Cybercrooks Taking Advantage of the Global Pandemic to Profit from Coronavirus Malware

With the World Health Organization officially declaring the COVID-19 infection a pandemic, more and more countries around the world are taking extra measures to contain the spreading of the virus. In this time of crisis, hackers have taken the opportunity to exploit the mass panic surrounding the Coronavirus strain in order to spread malware and make a profit.
Table of Contents
Remote access may prove to be a threat to organizations
In some places, nationwide quarantine is being imposed, leaving many companies and organizations with no other option but to make their employees quarantine themselves at home and work remotely. It's difficult for companies and organizations to adapt their security models accordingly in such a short time. Because access and usability have been prioritized over online security, the risk of cyber attacks has increased significantly.
The main problem lies not in the need to provide a scalable remote work option, but in network security. Most people will rely on RDP (remote desktop) and enterprise VPN access solutions, to connect themselves with their work network and servers. While RDP is a great tool that gives you the ability to connect to a remote desktop and work from home, it appears that it was the most preferred attack vector for ransomware during the first quarter of 2019. On top of that, RDP credentials are known to be easily harvested by attackers.
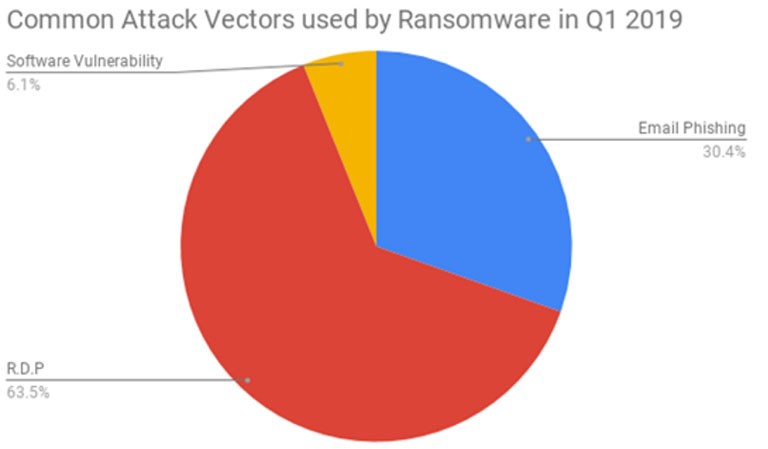
Figure 1: RDP topping the chart of preferred infection vectors for ransomware in the first quarter of 2019. Source: Coveware
When a company gives remote desktop access for its employees to work at home, it's strongly advised to reset all passwords, choose stronger ones, as well as opt for an MFA (multi-factor authentication). These requirements are necessary because a large number of employees make the mistake of reusing the same password for more than one online service. This raises the chances for personal information to get stolen and later on sold on dark web marketplaces.
A report by Cloudfare states that due to the large number of people staying at home at once, the general usage of internet has spiked on a global scale:
"As more people work from home, peak traffic in impacted regions has increased, on average, approximately 10%. In Italy, which has imposed a nationwide quarantine, peak Internet traffic is up 30%. Traffic patterns have also shifted so peak traffic is occurring earlier in the day in impacted regions."
Malicious actors exploit the Coronavirus outbreak for phishing purposes
No important global event has been left unexploited by cyber criminals for phishing. With the COVID-19 epidemic keeping people in a constant state of panic, it's very easy to lure unsuspecting victims. False promises of essential discoveries and breaking news on the Coronavirus strain are presented to the users in the form of shady links, or open infected files. All they have to do is click, and their devices will instantly get infected with Coronavirus malware.
According to ActionFraud (National Fraud & Cyber Crime Reporting Centre in the UK), Coronavirus scams have cost victims over £800k just for February 2020.
Check Point reports that since the beginning of 2020, over 4,000 domains related to the Coronavirus have been registered, many of which are suspected to be made for phishing activity.
