Dexphot: An Invisible Cryptojacker that Spreads Like Wildfire

Table of Contents
Dexphot malware has the ability to exploit your system’s resources and reaps the rewards, while you suffer the unfortunate consequences.
Not many people are aware of what cryptojacking actually is, let alone why they should be concerned about it. Cryptojacking infections are malicious programs that use your computer’s processing power to mine for cryptocurrencies on behalf of a third party.
Nearly 80,000 Users Infected in a Single Day, According to Microsoft
Unlike other malware that tries to steal data, encrypt files or simply wreak general havoc on your computer, Dexphot is specifically a cryptojacking virus created to mine cryptocurrency. This type of malicious program takes advantage of your system resources to generate revenue for the people behind it. The effects of Dexphot include increases in the victims CPU and GPU usage. As a result of this, your system becomes less responsive, resulting in lag, crashes, and even data loss. Cryptojacking malware will also significantly increase the energy consumption of your computer, resulting in higher electricity bills.
This strain of cryptojacking malware has plagued users since October 2018, however, the infection reached peak activity between June and July 2019. According to Microsoft researchers, during that time, Dexphot managed to affect over 80,000 users in a single day. Since reaching that high, the daily number of victims has slowly declined. That's largely due to the efforts of Microsoft’s security experts, who stepped up and did what they could to patch vulnerabilities in their efforts to battle the threat.
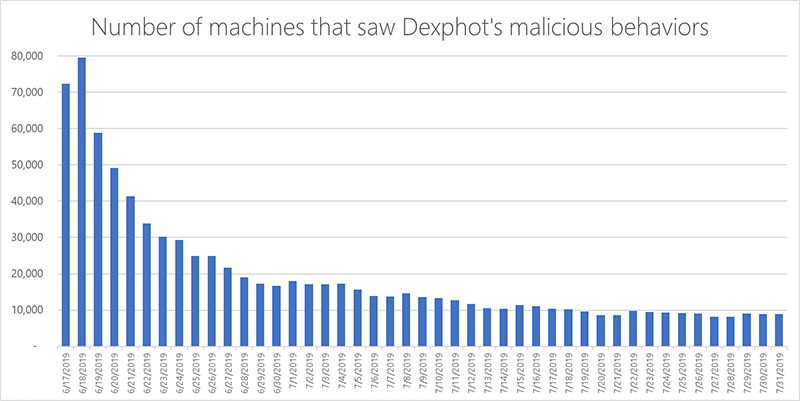
Figure 1 - Just on June 18, Dexphot Infections reached a staggering 80,000. Source: Microsoft.
Experts in the field, hail Dexphot as quite masterful in concealing its existence on your PC. They state that the malware employs ''sophisticated techniques'' to make its detection nearly impossible.
How Does Dexphot Infiltrate a System?
If you find yourself a victim of Dexphot and wonder how it found its way on your PC, the answer is simple. It generally does so via the usual trickery most malware resorts to – spam campaigns, peer-to-peer networks, fake updates, etc.
However, there have been some peculiar infection routes used by Dexphot Dexphot. It has been known to take advantage of computers that have been previously infected with another kind of malware called ICLoader. ICLoader is commonly installed in software bundles, usually pirated software and games.
Designed to Persist and Cling to Your Computer
By running malicious code straight into the system’s memory, Dexphot can remain hidden from classic signature-based antivirus programs. It employs an operation known as ''process hollowing.'' Unlike the common method where a malicious is used to infect a computer, process hollowing works by hiding in the Random Access Memory (RAM) of legitimate processes. Malicious programs that use this technique are known as "fileless malware" and are much harder to detect.
However, that's not Dexphot's only option to conceal itself. It can also do that by resorting to polymorphism. In simpler terms, it uses an array of different names for the malicious files used in a single attack. After it's done with that one attack, the malware changes the file names so they're different for the next one, therefore, preventing its admission to security nets.
Another failsafe the malware employs are scheduled tasks. The cyber threat uses a series of scheduled tasks to ensure that after each system reboot, a fileless reinfect would follow.

Figure 2.1 - This Powershell script is used to monitor the system and reinstall the malware if removed. Source: Microsoft.

Figure 2.2 - Command that utilizes scheduled tasks to add more redundancy in the other methods fail. Source: Microsoft.
What to Do If You’re Infected with Dexphot
Even if you manage to detect Dexphot lurking on your PC, the malware has a plan for that. It has a failsafe. The infection makes sure to run two monitoring services, as well as three malicious processes. If one of its processes gets shut down, it terminates all malicious functions and proceeds to reinfect your system, making it quite difficult for you to get rid of it.
When it comes to researching subjects on the internet, always take the information you find online with a grain of salt. Do additional research before you download anything. Don't click on sites or files without making sure it's reliable. Caution is always your friend. It helps you to avoid joining the ranks of the 80,000 victims of this nasty cryptominer.








