control. And, these cybercriminals-controlled sites are ones that promote malware-ridden Coronavirus-related content – either maps, advice, or any information concerning COVID-19, and the panic around it. These sites, then, advertise a variety of corrupt applications. If the victim downloads the malicious software using the bogus site, they invite major trouble into their device. By downloading the malicious app, in actuality, they allow the information-stealing Oski malware into their system.
Oski, the information-stealing malware – What you need to know about it?
Oski has a web-based PHP command-and-control server, which is in Russia. Naturally, experts presume that's where the people behind it are situated. It's Windows-based, which allows it to target x86 and x64 versions of Windows 7, 8, 8.1, and 10. Its standard infiltration techniques include all the usual suspects: malvertising and phishing campaigns, drive-by downloads, exploit kits. The malware can also spread as a direct zipped file or an executable. Its versatility grants it quite the range when it comes to attacks. It appears that the people trying to spread the infection, have now set their sights on a more 'direct' approach. They have begun to target routers and change DNS settings, intending to redirect unsuspecting victims to corrupt sites and pushing the nasty threat on them as a 'useful tool.'
Oski can get installed without any explicit administrative rights. What's more, it comes wrapped under a wrapper payload. Then, once Oski gets loaded in the system, that payload self-destructs. Thus, ensuring that Oski's tracks cannot get detected, and it remains hidden.
Oski made its way on the Dark Web forums in December. It got advertised by its creators as the perfect tool to steal information from its victims. Oski aims to seize data on crypto-wallet accounts, online account credentials, credit card numbers, bank account details. It's thorough in its theft.
When it comes to exfiltration, the Oski stealer turns to HTTP protocol to transmit data from the compromised end-user system. That data gets transferred as part of the HTTP POST body, and it gets sent in a compressed format. Like, a zipped file, for example.
During the short time after its Dark Web advertisement, in December, Oski has claimed quite the impressive list of victims and has stolen a plethora of private information. Experts report the malware possesses 43,336 stolen passwords. A number, Oski managed to reach, mainly from Google campaigns. A mere ten hours later, after their investigation, they noted that the number rose to 49,942, with an increase in the logs from 88 to the staggering 249.
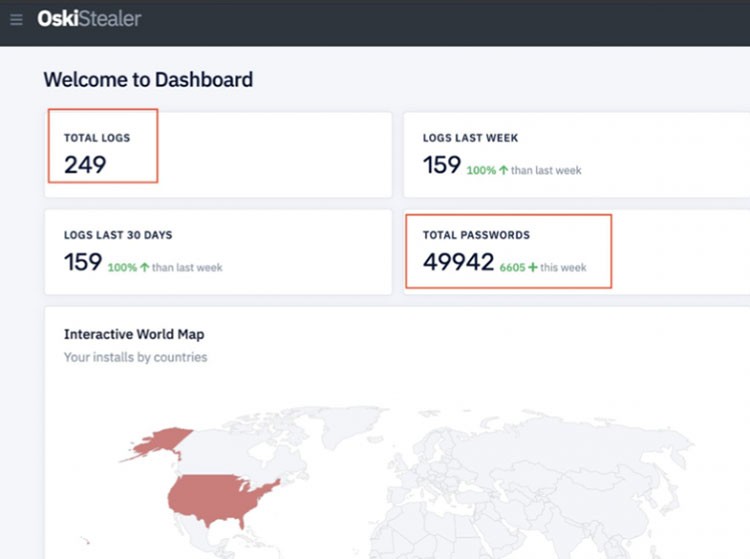
Oski's reported progress and improvement in its data theft. Source: securityweek.com
The latest Coronavirus-exploiting cyberattack
Cybercrooks always look for ways to profit off of people's fear and naivety. As explained above, their latest endeavors prey on public concerns around the COVID-19 pandemic. Security experts noted that their router-targeting campaign has only been active for a mere few days, but in that short duration has claimed over 1,193 victims. These cyber attackers target people, mainly located in the U.S., France, and Germany.
The malicious individuals aim to hack routers, which they later meddle with, and change their settings. They seem to have focused mainly on Linksys routers, targeting them by brute-forcing remote management credentials. If you don't possess a Linksys one, don't breathe a sigh of relief yet. Reports have come flooding that D-Link routers have also begun getting compromised. The cybercriminals' attack evolves. You must remain vigilant and not rely on the 'it's not going to happen to me' mindset.