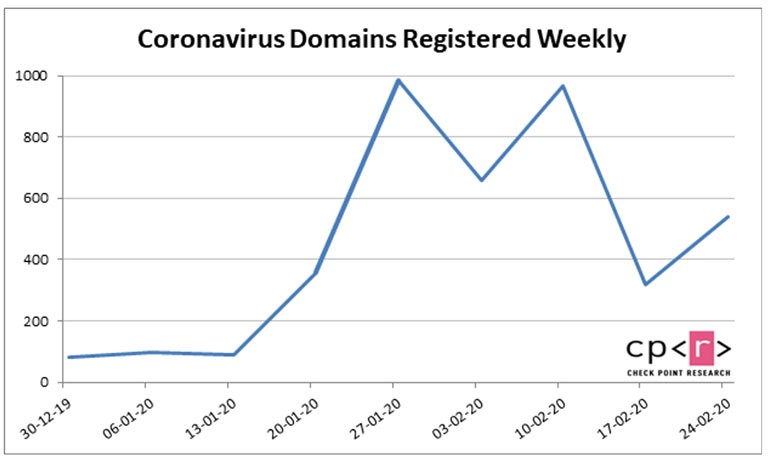
Figure 2: The graph shows the number of Coronavirus-related domains registered from the start of 2020. Source: Check Point
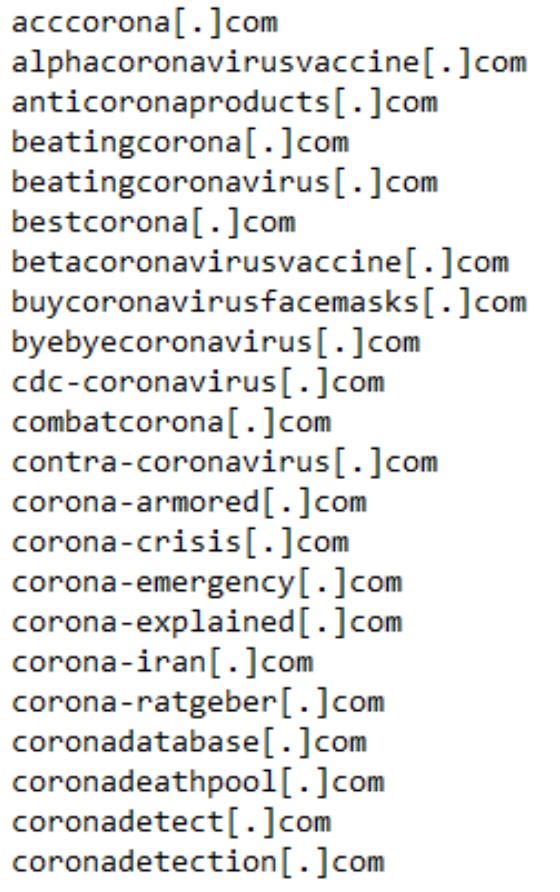
Figure 3: Coronavirus domains that are known to be malicious
Coronavirus-related spam campaigns and comment bots are swarming on the internet
Fake news and disinformation about the feared Coronavirus have turned into weapons not only for political bias but for cyber criminals activity as well.
More and more spam campaigns regarding the COVID-19 outbreak are being sent on a daily basis. They'll pretend to be from official organizations that offer legitimate information about the Coronavirus strain. The receiver will be prompted to follow a shady link, or open a file attachment.
Sophos Security Team warns of an email claiming to be sent from the World Health Organization, regarding Coronavirus awareness. The message contains the WHO logo and states:
"Go through the attached document on safety measures regarding the spreading of corona virus.
Click on the button below to download
Symptoms common symptoms include fever,coughcshortness of breath and breathing difficulties."
