SilverTerrier Cybercrime Group Targets Key Workers Fighting Coronavirus

With the Coronavirus pandemic not slowing down, we rely on the people fighting the COVID-19 menace head-on even more. We're all in the hands of medical professionals, and other organizations on the front lines. Cybercriminals disregard our reliance and their morale and decency in favor of malicious purposes. They choose to profit off of these essential individuals trying to help the world in the battle against Coronavirus. Cybercriminals have not ceased their attacks.
A particular cybercrime group, originating from Nigeria, has not relented but pressed on. The SilverTerrier group has taken those essential workers as their prime targets for cyber attacks.
Table of Contents
The SilverTerrier Cyber Attackers Hit Where It Hurts Most.
The malicious cybercrime group has its sights on organizations in sectors that are critical in the fight with COVID-19. They target them by business email compromise (BEC) campaigns. That type of attack has become a calling card for SilverTerrier as they specialize in it.

Top five industries targeted by SilverTerrier in 2018 and 2019. Source: unit42.paloaltonetworks.com
In a mere three months, three SilverTerrier actors are responsible for launching a slew of COVID-19 and Coronavirus-themed malware campaigns. They managed to craft over 170 distinct phishing emails and, according to experts, exercised 'minimal restraint' in their targets of choice. Their target list comprises organizations leading national responses to Coronavirus in various countries. Like, Australia, Italy, Canada, the UK, and the US. Government, healthcare, insurance, medical research and publishing, and utility organizations are all under siege by the attackers.
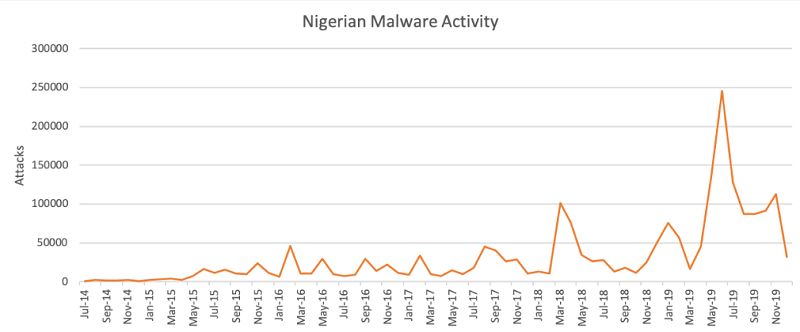
Nigerian malware activity had been declining during the last months of 2019 before COVID-19 struck. Source: unit42.paloaltonetworks.com
These crooks prey on the fact that most businesses now rely on a remote workforce as many employees work from home. Naturally, every time they get an email related to Coronavirus, they're enticed to click as they want to know of all that relates to COVID-19.
As established, the SilverTerrier group uses BEC attacks to spread malware. These attacks also go by 'man in the email' and focus on employees who have access to company funds via compromised accounts that belong to senior management, including c-suite executives.
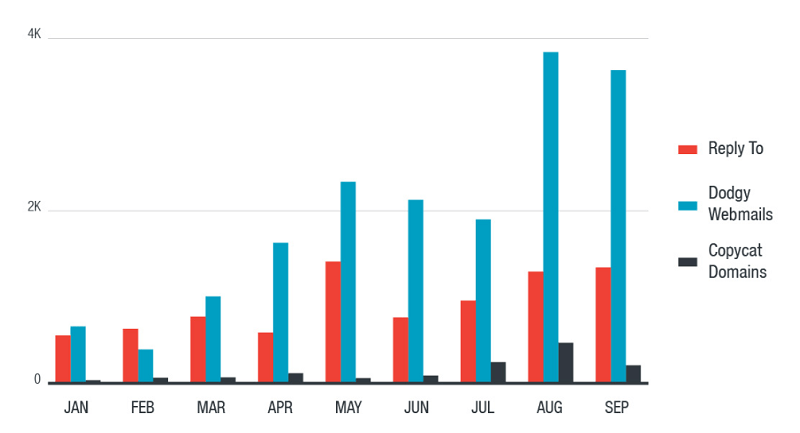
Distribution methods for email-only attacks. Source: trendmicro.com
These cybercrooks' objective is to get their targets to transfer money from company funds to bank accounts, which they control. They use every method possible to achieve that. The BEC attack is a means to an end – it aims to convince the target that the request to send money to a particular account is legitimate. They use falsehoods to secure that transfer. More often than not, claiming that it's an urgent matter that requires prompt actions. Like, asserting that an 'an urgent end-of-quarter payment has to get made.'
