Cybercriminals Target Healthcare Organizations Fighting Coronavirus

The world is amid a pandemic. Coronavirus has spread globally and has claimed a staggering amount of victims. People are scared and unsure of what to do and what's to come. In these uncertain times, one thing has remained a constant – everyone agrees that the people fighting the pandemic first-hand are heroes. Nurses, doctors, researchers, medical professionals in the front lines, doing their best to help. These are people who are worthy of respect in general but even more-so deserve it now. A lot of them have been doing their day-to-day even without the proper protective equipment because they don't want to turn their backs to the people who need them most. They risk their own life helping those in need. That's worthy of admiration.
Unfortunately, some people don't care about sacrifice, public duty, and common decency. There are cybercriminals, who see it fit to put profit over people. Crooks, who don't care about the state of emergency most countries are in, and the state of panic almost all individuals are in, non-stop. These malicious individuals have decided now is the time to unleash malvertising campaigns. Not only that, but attacks aimed at those we need most – healthcare professionals, fighting the dreaded Coronavirus head-on. They have unleashed their attacks at hospitals, healthcare organizations, and medical suppliers, and medical professionals are suffering from it. Instead of focusing on helping people, they're distracted by the greed of cybercrooks.
Table of Contents
No Time Like the Present for a Quick Cash Grab
The malicious individuals unleashed their malvertising attacks onto those trying to protect us from the virus. Malware researchers uncovered two recent campaigns of note – one against two Canadian establishments: a government healthcare organization and a medical research university. And, the other cast a wide net and aimed at medical organizations and medical research facilities worldwide.
The crooks sent out a slew of emails to the organizations and masked them as legitimate. They purported their legitimacy by claiming to contain COVID-19-related information. More specifically, medical supply data, details from the World Health Organization (WHO), or vital corporate communications regarding the virus. Whichever front the email put out, its real objective remained the same – to spread malware. The cybercriminals loaded these emails with ransomware, info-stealers, Trojans, and more. All in the name of a quick cash grab.
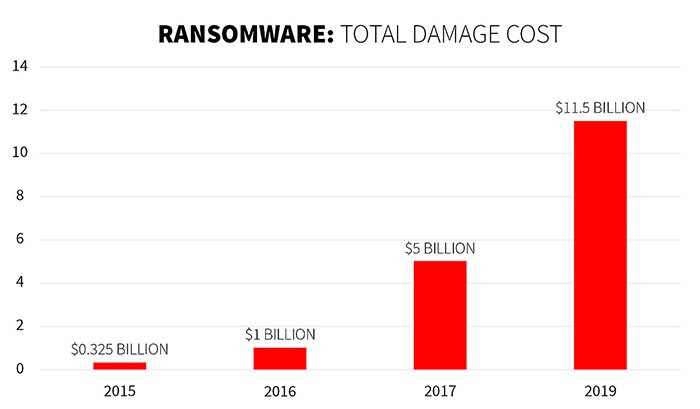
Depiction of the year-to-year increase in the profitability of ransomware. Source: gdatasoftware.com
The Ins and Outs of the Phishing Attacks
At the end of March, more specifically between March 24 and March 30, researchers noticed certain peculiarities about COVID-19-related attacks. There were several attempted attacks aimed at people actively engaged in fighting Coronavirus. As mentioned, the cybercriminals' first attempt at an attack targeted individuals, connected to an unnamed Canadian government health organization, involved in COVID-19 response efforts. And, their second one aimed at a Canadian university responsible for conducting COVID-19 research.
The malicious emails did their best to mimic legitimate ones. They spoofed an actual WHO email address (noreply@who[.]int) and contained a rich text format (RTF) file that supposedly had information related to the pandemic.
To open this email is a mistake. To open the RTF is an even bigger mistake.
After the RTF file gets opened, it attempts to deliver a ransomware payload into your system. The payload exploits a known vulnerability (CVE-2012-0158) in Microsoft Office. It lets the attackers execute arbitrary code.
If you open the malicious attachment, it drops and executes a ransomware binary to disk at C:\Users\
The malware, the RTF file hides, appears to be an open-source ransomware variant by the name of EDA2. That infection is part of a grander, more ominous, ransomware family – that of HiddenTear. If the name rings a bell, it's no surprise. The HiddenTear threat is a behemoth that has claimed countless victims.