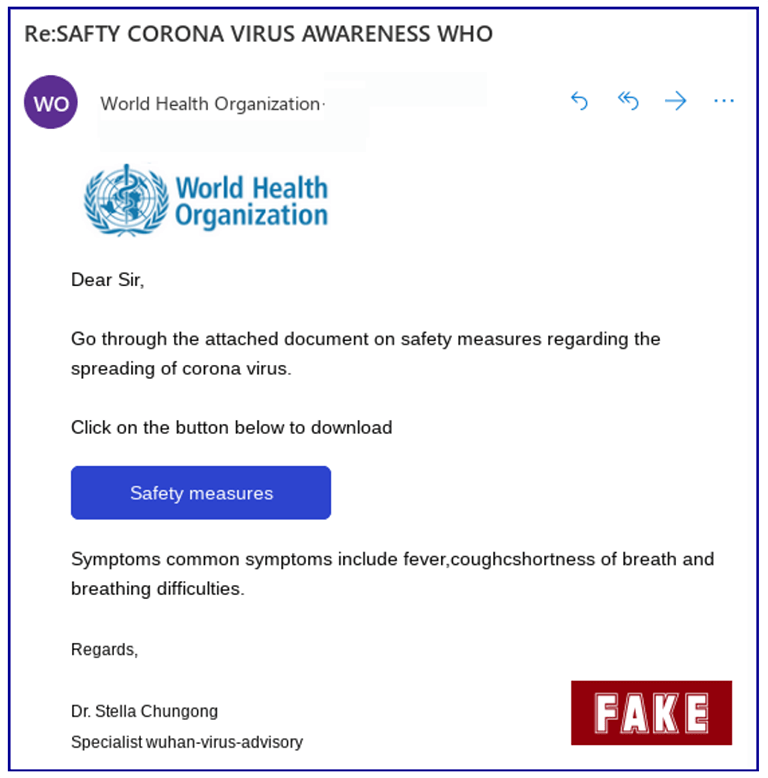
Figure 4: Image shows the scam email claiming to be from the World Health Organization. The text is full of spelling and grammar mistakes, which is a common trait in scam campaigns. Source: Sophos
Once you click the link, you'll be redirected to a site with a weird domain name, that has no connection to the WHO, and is also a non-secure HTTP site. In the background can be seen the official WHO page rendered in a frame, and a pop-up email verification form on top of it.
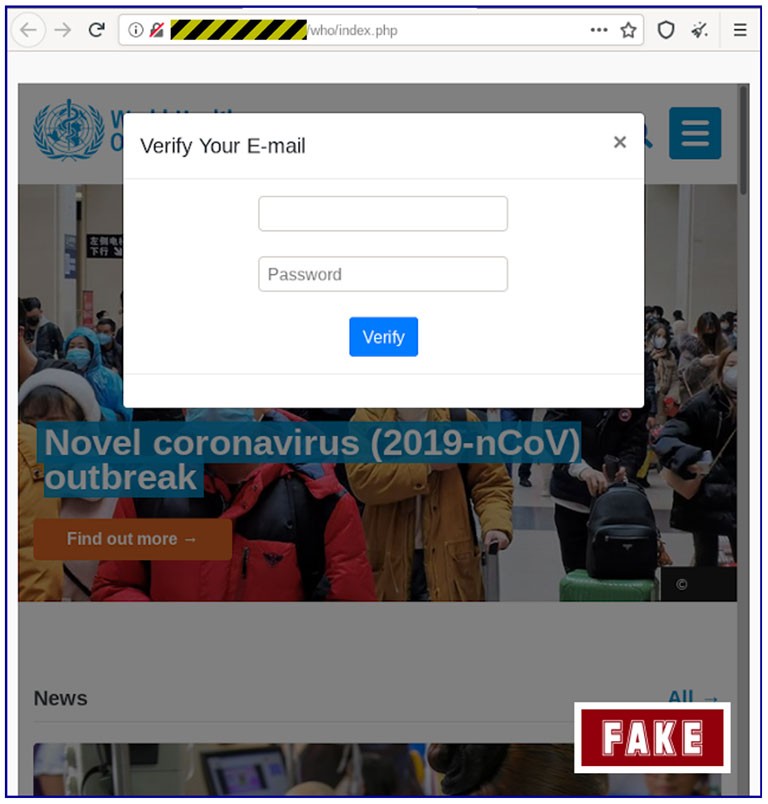
Figure 5: Image shows the site you'll get redirected to once you follow the dubious link included in the scam email. After you click 'Verify', you'll be redirected yet again, but this time to the real WHO page. Source: Sophos
Aside from scam emails, comment spamming is another popular method. Bots are programmed to inject 'Coronavirus' into the comment sections on sites since it's a highly trending search item these days. By doing so, the bad robot will help rank up the page significantly, thanks to search algorithms. Comment spamming can also be seen on legitimate and trustworthy sites since they attract a lot of readers. By using Coronavirus-related content as click-bait in their comment sections, they can lure even more unsuspecting victims.
