UCSF Falls Victim to NetWalker Ransomware Attack – Pays Over $1m Ransom

The University of California San Francisco in the USA fell victim to a cyber-attack on June 01. The institution got targeted by NetWalker ransomware and decided to comply with the attackers' demands.
Let's look into the ransomware menace. Security experts discovered NetWalker ransomware in August 2019. It first held the name Mailto due to the way it encrypted files (the extension it added was of the same name). Further analysis of one of its decryptors indicated that it's called NetWalker.
After the infection infiltrates the system, it initiates its programming – take control and encrypt everything.
What happens after the malicious file gets executed. Source: cynet.com
It adds specific extensions that lock your files and make them unusable. Most of the files you keep on your system get renamed, and their extensions change to 'mailto[knoocknoo@cock.li].[generated-file-name].'
What your files look like after NetWalker adds its extensions. Source: cynet.com
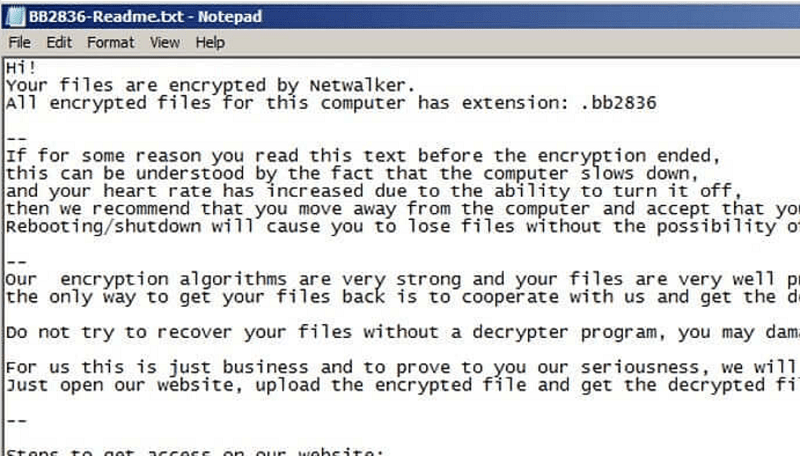
Upon completing the files' encryption, it leaves a ransom note detailing the victim's ordeal alongside demands. We found two versions of NetWalker's ransom note. You can see them both below.
Ransom note version 1. Source: cynet.com
Ransom note version 2. Source: tripwire.com
The hackers behind the NetWalker ransomware attack have not joined others with the ceasefire against healthcare institutions. Many other hackers have set their sights on other targets amidst the Coronavirus pandemic. The ones, behind NetWalker, have continued their attacks without much thought on where they land.
The Attack on UCSF
A little backstory on UCSF. The UCSF School of Medicine is one of the leading facilities in Coronavirus research. According to reports, they're doing COVID-19 antibody testing. The IT department of UCSF states that the ransomware attack on the School of Medicine's servers was not even the intended target.
The hackers cast a wide net of sorts. They unleashed their malware and waited to see where it would land. The crooks had no clear idea of targeting the School of Medicine specifically. It just so happened that it was the target they got.
To ease concerns, USCF quarantined the School of Medicine's IT systems, stating that it's a precautionary measure. Supposedly, the attack is an isolated incident that poses no danger to the core UCSF network.
"We quarantined several IT systems within the School of Medicine as a safety measure, and we successfully isolated the incident from the core UCSF network."
Source: uscf.edu
An Ongoing Investigation
UCSF's IT department has yet to finish its investigation, so they haven't made any conclusive statements. But they did report it's their belief that the server attack was opportunistic. And, stated that the hackers presented stolen data as proof of the breach. That's right. To incentivize the University into paying, they offered the data they managed to take from the servers.
According to the attackers' statement, they managed to get a hold of some sensitive information. That information included folder listings with employee information, medical studies and financials, and student applications with social security numbers.
The University's statement (which they shared on the uscf.edu site) elaborates that it's their firm belief no medical records got stolen. Patient care delivery operations, the overall campus network, and the COVID-19-related work also remained unaffected by the attack.
"Importantly, this incident did not affect our patient care delivery operations, overall campus network, or COVID-19 work."
"We are continuing our investigation, but we do not currently believe patient medical records were exposed. "
Source: uscf.edu
They share that a lot of information managed to remain untouched by the attackers, but that doesn't mean they didn't get a hold of valuable data. They stated the crooks got their hands on valuable academic work aimed to serve the public interest.
That is why the University decided it best to succumb to the ransom demand and pay up. Reportedly, they gave the cybercriminals $1.14 million as ransom. However, it's important to note that according to the University's statement, that's only a portion of the amount they got extorted for by the crooks. Their statement read that they ''made the difficult decision to pay some portion of the ransom, approximately $1.14 million." That hints that the brazen online criminals may have asked for an even steeper sum.
With those $1.14 million, the University bought itself a tool able to unlock the encrypted data. It also purchased them the return of the data, which the hackers previously obtained.
The University's move to cave and comply will undoubtedly create ripples in the online community. It's likely to incentivize crooks to craft more cyber-attacks, and strike other educational institutions. It's a crucial time for organizations in the education sector to tighten their online security. Cyber attacks will not cease but continue. Do your best to safeguard your systems from the clutches of malicious cybercriminals.








