Chinese-Based Vicious Panda Group Weaponizes Coronavirus Data for a Cyber Attack

Vicious Panda is a Chinese-based anonymous group that carries out attacks against a variety of targets. It received the classification Advanced Persistent Threat (APT). APT indicates a prolonged and aimed attack. One that locks on a specific target, with the sole intention to corrupt and compromise their system. All the while, trying to gain information from or about that target.
Table of Contents
Misinformation or the lack of information works in favor for hackers
The Vicious Panda campaign exploits the current global situation for profit. There's a world-wide pandemic, following the spread of the COVID-19 strain of the Coronavirus. It's a highly contagious, potentially deadly virus that has people in fear for their lives. Most people will click and download anything and everything, even remotely associated with the disease, because people feel starved for news. Most don't know what to believe, what's an exaggeration, what's fake, what they should do, and what they should avoid. Every shred of information gets hungrily consumed, and further spread and passed on to relatives, friends, and followers via social media. While people are afraid for their lives and the lives of loved ones, Vicious Panda sees an opportunity for profit. It takes advantage of people's fears and the Coronavirus scare.
The Chinese-based group has come to use fake documents, supposedly containing information about the Coronavirus. Its objective is to slither into your system, take over, and get a hold of all manner of private data to then exploit for profit.
The growing demand for Coronavirus-related news has presented an opportunity for cybercriminals. Malicious hackers use government reports, tracking maps, World Health Organization reports, and health fact sheets, corrupt them and unleash them unto unsuspecting victims.
Vicious Panda, in particular, chose two fake documents as its infiltration method. It feeds into the fear-frenzy and lures people into opening its documents and providing them with sensitive personal information.
Vicious Panda's attack is a sly one that proves a remarkable example of social engineering. This APT sent out two documents that appeared to mimic press briefings, related to COVID-19. And, both of them harbored remote access malware.
The campaign appears to target the Mongolian public sector. It uses the pandemic scare to deliver a previously unknown malware straight to the target. That is, by far, not the only operation associated with this group. They have been carrying out attacks since 2016, at least, and their victims' list includes countries like Russia, Belarus, and Ukraine.
How does Vicious Panda carry out its attack and corrupt your system?
The malicious group uses corrupted documents to make its way into your machine. Malware researchers have figured out that two RTF documents get used. They get sent to the Mongolian public sector, and one of them reads that it's from the Mongolian Ministry of Foreign Affairs. Both of the documents are in the Mongolian language. The malware-carrying documents' presumed goal appears to be to take screenshots, exfiltrate, delete and edit files, and remotely execute processes.
If you're unsure, an RTF document is a text file format used by Microsoft products, like Office and Word. The abbreviation stands for Rich Text Format. RTF files can get read by most Word processors.
You can see the RTF files used by the Vicious Panda group in their original (Mongolian) language, as well as the translated version (in English), below:
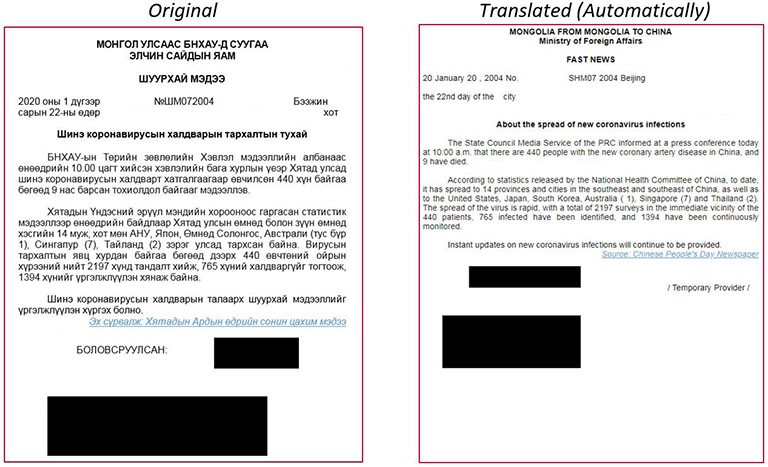
Document 1 – Information about the prevalence of new Coronavirus infections. Source: research.checkpoint.com
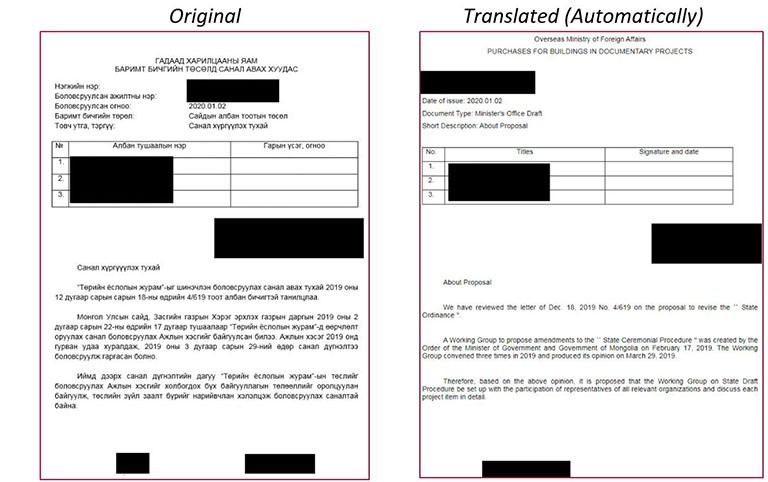
Document 2 – Purchases for buildings in documentary projects. Source: research.checkpoint.com
The Vicious Panda group used a tool called RoyalRoad (aka 8.t) to weaponize these RTF files. More specifically, it turned to the 7.x version of said tool. It's not a novel action, considering Chinese threat actors often turn to this tool for assistance in their attacks. It allows these attackers to make documents and customize them to fit each of their targets. The documents, they craft, can have embedded objects, which exploit the Equation Editor vulnerabilities of Microsoft Word.
