Disastrous Wiper Malware Causing Irreversible Damage to Computers Around the World

Imagine waking up one day to find that all your important data, like photos and documents, have been erased with no way to restore them. A frightening thought, isn't it? As technology changes, so is our way of storing valuable data. Let's face it, users don't keep a paper copy of every photo or document they have on their computer. With their hectic daily routines, people are so used to storing data on electronic devices for quick access.
The trouble is, not many users have the habit of keeping backups, especially on a separate device like a portable HDD or a USB stick. By failing to prepare for the worst, they become the perfect victims of a Wiper malware attack, the sole purpose of which is to destroy any data the victims store on their computers.
Table of Contents
What is a Wiper malware threat?
As its name suggests, a "wiper" is a malware threat programmed to destroy data. Interestingly, its goal is not to steal money and personal information for the attacker's benefit, but to create maximum devastation in a short time frame. Cyber criminals are able to sow fear by using a Wiper attack to create irreversible damage to governments, organizations, and businesses.
What exactly do they gain by causing such destruction? Two main reasons motivate the attackers:
- Sending a message (usually a political one)
- Covering up its tracks
Wiper malware is different than Ransomware
Wiper malware is similar to another threat – ransomware. But while ransomware offers a way for the victims to regain access to their files by paying a ransom, Wiper threats permanently delete them with no way for recovery.
In 2017, a wiper called NotPetya emerged, posing as ransomware. The threat caused massive damage worldwide, with costs estimated to be over $10 billion. Initially, NotPetya was supposed to target only Ukraine, but the attackers spread the malware globally. Reports show that the threat encrypts personal files and asks its victims to pay for a decryption key. However, after an analysis of the malware's source code, it turns out that there was never a decryption option. Even though NotPetya is able to display a necessary key for decryption, it would only decrypt to a useless random number.
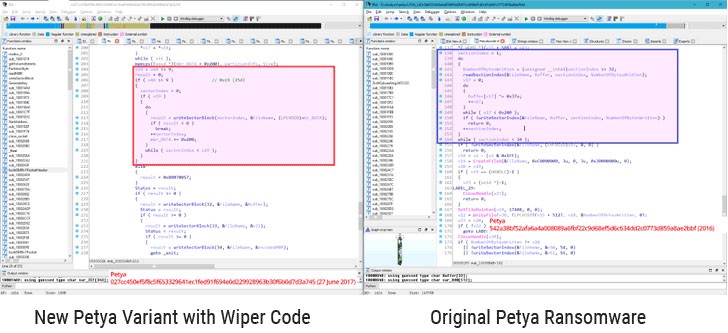
Image shows NotPetya's modified wiper code compared to the original code of Petya Ransomware. Source: The Hacker News
The malicious ways Wipers operate
Wipers in this malware family may sometimes work differently, but their targets are always the same:
- Files
- Backups
- System boot section
From these targets, the most time-consuming is the first one. Overwriting disk drives takes way too much time, and as previously mentioned, wipers seek to destroy data as fast as possible. That's why the malware will delete files at random, by writing a specific amount of data at specific intervals. Other tactics include targeting specific file types or acting as ransomware by using encrypt key points of the disk drive but minus the decryption key part. After the file destruction is complete, the wiper will hit the recovery system to ensure that the user won't be able to recover the lost data. The Master File Table (MFT) stores information on every file on the PC, including creation date, location, and access permissions. That's an excellent opportunity for wipers to ensure that the stored files are unrecoverable because when the MFT is damaged, the filesystem (NTFS) won't be able to restore them from the disk.
Information about the filesystem and disk partitions is stored in the Master Boot Record (MBR), which can also invoke the boot loaders in Volume Boot Records (VBRs). So, if something was to happen to the MBR and VBRs, be it damage or modification, the computer will fail to boot the OS and load the filesystem. While it takes some time for files to get permanently deleted, that's not the case with the MBR and VBRs, which can get damaged in a matter of seconds either through overwriting or key-less encryption.
As already mentioned, wipers do everything in their power to ensure that the damages they've done are irreversible, and the victim has no way of salvaging any data. In order to do that, this malware also has to attack specific features in the Windows OS (i.e., Windows Recovery Console, Windows backup, etc.), which are essential to restore damaged/altered file systems.
Notable examples of Wiper’s disastrous effect around the world
The first Wiper appearance is attributed to a threat called Narilam, which caused trouble back in 2008 by targeting Iranian business and financial software.