These hackers hijack your router and alter your DNS IP addresses. As already explained above, the DNS has the responsibility of sending you to an IP address that corresponds to the website you typed in and wanted to visit. By seizing control over the DNS settings, the attackers can rename the DNS IP addresses and redirect you to [.]attacker-controlled webpages. You can see a list of some of the targeted domains, these crooks redirect you to, below.
- aws.amazon[.]com
- goo[.]gl
- bit[.]ly
- washington[.]edu
- imageshack[.]us
- ufl[.]edu
- disney[.]com
- cox[.]net
- xhamster[.]com
- pubads.g.doubleclick[.]net
- tidd[.]ly
- redditblog[.]com
- fiddler2[.]com
- winimage[.]com
List of targeted domains, to which users suffer redirects. Source: threatpost.com
Victims of these redirects tend to get taken to sites, which promote an app. It may not be the same app every time, but it is always one regarding the COVID-19 outbreak. Not only do they push the app, but they urge users to download it if they wish to "have the latest information and instructions about coronavirus (COVID-19)." The cherry on top is that these crooks claim that message comes from none other but the World Health Organization (WHO). That's a claim they made up for credence, and hope you believe. Do not fall for it.
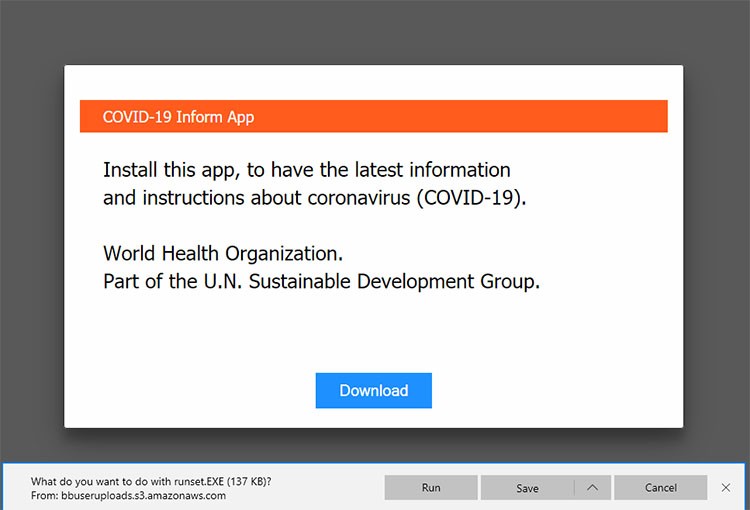
COVID-19 Inform App deceitful promotion and DOWNLOAD button. Source: threatpost.com
The myriad of Coronavirus-themed pages pushes sham apps and does its best to dupe you into downloading them. All the applications get advertised as useful, if not essential, tools to assist you during this pandemic. Don't believe that. It's a lie, crafted by malicious individuals.
These crooks gave it their best to make their lie appear legitimate. The Download button, the page boasts, has the 'href' tag, or hyperlink, set to google[.]com/chrome. That way, if you keep your mouse cursor on top of the button, you might get duped that it's reliable. The facade begins to crack when you realize that an 'on-click' event has gotten set, and it changes the URL to the malicious one.
Protect yourself – minimum effort, and you avoid maximum damage
You must change the default login username and password, with which the router comes in your possession. Create safer credentials to ensure that hacking your router remains off the table for malicious cybercrooks.
If you have a Linksys or D-Link router, change the router's control panel access credentials. If you don't have such a router, change the credentials nonetheless! Protect your cloud account credentials, as well. Also, secure any remote management account for your routers. That way, you'll manage to avoid takeovers that rely on the brute-forcing tactics or credential-stuffing attacks.
If you wish to avoid the hassle, headaches, and trouble dealing with the attack, don't ignore the warning signs. If anything seems suspicious, treat it with the appropriate amount of caution. A little extra attention goes a long way. If you wish to download an app, do it from official sources, like Google Play. Any other place deserves to get treated with the utmost vigilance.