As soon as the binary gets executed, an HTTP GET request for the resource tempinfo.96[.]lt/wras/RANSOM20.jpg gets initiated. The infection slaps on a notification display on your Desktop to clue you in to your predicament – 'YOUR PC IS LOCKED.' The message it contains reads: 'If you want to unlock your files, you must send .35 BTC [Bitcoin] to this address.' It then leaves you the address in question. To clarify, at the time of writing this article, .35 Bitcoin equals 2,670.13 USD.

Image of the ransomware notification message. Source: unit42.paloaltonetworks.com
The image gets saved to disk at C:\Users\
The ransomware binary encrypts an array of files extensions, including '.DOC', '.ZIP', '. PPT' and more. Researchers note that this ransomware's binary has a substantial limitation. It's hard-coded only to encrypt files and directories that are on the victim's Desktop.
Here's a list of the various file extensions, which the ransomware binary encrypts:
'.abw', '.aww', '.chm', '.dbx', '.djvu', '.doc', '.docm', '.docx', '.dot', '.dotm', '.dotx', '.epub', '.gp4', '.ind', '.indd', '.key', '.keynote', '.mht', '.mpp', '.odf', '.ods', '.odt', '.ott', '.oxps', '.pages', '.pdf', '.pmd', '.pot', '.potx', '.pps', '.ppsx', '.ppt', '.pptm', '.pptx', '.prn', '.prproj', '.ps', '.pub', '.pwi', '.rtf', '.sdd', '.sdw', '.shs', '.snp', '.sxw', '.tpl', '.vsd', '.wpd', '.wps', '.wri', '.xps', '.bak', '.bbb', '.bkf', '.bkp', '.dbk', '.gho', '.iso', '.json', '.mdbackup', '.nba', '.nbf', '.nco', '.nrg', '.old', '.rar', '.sbf', '.sbu', '.spb', '.spba', '.tib', '.wbcat', '.zip', '7z', '.dll', '.dbf'
The infection's encryption algorithm is simple yet effective. All your files get locked and renamed with the extension '.locked20.' You can see the ransomware source code in the image below.
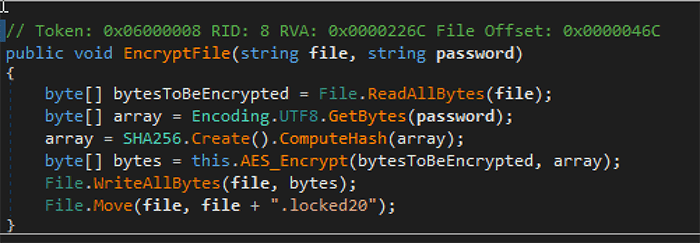
The encryption source code of the ransomware. Source: unit42.paloaltonetworks.com
After the remote command and control server (also called C&C or C2) manages to get a hold of your data, it creates a custom key based on the username/hostname details. It proceeds to send that key back to the infected host for further processing.
Once the key gets received from the C2 server, the infected host initiates an HTTP POST request to the resource www.tempinfo.96[.]lt/wras/savekey.php containing its hostname and the primary decryption key for the host, which is, in itself, AES encrypted.
Empty Promises and No Actual Cease-Fire
Recently, there was a slew of promises made by cybercriminals that they would discontinue attacks aimed at hospitals, while the pandemic lasts. That pledge and those promises proved nothing more than empty words as research points that attacks continue to this day. There have been several hospitals that have shared alarming information – Ryuk ransomware has targeted them. Ryuk is another monstrous threat in the ransomware world.
I can confirm that #Ryuk ransomware are still targeting
hospitals despite the global pandemic. I'm looking at a US health care provider at the moment who were targeted overnight. Any HC providers reading this, if you have a TrickBot infection get help dealing with it ASAP.— PeterM (@AltShiftPrtScn) March 26, 2020
Social media post from March 26, confirming Ruyk's hospital attacks. Source: twitter.com
It's not only Canada and the USA that are suffering from these attacks. As mentioned, the crooks have gone global with their greed.
A London-based healthcare provider, by the name of Hammersmith Medicines Research, works with the British government to test COVID-19 vaccines. They reported a ransomware attack recently. The Maze ransomware claimed them as victims, and the crooks who launched that attack later posted the data they stole from the organization online.
Medical organizations and medical research facilities in Japan also joined the list of targets, by way of the AgentTesla malware. In said list, you'll also find a German industrial manufacturing firm, a Turkish government agency managing public works, a Korean chemical manufacturer, and a United States defense research entity.