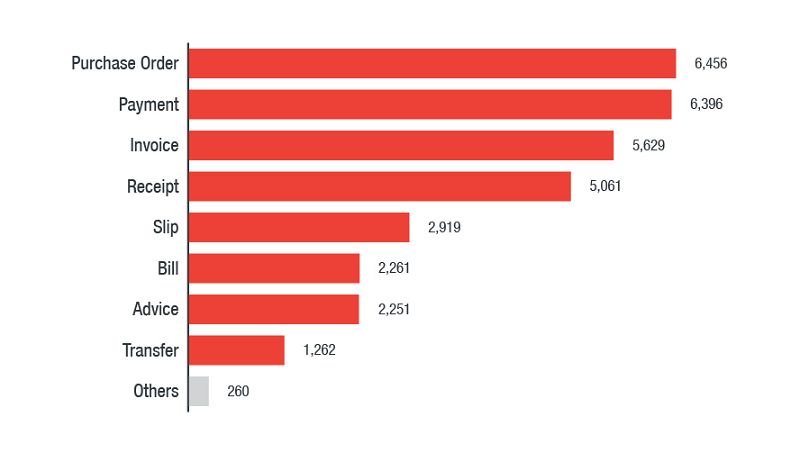
Most popular filename categories used in malicious attachments in BEC attacks. Source: trendmicro.com
Experts note these tactics work as, according to FBI statistics, in 2019, BEC attacks lead to global losses of $1.77 billion (£1.42bn/€1.62bn). Knowing these numbers, it shouldn't come as a surprise that cybercrooks have started to modify their attacks, and tailor them with COVID-19 in mind.
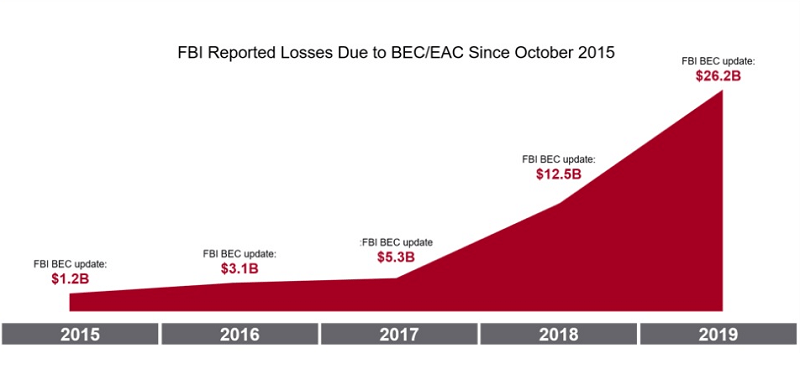
FBI reported losses caused by BEC/EAC attacks, from 2015 to 2019. Source: www.proofpoint.com
SilverTerrier carries a myriad of threats via its scams. Trojans, ransomware, adware, these crooks have no shame. Experts estimate that, currently, they spread LokiBot, FormBook, AgentTesla, and Renals.
