Spearphishing Campaign Takes Advantage of Coronavirus Fears to Spread Lokibot Infostealer

Coronavirus-related cybercrime has skyrocketed in the past few months. Malicious individuals forsake human decency and take advantage of the panicked state of the world, and the constant need for information. Cyber attacks are on the rise.
As you can see in the chart below, trend searches seem to overlap. One line represents the overall search for Coronavirus by Google Trends, and the other shows social media discussions on cybersecurity and cybercrime connected to Coronavirus.
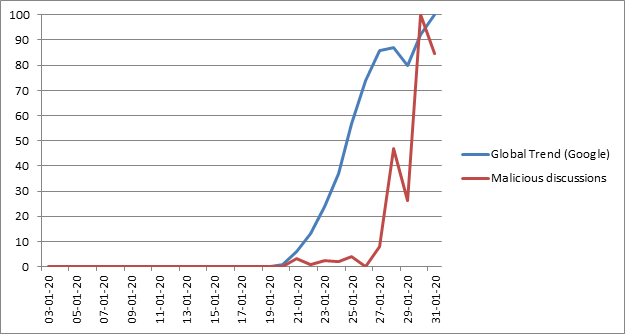
Comparison between the Coronavirus trends – the virus and the malware. Source: blog.checkpoint.com
You can also see the spike of newly registered websites with domain names related to Coronavirus.
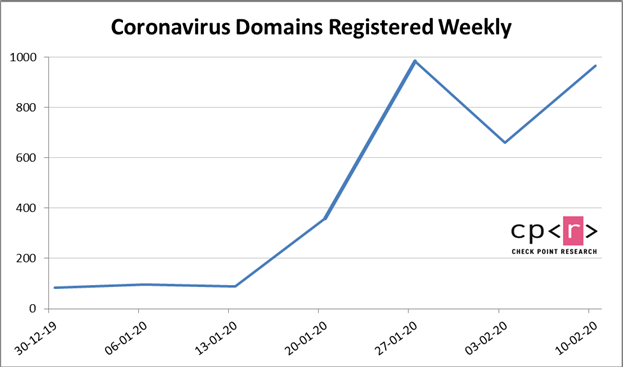
Noticeable increase of registered Coronavirus-connected domains. Source: blog.checkpoint.com
Naturally, it's more than likely that not all of these sites relate to cybercrime. Regardless, the increase should not get ignored since Coronavirus-related malware attacks have spiked in an equally formidable manner.
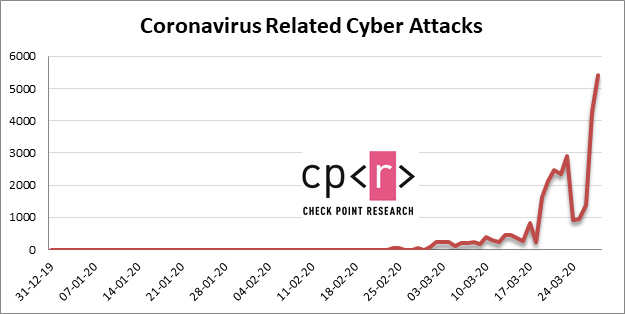
Coronavirus-related attacks in the last few months. Source: blog.checkpoint.com
Cybercriminals prey on people's fears to spread info-stealing malware. The latest in a long string of scams, piggy-backing on the Coronavirus pandemic, involves the Lokibot infection. Malicious individuals capitalize on the fact that everyone's eyes stay glued to the COVID-19 development, and most people ravage each shred of news, even remotely related to Coronavirus. These crooks use that to their advantage and profit off of the masses' need for information. They have crafted a spearphishing email, carrying the Lokibot Trojan threat.
To give further legitimacy to their sham, the cybercrooks behind the deception, use the World Health Organization (WHO) trademark. It acts as a lure that baits as many victims as possible into falling for these falsehoods. And, unwittingly, inviting malware into their machine. These crooks promise to provide Coronavirus-related information, and that's something every person craves at the time of this scary pandemic. People are frightened and uncertain of what's happening and what's to come. Cybercriminals exploit those fears.
Table of Contents
Beware the spread of misinformation
Above all, you must realize that this bogus email does not come from WHO! It's neither reliable nor legitimate. Its goal is to look trustworthy enough to get you to follow its instructions. And, in doing so, to allow the malware latched onto the email into your PC.