Groovemonitor is the name of a wiper attack on Iran in 2012. What's curious about this malware is that it didn't write data at specific data intervals to cause destruction. Instead, Groovemonitor's targets were certain files created on specific dates.
As its name suggests, Dark Seoul is a wiper focused on targeting South Korea. The threat became famous in 2013 with its attacks on media and bank companies.
On November 24, 2014, a particular Wiper malware attack on Sony Pictures made the news. The attack came as a response to the rather unflattering portrayal of North Korea's leader Kim Jong-un in the movie "The Interview." The geopolitical spoof tells the story about two close friends (starring James Franco and Seth Rogen), who are approached by the CIA and are entrusted with the mission to assassinate the North Korean dictator. The cyber criminals demanded the withdrawal of the movie. When Sony did not comply with their demands, the company was hit with a destructive Wiper malware, resulting in a major data loss. While the attacker's identity remained a mystery, North Korea's involvement was suspected by the US authorities, causing the Obama administration to impose new sanctions against North Korea in response to the Wiper attack on Sony Pictures.
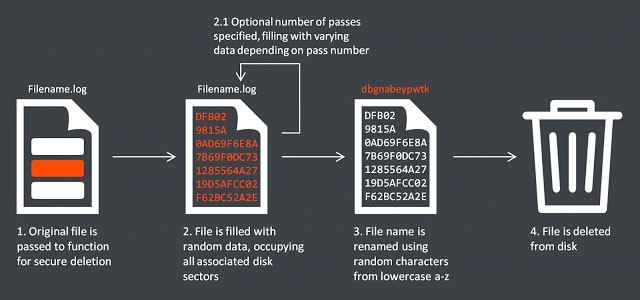
Image explaining the wiper mechanism used in the Sony attack. Source: Security Affairs
"Today's actions are driven by our commitment to hold North Korea accountable for its destructive and destabilizing conduct," stated US Treasury Secretary Jack Lew
While in a separate statement, the White House claimed: "We take seriously North Korea's attack that aimed to create destructive financial effects on a US company and to threaten artists and other individuals with the goal of restricting their right to free expression."
Shamoon is a famous representative of the Wiper family employed between 2012 and 2016 with a particular target in mind – Saudi energy companies. According to a report by IBM's X-Force, the most destructive Shamoon attack was on Saudi Aramco in 2012, which caused the data destruction of around 35,000 workstations. This malware was able to gain access to files thanks to a commercial driver called RawDisk, which allows direct modification of data on the hard drive. Earlier versions of Shamoon are known to overwrite files by using a picture of a burning American flag, whereas versions from 2016 used a picture of Alan Kurdi's body.
ZeroCleare is a new wiper threat whose attacks were increased between the second half of 2018 and the first half of 2019. During an investigation on destructive attacks in the Middle East, IBM's X-Force team discovered that the wiper behaves exactly like Shamoon, including targeting energy companies, with attacks dating back to 2012. ZeroCleare operates by overwriting the MBR and disk partitions on targeted Windows-based computers, with the help of the RawDisk toolkit, just like Shamoon did. To bypass Windows controls, ZeroCleare uses malicious PowerShell/Batch scripts.
"According to our investigation, ZeroCleare was used to execute a destructive attack that affected organizations in the energy and industrial sectors in the Middle East. Based on the analysis of the malware and the attackers' behavior, we suspect Iran-based nation-state adversaries were involved to develop and deploy this new wiper," said Limor Kessem, who is a security researcher and executive security advisor at IBM.
On December 29, 2019, the national oil company of Bahrain – Bapco, was hit with a wiper called Dustman. The attackers were able to load the wiper into the AV software by penetrating the Bapco network, consequently infecting all connected machines. On some computers, however, the malware did not operate correctly, causing no damage at all. This flaw left evidence of the malware's type and the attackers behind it. According to analysts, the attack is unlikely to be connected to known tensions with the United States. The main suspects are Iranian hackers, due to their history of hacking foreign oil and gas companies.
Is there a way to prevent a Wiper attack?
A report by Europol predicts a potential rise in wiper attacks in the near future, so it's best to get to know the threat closely and learn how to prepare for the worst. Once a wiper activates on the infected machine, there is no way to stop it. The best way to protect your data is by choosing a security solution that can predict and analyze threats pre-execution. And most importantly - always remember to backup all important data, ideally offsite. This way, even if a wiper attacks your system, you’ll have a clear path to restore the lost data.