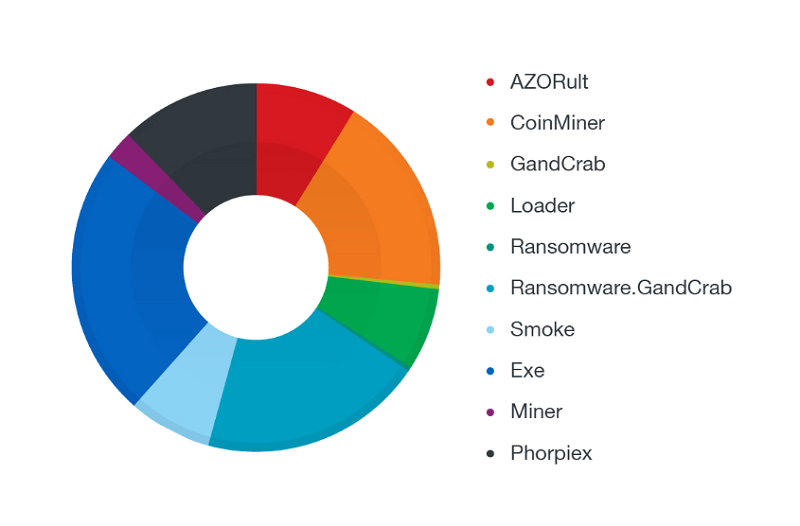
Most popular filename categories spread via attachments of phishing-related BEC attacks. Source: trendmicro.com
How Can You Protect Yourself From a BEC Attack?
One of the best ways you can defend your employees from falling into the clutches of a BEC attack is a rather simple one. If you don't want your employee to approve the moving of funds into an unauthorized account based on a deceiving email, make it so they cannot do that.
Implement more workflow controls, and make it so all financial transactions must get the approval of multiple individuals. That leads to the attacker having to deceive several people, which in turn increases the chances at least one will notice something off with the request. It's a simple yet effective strategy to ensure money only goes where it's supposed to, and not in the hands of criminals. The more fail-safes you have, the better.
Train your employees to stay hyper-aware of online schemes, and make sure they know how to avoid these shenanigans. They should always remain on the lookout for phishing emails. Below, you can see examples of two such emails.
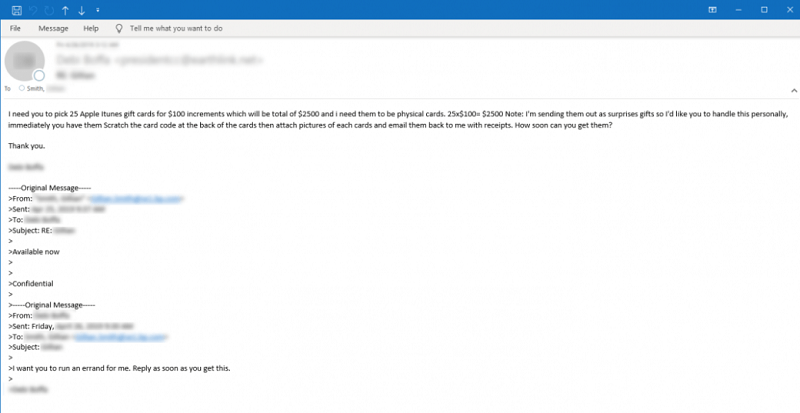
Sample email asking the target to buy physical Apple iTunes gift cards. Source: symantec-enterprise-blogs.security.com
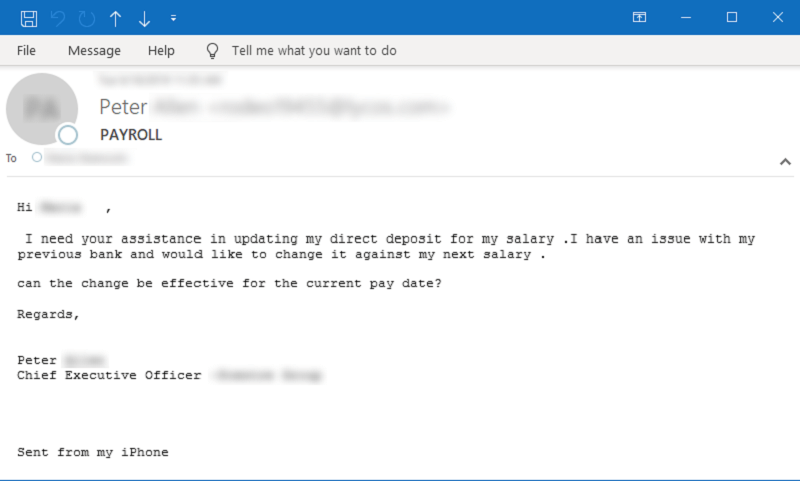
Sample email asking for help on a payroll/salary issue. Source: symantec-enterprise-blogs.security.com
After an email lands in your inbox, subject it to close inspection. Is the grammar okay? What about spelling and punctuation? Do email addresses and logos match up? Did you expect to receive the email, or did it catch you off-guard? All of these little things add up and matter, and they can save you a ton of money and troubles.