What happens next?
The malicious group sends out these documents and dotes you into opening them. That's why the current attack exploits the pandemic and the fears surrounding the Coronavirus strain COVID-19. One of the documents bears the name 'About the Spread of New Coronavirus Infections.' It even cites the National Health Committee of China. If you open it, and the Microsoft Word vulnerability, as mentioned above, gets exploited, here's what follows.
A file with the name intel.wll gets dropped into the Word Startup folder, called %APPDATA%\Microsoft\Word\STARTUP. Every time, you then launch the Microsoft Word application, each DLL file that has a WLL extension in the Word Startup folder will launch alongside it, as well. That process triggers the infection chain. You can see a visual representation of the infection chain below:
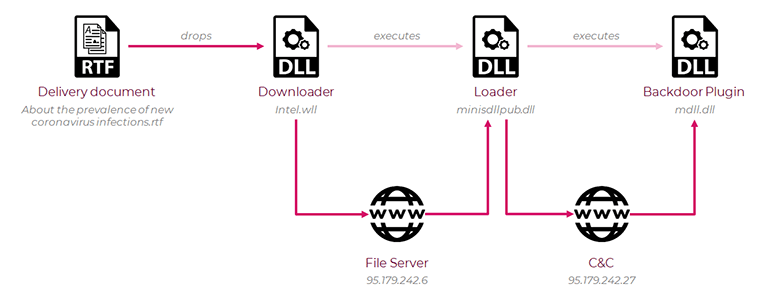
Chart of the infection chain mentioned above. Source: research.checkpoint.com
This action ensures that the infection chain will not fully come to fruition if it's run inside a 'sandbox.' In a computer security sense, the term 'sandbox' relates to a security mechanism that gets used for separating running programs. It executes programs (or code) deemed suspicious, or ones that have yet to get tested. The device tests and verifies that your machine will remain secure if you run a particular program (or code). A sandbox helps ensure system safety. It prevents the spread of software vulnerabilities.
The Vicious Panda group has made sure that, if run in a sandbox, their infection chain will not show its real face, and reveal its actual potential for damage. That way, their attempts to cause harm to your system will not get foiled.
For the complete execution of the malware, Microsoft Word must get relaunched. After it gets loaded, the intel.wll DLL downloads and decrypts the next stage of the infection chain. To do so, it uses one of the servers that belong to the threat actor (95.179.242[.]6).
What comes next is the download of another DLL file, which serves as the primary loader of the malware framework, which the attackers crafted. It gets executed by Rundll32, and communicates with yet another server, belonging to the threat actor (95.179.242[.]27). The communication assists it in receiving additional functionality.
The attacker, behind the servers, does the job of analyzing and potentially gaining access to the advanced parts of the infection chain near impossible. He operates the command and control server (C&C server) in a limited time frame, by going online for only mere hours every day.
When the infection chain reaches its final stage, the loader downloads and decrypts a RAT module, which is also a DLL file, and after, loads it into memory. The RAT module seems to have a base of common core capabilities, but it also stands out with some unique features. That has led to malware researchers branding it a 'custom and unique malware.'
- Take a screenshot
- List files and directories
- Create and delete directories
- Move and delete files
- Download a file
- Execute a new process
- Get a list of all services
A list of the common core capabilities. Source: research.checkpoint.com
Now comes the second stage payload, named Minisdllpub.dll.
Payload is a term that describes the objective of the malware that has found its way into your machine, be it adware, hijacker, Trojan, ransomware, and so on. It's what the hackers have designed said malware to do once it finds itself, lurking on your PC. Payload includes data deletion, data encryption, data damage, personal and financial information theft, et cetera.
The second stage payload in Vicious Panda's attack chain is the encrypted DLL file to get downloaded from the 95.179.242[.]6 server. That file's name is minisdllpub.dll, and it's a downloader for yet another payload.
