Tech, Real Estate, and Healthcare Companies Fall Victim to VegaLocker Ransomware Variant, Zeppelin

Zeppelin ransomware, a relatively newer malware threat, is found to be part of the VegaLocker ransomware family, alongside Jumper (Jamper) and Buran. It's written in the Delphi programming language, which gets categorized as a "high level" language. The Delphi source code proves quite challenging to reverse engineer, which only works to Zeppelin's advantage. The Zeppelin threat is a variant of the Buran threat specifically, as they are both Ransomware-as-a-Service (RaaS) infections. A RaaS model allows you to target a system, even if you don't have any knowledge about cyber attacks. It's a type of subscription. You subscribe to using a certain RaaS and absolve yourself from having to code the ransomware yourself. Instead, you use someone else's threat. The profits that infection then brings in get split between its creator and the person paying to use it. The Zeppelin RaaS threat offers the same profit split as its predecessor Buran did – 75% of the money goes to the affiliates, with the remaining 25% going to the ransomware operators.
The Zeppelin cyber menace first made an appearance in November 2019. And, in no more than a month, its target list was entirely comprised of companies from the IT and healthcare industry. Reports of recent attacks indicate that Zeppelin may have turned its sights on real estate firms, as well. Zeppelin seems to have its focus on entities located in the US and Europe.
Zeppelin offers all the perks of a RaaS threat. It's highly configurable as you can modify it to your liking – ransom amount, preferred target list, ransom note contents, it can all be changed to your preference. You can also choose how it gets deployed – as a .dll or .exe file, or even wrapped in a PowerShell loader. Once you make these decisions, and the ransomware gets deployed into a system, it doesn't only proceed with encryption and extortion. It also follows a list of instructions, things to do while in the machine. It terminates a variety of processes and focuses on the ones that have to do with database and backup, and mail servers.
What's more, the executables are under three layers of obfuscation. Zeppelin ransomware utilizes obfuscation, as well as environment-awareness techniques, to escape signature-based endpoint defenses successfully. It's a rather sophisticated infection.
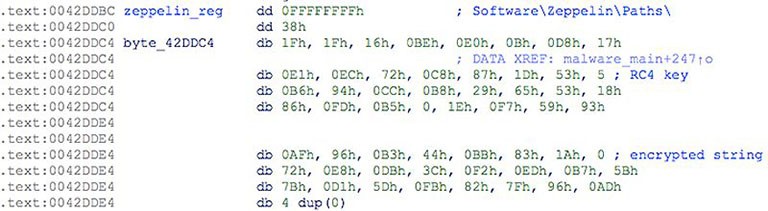
Example of Zeppelin obfuscated string. - Source: Threatvector.Cylance.com
Table of Contents
What follows Zeppelin’s infiltration?
After Zeppelin enters your machine, it installs itself into a temporary folder with the name 'zeppelin,’ which is where it gets its name. As soon as the ransomware settles into your system, it strikes. It uses cryptography algorithms to encrypt your data. Documents, archives, photos, videos, all of it gets locked. If you wish to get it unlocked, you must follow the ransomware's demands.
To secure its hold over your files, Zeppelin attaches a randomized extension to every single one you have on your PC. Each file gets renamed and rendered inaccessible. The ransomware uses the hexadecimal numeral system. For example, a picture that used to be called "1.jpg" becomes "1.jpg.126-D7C-E67." Aside from that 3x3 extension format, Zeppelin also has the option to attach ".zeppelin "at the end of each file. So, the file "1.jpg" turns into "1.jpg.zeppelin." The ransomware also adds file-markers to the locked data. They also share the 'zeppelin' name. A myriad of symbols can surround the marker, and which symbols it gets depends on the hex editor and character format you use.
As soon as Zeppelin has your files under its grasp, it leaves you a text file with demands. It's called "!!! ALL YOUR FILES ARE ENCRYPTED !!!.TXT." That's the ransom note that lists everything the cybercriminals expect you to do if you wish to regain control over your data.
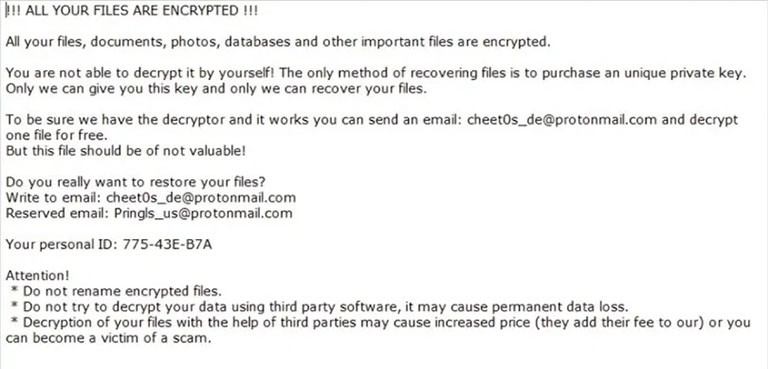
Image of Zeppelin Ransomware's ransom note in plain text. - Source: i2.wp.com
The message it contains is as follows:
|
!!! ALL YOUR FILES ARE ENCRYPTED !!! All your files, documents, photos, databases and other important files are encrypted. You are not able to decrypt it by yourself! The only method of recovering files is to purchase an unique private key. Only we can give you this key and only we can recover your files. To be sure we have the decryptor and it works you can send an email: bad_sysadmin(at)protonmail[.]com and decrypt one file for free. But this file should be of not valuable! Do you really want to restore your files? Write to email:bad_sysadmin(at)protonmail[.]com Your personal ID: Attention! * Do not rename encrypted files. * Do not try to decrypt your data using third party software, it may cause permanent data loss. * Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam. |
The ransomware claims that only a unique decryption key can unlock your files, and if you wish to have it, you must contact the data kidnappers via email. Once you reach out, they'll come back to you with more thorough instructions, like the exact ransom amount, how to send it to them, and so on. The sum is presumed to stay in the range of a number with three or four digits, typically expected to get paid in Bitcoin or some other type of digital currency (cryptocurrency).