All these places, and likely others like them, fall victim to malvertising campaigns that exploit the Coronavirus situation for financial gain. The cybercriminals, behind the attacks, use COVID-19 to lure the targets into opening their emails. Since Coronavirus is quite the buzz word at this point, it tends to successfully bait people into trusting the bogus emails enough to open them. To achieve that, and ensure their success, they usually put an attention-grabbing tag-line. Like, for example, 'COVID-19 Supplier Notice" or a "Corporate advisory.'
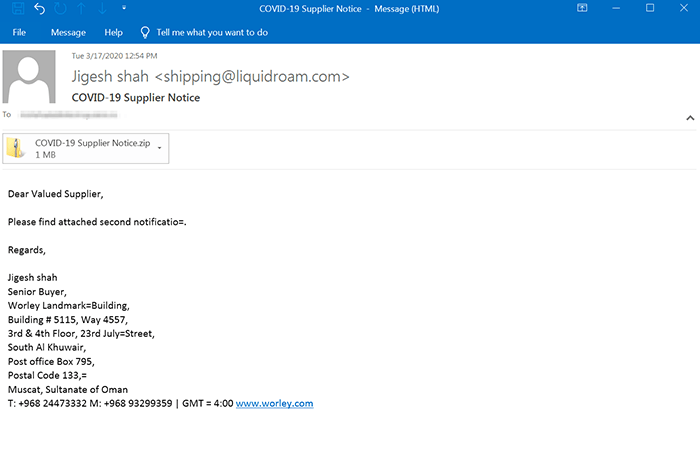
A phishing email that's shown to contain the tag-line 'COVID-19 Supplier Notice.' Source: media.threatpost.com
Getting you to open their sham email is the cybercriminals' first step. Once they trick you into doing that, they have to dupe you into believing the contents of the email enough to follow its instructions. They tend to be the same in every single one – see the attachment, and open the attachment. Do NOT! Don't fall victim to their trickery.
The attachments for the nasty emails proved to be droppers that deliver variants of the AgentTesla malware family. In case you're unfamiliar with this particular infection, it's an info-stealer that has been around the block since 2014. It gets advertised and sold on a myriad of forums, which act as watering holes for cybercriminals. AgentTesla is among the top malware families of choice of the SilverTerrier threat actor, which is notorious for business email compromise (BEC) campaigns.
Below you can see a chart showing the reported losses from BEC attacks in recent years. As you can see, the growth is evident.
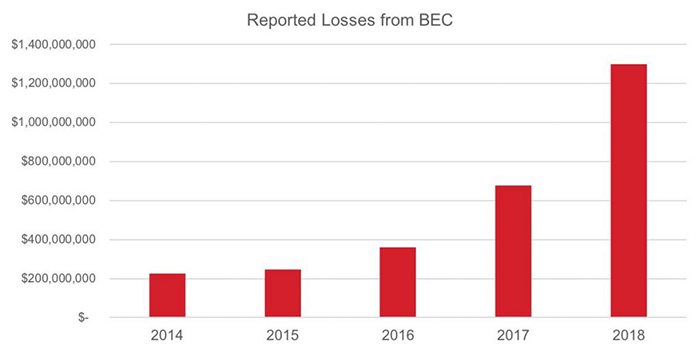
Depiction of the reported losses from BEC attacks from 2014 to 2018. Source: vadesecure.com
Tricking People Is a Tricky Business
Reports show that the email address, responsible for sending out these malicious emails, is 'Shipping@liquidroam[.]com.' It uses a legitimate business domain for LiquidRoam, which provides sales of electric skateboards. Upon discovering this, researchers concluded that it has gotten compromised, and has fallen into the hands of cybercriminals to use as they see fit.
Another observation made by researchers showed that all the associated samples connected to the same C2 domain for exfiltration – 'ftp[.]lookmegarment[.]com.' They also add that the AgentTesla samples had hard-coded credentials, which got used to communicate with the C2 server over File Transfer Protocol (FTP).
Cybercriminals show no sign of stopping their attacks. To this day, they continue leveraging the Coronavirus pandemic as a theme for their malicious cyberattacks worldwide. They spread malware using spearphishing campaigns, booby-trapped URLs, and credential-stuffing scams. Be careful not to fall into the web of lies they spin. Exercise caution, and remember that you can never trust the word of cybercriminals, as is evident by the continued attacks on research facilities and healthcare institutions.








