Hackers Leveraging Coronavirus Outbreak to Shift Focus and Target Education Sector

Coronavirus doesn't show signs of slowing down as the number of infected keeps growing. While some countries are getting better with the response to COVID-19, others are not as fortunate. It's a time of great turmoil as individuals and governments are looking for the best strategy to combat the pandemic, stay-at-home orders, and comply with social distancing guidelines. What's NOT helping the situation at all, is the persistent meddling of cybercriminals.
This chart shows the trending malware related to the Coronavirus outbreak between June 05 and June 11. There have been several 'revivals' for malware tools that hackers appeared to have moved away from, like Zloader, for one.
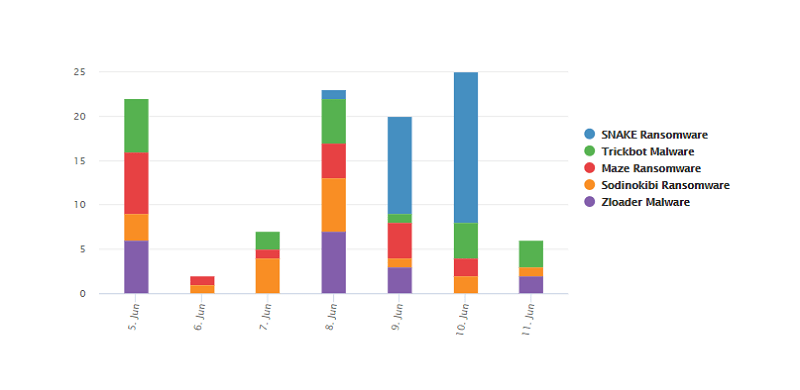
Trending COVID-19-related malware between June 05 and June 11. Source: cdn2.hubspot.net
Malicious crooks have not slowed down their cyberattacks. Instead, they've amped up their hacking, and have targeted governments and individuals from every sector. There was a time when the healthcare sector was a preferred victim of their hacking. Nowadays, the healthcare industry appears to be giving way to the education sector as a prime target of cyber-activities.
Many government officials have pleaded with hackers to cease their attacks on the healthcare industry, which has led to some crooks switching focus on the education sector. And, it's now showing a spike in attacks.
It's bad enough how the COVID-19 pandemic affected the education sector, but now that hackers are turning their sights to it, it will likely get even worse.
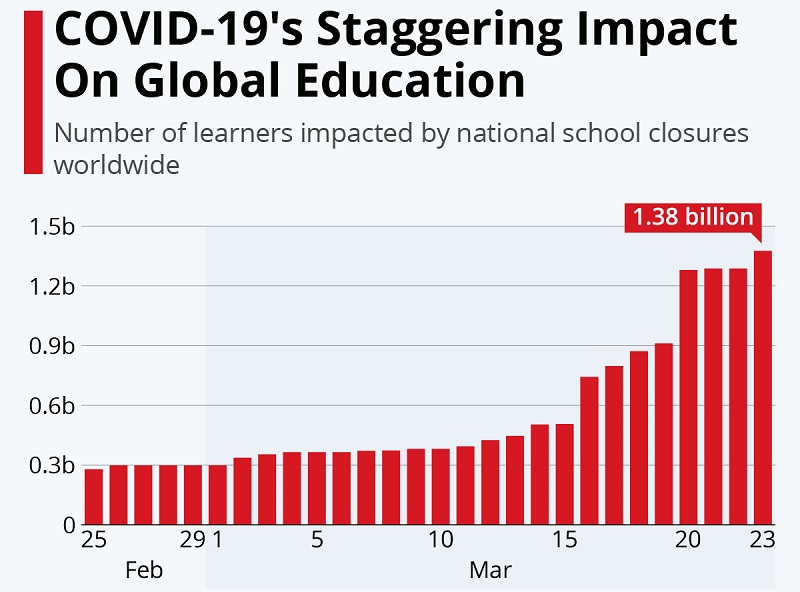
Coronavirus impact on the education sector. Source: cdn.statcdn.com
Schools, colleges, and universities have suffered budget cuts, which doesn't help them defend against malicious individuals and their attacks. Most such establishments don't have the necessary funding to install proper defenses, like cybersecurity tools and educating people working there (like administrators) what to look out for – malvertising, spam emails, corrupted links, and so on. And, they fail to protect themselves from cyberattacks.
What's more, it's not only the establishments' representatives that put them in danger of allowing hackers unwanted access. It's also the students. Some don't know any better and are prone to risky online behavior. Like, visiting sites, they shouldn't go to, or clicking suspicious links or opening an attachment that seems harmless enough but is malicious. Students are another gateway into the school system, which hackers can turn to use.
Coronavirus Makes These Attacks Easier.
Crooks' attacks have been made easier due to the Coronavirus pandemic, and the remote schooling that it forced upon students of all ages. Online classes are currently the norm, and that's yet another can of worms. Zoom, Google Hangouts, almost every platform that offers groups the ability to gather online, is susceptible to hacking.
More often than not, these establishments fall prey to ransomware attacks. That's among the most lucrative ways hackers can profit off of forcing malware into their system.
The ransomware slithers its way into the system, encrypts all the data kept there, then demands payment for the decryption. It's a simple scheme, but an effective one.
Below, you'll see a chart of the average ransomware payment made in 2018 and 2019. Since ransomware attacks are more rampant this year, the statistics for 2020 will likely be mind-boggling.
