RIPlace: A Simple Evasion Technique That Makes Bypassing AV and Ransomware Protection Possible

Ransomware has proven to be a nuisance on a global scale, with some attacks costing millions of dollars. Imagine what would happen if there's a coordinated cyber attack. Cambridge University researchers estimated that if such a coordinated attack were to hit 600,000 businesses around the world, it would cost the global economy up to $184 billion. Researchers share that in their modeled scenario, the attack is launched through malicious emails that, once activated, can encrypt data on nearly 30 million devices within 24 hours. Sounds scary, right?
Knowing that, how would you feel if there's a way for ransomware to completely bypass all security measures on computers like AV (Anti-Virus) software and extra ransomware features? Not good, we bet. Sadly, this scenario may become true. Security researchers at Nyotron have discovered a new evasion technique called RIPlace that has the potential to change the way ransomware operates by making it invisible to security software.
Table of Contents
About RIPlace
In Spring 2019, Nyotron's Research team followed the responsible disclosure process and shared that they've discovered an evasion technique that could help malware bypass most AV, anti-ransomware, and Endpoint Detection & Response (EDR) products. Due to its ability to evade detection by replacing sensitive files on its victim's machine, the researchers named it "RIPlace" - a combination of the replacing function and RIP (Rest in Peace), as the replaced original files no longer exist.
What makes RIPlace so dangerous
- The evasion technique can be used on machines running Windows XP or newer versions.
- It would only take a few lines of code to bypass the ransomware protection features installed on the victim's machine.
- RIPlace works even on systems that are timely patched and run up-to-date AV products.
- Inbuilt ransomware protection features and other security products can be eluded thanks to RIPlace.
How RIPlace manages to bypass ransomware protection
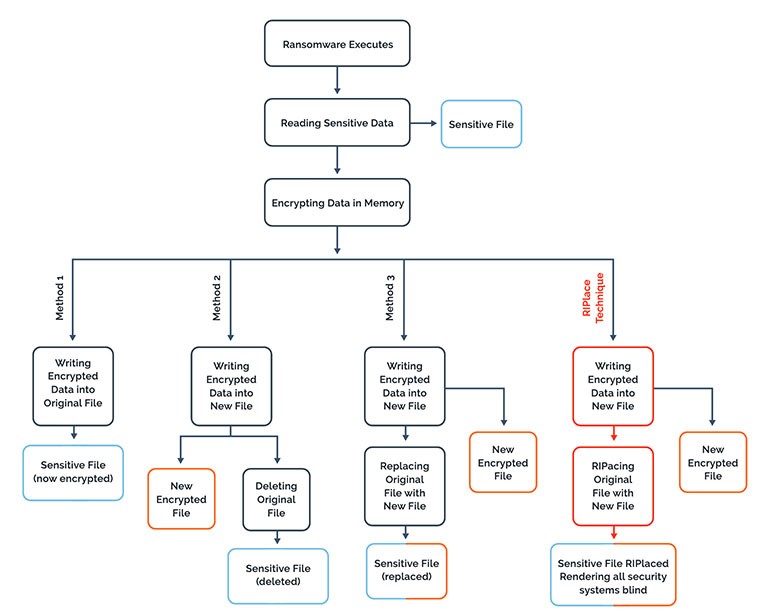
Fig.1: How ransomware works and the way RIPlace makes a difference. Source: Nyotron
As shown on Fig.1, most ransomware is known to perform the following actions after a successful activation:
- Open/Read original files.
- Encrypt content.
- Save the encrypted file on Disk.
- Replace the encrypted file with the original one.
With the new evasion technique, there's a difference when it comes to the fourth step where RIPlace renames and replaces files. When a Rename request is called (IRP_MJ_SET_INFORMATION with FileInformationClass set to FileRenameInformation), the filter driver gets a callback to filter the request. Nyotron's research team found that if DefineDosDevice (a legacy function that creates a symlink) is called before Rename, it will be possible to pass an arbitrary name as the device name, and the original file path as the target to point on.
With RIPlace, "the callback function filter driver fails to parse the destination path when using the common routine FltGetDestinationFileNameInformation." Even though it returns an error when passing a DosDevice path, the Rename call is successful.
That being said, if your AV/ransomware protection products can't handle IRP_MJ_SET_INFORMATION callback properly, it may be possible for cyber attackers to bypass them using the RIPlace technique. Nyontron researchers note that this vulnerability can be abused by attackers to avoid getting their activity recorded by EDR products, as well as to bypass security products that rely on FltGetDestinationFileNameInformation routine.
There are no reports about RIPlace being used in the wild
"We have not seen the RIPlace evasion technique used in the wild yet. However, we believe it is just a matter of time. Cybercriminals often leverage disclosed vulnerabilities within days if not hours. Unfortunately, this technique is trivial to use, requiring literally two lines of code to implement," says Nir Gaist (Nyotron CTO/co-founder) in an interview for Digital Journal.
Phishing and ransomware attacks have been immensely successful for the last few years, so there's no doubt that in 2020 they'll continue to thrive, especially across local, state, and healthcare institutions. If attackers were to use the RIPlace technique, the impact would be catastrophic.
Only a few security vendors have taken proactive actions against RIPlace techniques
It's evident that in the wrong hands, RIPlace could potentially make ransomware unstoppable. Nyotron disclosed the issue to security vendors, but not everyone saw RIPlace as a threat, arguing that it still hasn't been used by cyber attackers. Even so, the smartest thing would be to fix the issue, rather than wait for the worst to happen. So far, only a handful of vendors have addressed the issue in their products.
Microsoft stated that the RIPlace technique is not considered a vulnerability since it doesn't meet their Security Servicing Criteria. Even with their CFA (Controlled Folder Access) ransomware protection feature enabled, the RIPlace bypass can still be executed, as demonstrated in Nyotron's video:
It's been established that all versions of Microsoft Windows (from Windows XP to the latest Windows 10) are exposed to this vulnerability, even if they have the latest and greatest of AV, NGAV, and EDR security products installed.
The Nyotron team has also released a free tool for people that want to test their systems and/or security products against RIPlace.