Ironically enough, the email these people send you in their attempt to unleash an infection on your system has to do with misinformation. That's right. The scammers claim to address the spread of misinformation. It's chock-full of text banging on and on about the dangers of misinformation, suggestions, recommendations on what to do if you face it, and several points on infection control. Every word of the email aims to earn your trust and keep your attention. The entire message is in English, but some noticeable grammatical and punctuation errors hint that the people who wrote it do not have it as their first language. They also made a more significant gaffe. As mentioned, the cybercriminals claim the email comes from WHO. The email says it's from the WHO Center for Disease Control, which is a mix of the two major healthcare organizations WHO and the Centers for Disease Control and Prevention (CDC).
Their carefully crafted lie contains an attachment, which you get urged to download. If you do download and execute it, you're in trouble as that unleashes the Lokibot Infostealer into your system. And, that Trojan is anything but a desirable companion.
Lokibot’s infiltration process
The email's subject line is quite enticing. The crooks have named it 'Coronavirus disease (COVID-19) Important Communication[.]' in the hopes of getting as many people hooked into opening it as possible.
The attachment bears the name 'COVID_19- WORLD HEALTH ORGANIZATION CDC_DOC.zip.arj.'
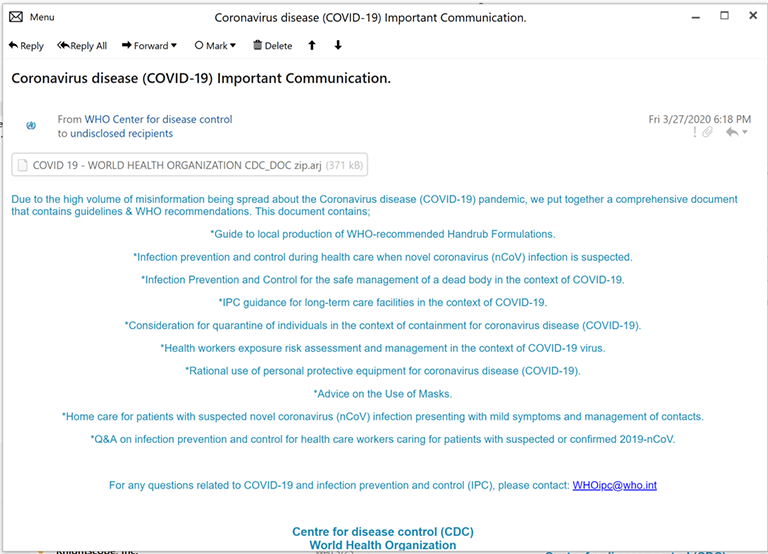
The email in question. Source: fortinet.com

The bogus WHO trademark accompanying the email. Source: fortinet.com
ARJ is a compression format, which gets used to create highly efficient compressed archives. You can open the compressed file with 7-Zip. The crooks, behind the scheme, use the ARJ format in the hopes that it will induce people into opening it since it's not an 'exe' file as most other scammers turn to when trying to spread their infections. But as soon as you click the attachment and decompress the file, you'll see an 'exe' file pop up. The file transforms to one that instead of the 'Doc.zip.arj' has a 'DOC.pdf.exe' extension.
Upon execution of the malicious file, the Lokibot Infostealer makes its way into your system, and corruption ensues. The infection lifts an array of credentials from your machine. The list is extensive, and it includes passwords of all kinds – ones stored in the browser, and stored email ones, as well as FTP credentials. Its entire design revolves around harvesting sensitive data from you. Then, once it steals that information from you, the malware proceeds to deliver it to the attackers' command and control (C&C) servers. The data gets exfiltrated to the URL 'hxxp://bslines[.]xyz/copy/five/fre.php.'
Around the world in less than thirty days.
This Coronavirus-related spearphishing campaign has not been around for long. It first got detected at the end of March, with some reports stating March 27 as the exact date of discovery. Since then, in a relatively brief amount of time, the attack has claimed quite a few victims. It has gone global, with targets in Austria, Germany, Turkey, the United States, and Portugal. These are the countries with the highest amount of reported incidents, but the target list does not end there. The campaign has also spread to Canada, Spain, Belgium, Italy, and Puerto Rico.
As it's clear to see, the Trojan's tactics are simple but quite effective. Don't underestimate the damage it can do. Lokibot has earned its reputation for being sneaky and efficient. So much so, that there are quite a few versions of it floating around the dark web for sale. Black market forums market Lokibot as a password and crypto-coin wallet stealer. You can even become the proud owner of one, for as small a price as $300.