Under no circumstances should you pay! Don't forget you're dealing with cybercriminals. These are malicious individuals, who weaseled their way into your machine, locked your files, and now extort you for money. Give nothing to these people, not your time, not your energy, and most definitely not your money. It will be a wasted effort, for they will double-cross you. Once they get your money, they have no more use of you, so they move on to the next victim. Don't allow these malicious extortionists to exploit you.
Zeppelin’s target list
The ransom message is in English, which hints at the infection's chosen targets. Zeppelin's prime objective is to target companies in the United States, Europe, and Canada. Russia and an array of ex-USSR regions seem excluded from the ransomware's target list. Among the excluded, you find Ukraine, Belorussia, and Kazakhstan. The infection manages to affirm whether you're in one of these countries or elsewhere, by poking around your system. It checks the default country code or the configured language in Windows. As soon as it makes its assessment, it acts in accordance – either initiating the attack on your machine or withdrawing from it.
Zeppelin's first steps in targeting your PC include terminating basic level functions. Servers associated with your computer and all of the associated databases are the first to go down. Your backups – gone. The ransomware follows programming to encrypt system boot files, web browser applications, Windows operating system directories, and user files with the goal of preserving system function. It disables recovery and does its best to cripple your machine. Then comes encryption followed by the ransom note display and extortion attempts.
Is Zeppelin shifting gears to better leverage new data backup strategies?
Reports have started to come in about a tactics shift from the Zeppelin ransomware. Instead of encrypting the machine's data after the attack and demanding payment for the decryption, it tries a different approach. Zeppelin has now started to steal files in lieu of locking them. Then they get used to pressure you into paying the data kidnappers. Should that tactic fail, the cybercriminals behind the hack can sell the stolen data on the dark web for a quick profit. That proves quite a lucrative approach to money-making, with both small-time and big-time targets. As established, Zeppelin mainly launches attacks against companies from the IT and healthcare industry. These are entities that are more likely to comply and pay up the ransom compared to home users. That's why they're Zeppelin's dream target. This strategy of targeting large enterprises even has a name in cyber attack culture – 'Big Game Hunting.'

Large-scale victims of ransomware attacks in 2019 in the US, Source: ninjarmm.com
The shift in strategy became necessary after companies began backing up their data to ensure that even if they fell prey to such an attack, they wouldn't get forced into payment. That's why ransomware threats like Zeppelin have taken to this new approach.
How did Zeppelin find its way into your machine?
Ransomware infections, like Zeppelin, are crafty when it comes to infiltration. They're resourceful, and manage to slither past you undetected, making you aware of their presence after they strike.
The infection turns to the usual antics to invade, and the best and easiest method for invasion is via malvertising campaigns. Zeppelin employs large scale spam email campaigns. If you're naïve enough to open suspicious emails and download their contents or click links they urge you to, you'll get stuck with the ransomware. Be wary of emails, whose senders you don't recognize, or you do, but something feels off. Trust your instincts, and always be extra vigilant. Most hackers use legitimate names and logos when it comes to the emails they send out. For example, you might get an email claiming to be from PayPal or Amazon. And, get asked to fill your personal and financial information again for 'verification.' Or, the email may say that terms and conditions have changed, and if you wish to see how, you must download the file attached. Don't fall for this trickery.
There are other methods of invasion it can turn to, as well. It can spread via managed service providers (MSPs). The ransomware attacked IT and healthcare companies and targeted MSPs in an attempt to further the infection process, and infect customers via management software. It can also hitch-hike into your system on a Trojan, fake updaters, or via freeware, corrupted links, and sites. Corrupted torrents provide easy access, too. Approach everything with caution, and you might spot the deception before you suffer the consequences of naivety or lack of attention.
If you do fall for the ransomware's deception, open the "official," "important" or "priority" mail, and download the attachment or click the link, the download and installation of the malware are immediate. It's the same with fake updaters, which instead of installing updates, install malware. Corrupted links, sites, and freeware follow the same pattern. And, as for Trojans, they are even capable of causing chain infections. Keep your anti-virus or anti-spyware software up-to-date, and be on your guard when you browse the web or look through your emails. Don't allow malware to slip past you.
If you wish to avoid the hecticness of dealing with ransomware, create backups for all your files. Also, note that to do these backups on the same machine is futile. You must have them on a separate device so that if your PC falls victim to such a malicious attack, you at least know that your files are safe.