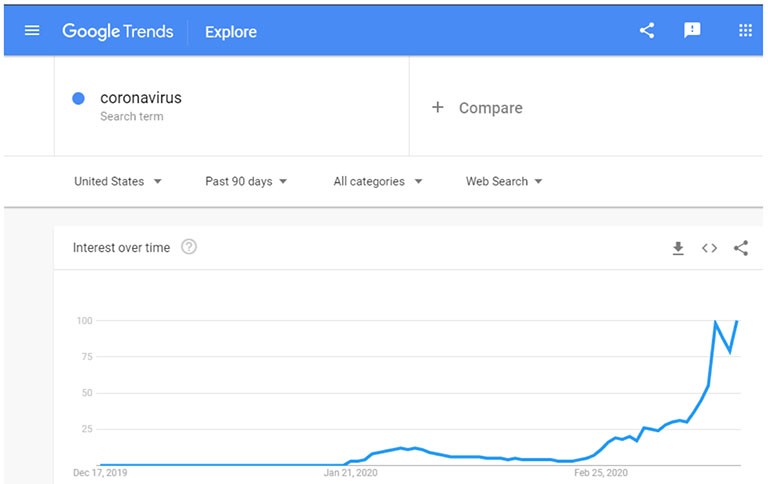
Figure 6: Image shows' Coronavirus' as a highly trending search term on Google.
Threats like Emotet and Trickbot utilize Coronavirus news stories to evade detection
According to reports from January 2020, both Trojans - Trickbot and Emotet were seen using news about President Trump's impeachment in the form of text to sneak past security software that uses AI or machine-learning technology. Due to the efficiency of this scheme, both Trojans continue to use it since it makes them appear harmless, and AV fails to detect the malicious code they carry. Only this time, the text they're adding is from Coronavirus-related news stories.
Upon closer examination of Emotet and Trickbot samples, it was discovered that they utilize news stories from CNN news, and include them as part of the malware description. The information in question can be seen in the Details section when opening the Properties window of the malware file.
This cunning trick proves to be useful to evade detection from security software with AI (artificial intelligence) and machine-learning features.
Other Coronavirus malware cases that are circulating the internet
The Emotet and Trickbot Trojans are not the only malware out there that takes advantage of the COVID-19 strain. Because the pandemic made people eager to receive news about the virus, it has created a perfect footing for effective cyberattacks.
For example, the password-stealing AZORult malware was detected in dubious websites that used a version of the interactive dashboard of Coronavirus infections and deaths (produced by Johns Hopkins University).
Another Coronavirus malware is Vicious Panda. Its creators use fake documents related to the COVID-19 virus to spread malicious software and obtain user's personal data. The Chinese actors responsible for this Coronavirus malware pretend to send official information from the Mongolian Health Ministry, aiming to make the victim disclose sensitive data.
There are also cases of malware that has 'Coronavirus' or 'COVID-19' in the name. Examples of such threats are the CovidLock and CoronaVirus ransomware. What's curious about the latter is that it may actually be a wiper, acting as a cover for a KPOT Trojan installation.
Because the COVID-19 continues to be a global hot topic, cybercrooks will inevitably exploit the situation for their benefit. To ensure you don't fall victim to Coronavirus malware, you should always be cautious when online. Here are some steps you can take to ensure this doesn’t happen:
- Don't let yourself get fooled by the name of the email sender. Since the name is not a real indicator of legitimacy, you should compare the sender's email with the one of the real organization or company they're claiming to be.
- Think twice before clicking on a link if it looks shady to you.
- Never enter personal information on a website that shouldn't require such. If you have suspicions that you've shared login credentials on a bogus site, you should change your passwords as soon as possible.
- Often, spelling and grammar errors are what give attackers away. If an important organization or company were to contact you via email, their message wouldn't be full of simple mistakes.
- Don't feel pressured to follow an email's instructions. No matter how urgently you're being prompted to follow a link or open an attachment, it would be best if you thought twice before complying. When in doubt, do the necessary research to verify the legitimacy of the email and its sender before doing anything rash.