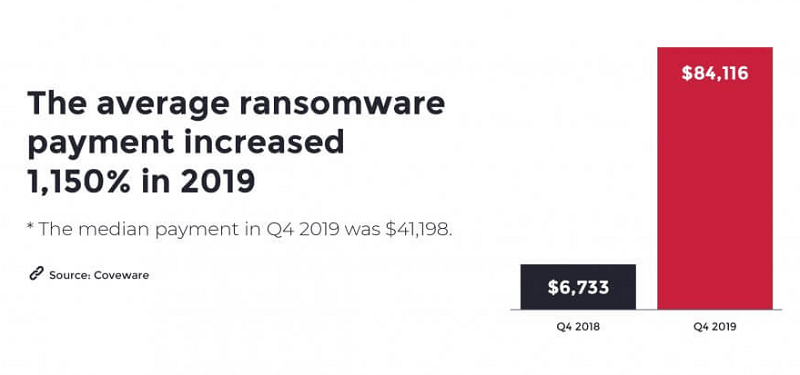
The impressive growth of ransomware payments made in 2019 compared to 2018. Source: ninjarmm.com
Research points out that ransomware attacks take up 80% of malware-related incidents in this sector – education. Here are a few examples of targeted establishments that have fallen victim to ransomware.
In March, Wichita State University in Kansas, USA, alerted its students of a security incident, which led to "unauthorized access to a computer server that WSU used to operate various student and employee web portals." University officials estimated that it impacted up to 1,762 individuals.
In May, the University of Corsica had to make the same announcement. It notified its students of a similar incident. Hackers managed to seize control of the school's network and demanded a ransom for its release.
Here's yet another chart made of data from 2019 about ransomware targets that same year in the USA. The numbers in 2020 will likely display a stark difference since malware attacks on government, healthcare, and education establishments have only grown this year compared to the previous.
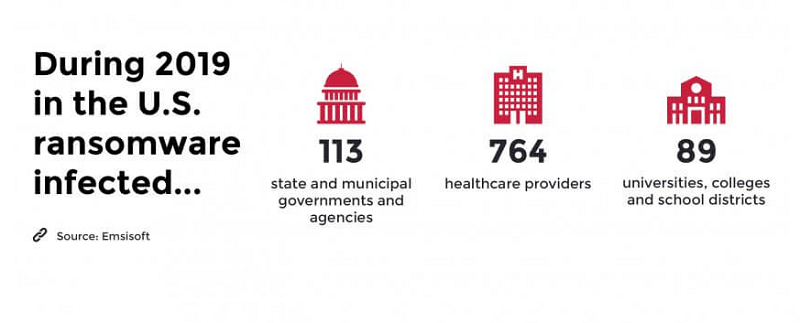
Ransomware targets in the USA in 2019. Source: ninjarmm.com
How Do Scammers Trick You?
There has been a slew of tricks, which cybercriminals resort to in an attempt to deceive you into allowing malware into your machine. Concerning COVID-19, there have been fake maps, sham contact-tracing apps, fraudulent text message scams, malicious websites. And, so many more methods, hackers still use to dupe their victims.
Malvertising and phishing campaigns remain the most commonly used means to spread hackers' lies. It's one of the easiest ways you can reach the most amount of people.
This chart shows the trending attack types related to critical infrastructure attacks. It's visible that phishing takes the lead.
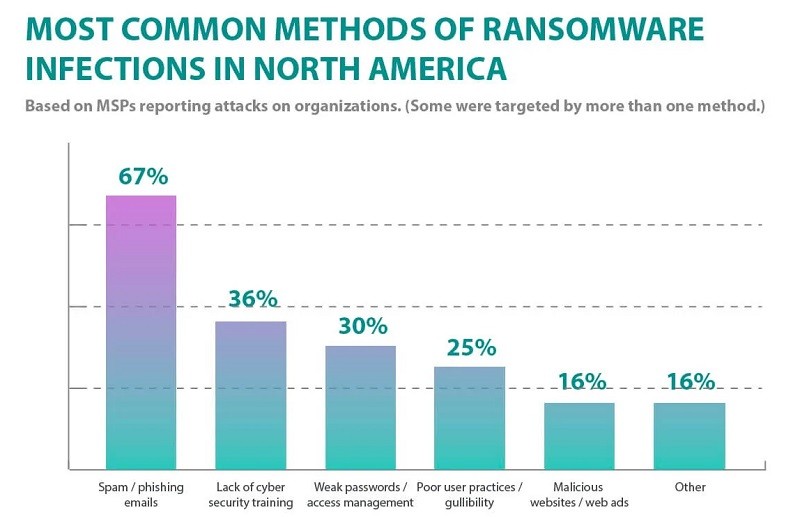
Most common methods of infiltration used in ransomware attacks in North America. Source: safetydetectives.com
Always exercise caution when online. Be wary of the sites you go to, and everything you click. Cybercriminals are savvy, and some of their scams are more difficult to spot than others. When receiving an email, ask yourself a few questions before opening it. Do you know the sender? Were you expecting an email from this sender, or did it catch you by surprise? Do you notice anything off with the sender's email address? Often-times, crooks mimic legitimate email addresses. Don't allow a spoofed email to fool you into falling for a scam! Look at emails' contents with a grain of salt. Verify they come from a verified source. Red flags tend to include grammatical, spelling, and punctuation mistakes. Remain cautious, and don't blindly follow instructions, like downloading an attachment or clicking a link. Extra attention won't hurt, but it can save you a ton of issues.