Minisdllpub.dll creates a mutex by the name Afx:DV3ControlHost. A 'mutex' is also known as a lock since it's a program object used to prevent simultaneous access to a specific resource. After it creates the mutex, it defines a structure of size 0x5f8 that allows it to store a plethora of data, connected to the system, and the environment, as well. That can include the following: the version of the operating system, IP addresses, username and name of the running PC. Following that structure, another one gets created. Its size is 0x3FC, and its goal is to store: command and control IP address (95.179.242[.]27), port (443), API functions, and pointers to loaded DLLs.
As soon as it finishes creating these structures, it sets up a new threat. It gets a few lists of API functions and loads them dynamically. Each of these lists contains the name of a library. And, also, a sequence of API functions to load from said library. Then, these functions get pointers added to the previous structure, which get used to dynamically invoke them, when the time comes to do so.
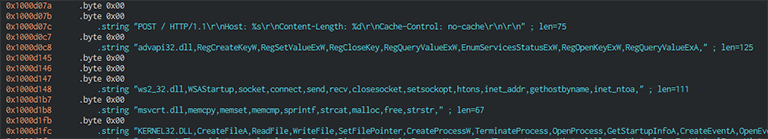
Lists of API functions, separated with commas, prefixed with the library name. Source: research.checkpoint.com
The second stage payload, named Minisdllpub.dll, then sets up HTTP/HTTPS communication and begins to communicate with its remote control via new threads. Following the reply of the server, and a few more malicious actions, Minisdllpub.dll loads a new Portable Executable File (PE) to memory.
Minisdllpub.dll and its role as the 'middle-man.'
As soon as that file gets loaded, it starts a search. It looks for an export function with the name 'e.' Meanwhile, the malicious software continues to listen to and receive commands from the server. After it gets a command, it passes it on to the aforementioned 'e' function. In doing so, Minisdllpub.dll fulfills its role as the 'middle-man' between the C&C server and the final payload, which is a remote access tool. In the image below, you can see the malware looking for the export function 'e.'
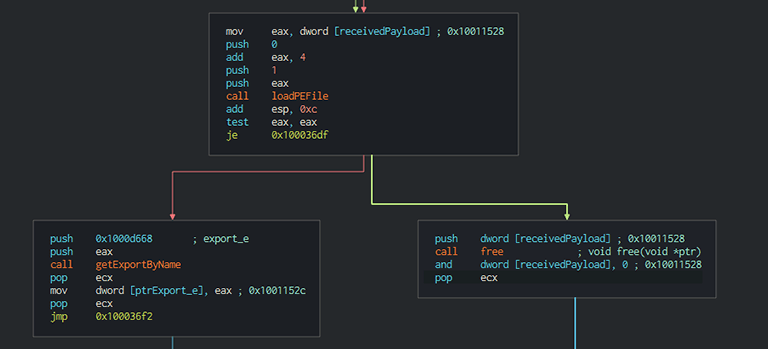
The search for the export function 'e.' Source: research.checkpoint.com
At this point in the malware's corruption process, the victim's machine contains quite the unique layout of modules loaded onto it. If the description of the process got too jumbled for you, here's a representation of it, to clarify everything explained so far:
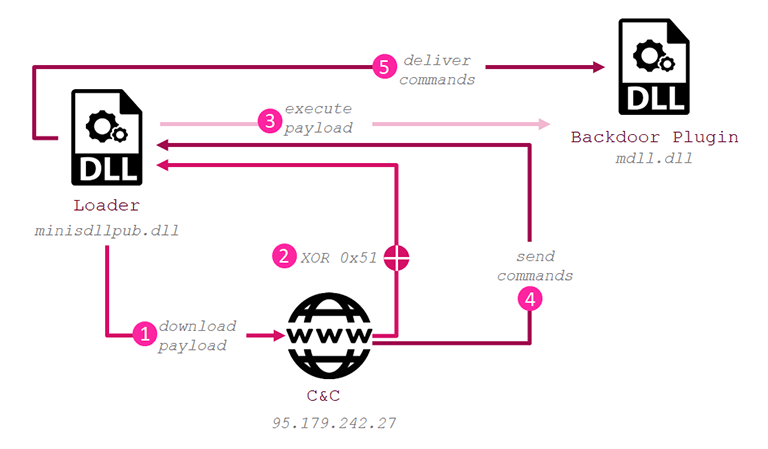
A visual depiction of the loader execution flow. Source: research.checkpoint.com
Minisdllpub.dll passes onto the final payload an array of commands to execute, as well as a myriad of structures. The Remote Access Trojan (RAT) now uses all of the structures, which got created and filled. With their help, the RAT dynamically invokes API functions, as well as delivers data to the C&C server. This entire approach is somewhat unique and turns the analysis of the RAT into a near-impossible feat.
Vicious Panda appears to be only the latest of a string of Chinese-based operations against foreign governments and organizations. The Vicious Panda campaign preys on people's fears regarding the current pandemic and leverages the COVID-19 virus to bait potential victims into triggering the infection chain. Do your best to stay level-headed and vigilant. Don't allow your fear to turn you into a victim of Vicious Panda.