Who Is Most at Risk of Such Attacks?
Experts assert that so far in 2020, the BEC scheme trying to sneak malware into your system remains the most prominent threat to cybersecurity. Below you can see statistics of these attacks, based on country, as well as the most common keywords used in the attacks.
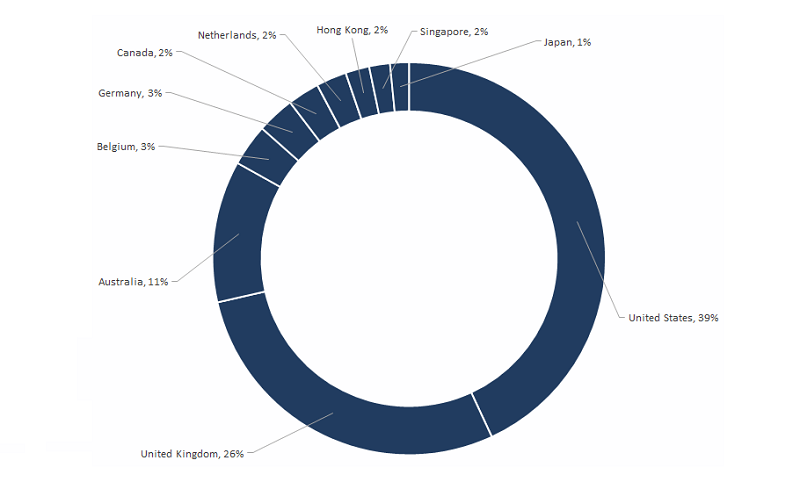
Top 10 BEC victim regions from July 2018 to June 2019. Source: symantec-enterprise-blogs.security.com
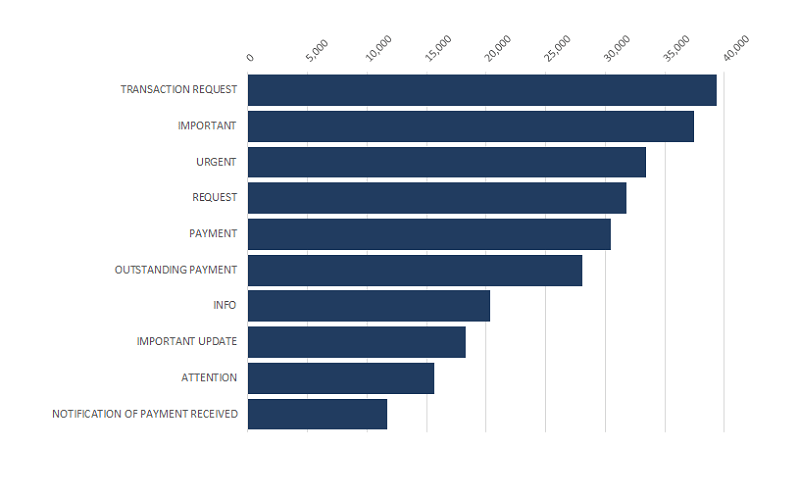
Top 10 BEC keywords used in attacks from July 2018 to June 2019. Source: symantec-enterprise-blogs.security.com
The very nature of the BEC attack places a wide variety of institutions at risk. Security researchers advise caution. Healthcare and insurance organizations, government agencies, public utilities, and even universities with medical programs should remain vigilant.
Coronavirus-related emails must get examined with attention and scrutiny. Especially so, if they contain links, 'you must click on,' attachments 'you must download,' or a listed bank account 'you must transfer funds to.' Double-check everything, and don't do anything on blind faith. It's always better to be safe than sorry. Take the extra time to verify the legitimacy of the email. That earns you more than peace of mind, but also a reliable system.








