LockerGoga Aims to Attack Critical Infrastructures Worldwide by Joining Efforts as Part of a Ransomware Trio
Table of Contents
Investigators say that LockerGoga, MegaCortex, and Ryuk ransomware are used in attacks, targeting critical infrastructures across the world.
Ransomware has been causing serious chaos in businesses all over the world. Companies fear that their databases will be devastated by the increasing ransomware attacks, targeting more and more key industries.
Dutch Government Warns of Three Dreadful Ransomware
A report by the National Cyber Security Center in the Netherlands states that at least 1,800 businesses worldwide are affected by ransomware. The report also highlights three file-encrypting malware pieces which are responsible for the massive infection. Those are LockerGoga, MegaCortex and Ryuk ransomware. According to the investigators, these three ransomware threats use the same digital infrastructure and are considered "common forms of ransomware."
Critical Infrastructures Impacted
Although the NCSC said that malware victims were around 1,800, the actual number of targeted companies could be much higher. The names of the affected organizations remained unknown, however, the investigators stated that the ransomware attacks were against critical infrastructures all over the world.
The NCSC found pieces of evidence that Ryuk has been used in ransomware attacks against government, education, and healthcare institutions. One of its huge victims is the Spanish multinational company Prosegur. The attack against it resulted in isolating both internal and external systems, shutting off the communications with its customers.
MegaCortex is known for targeting corporate networks. The ransomware encrypts files, changes the user’s password and threatens to publish the victim’s files if they don't pay the ransom. One of the malware victims was Sophos, who reported that the Emotet or Qakbot Trojans on their networks were infected with MegaCortex.
At the same time, LockerGoga ransomware has been used in several malware attacks against critical infrastructures, such as Altran Technologies in France, the chemical companies Hexion and Momentive in the USA, and Norsk Hydro in Norway, forcing a switch to manual operations.
The Ransomware Trio is Installed via Targeted Attacks
LockerGoga has known to be part of a wave of high profile infections that specifically target large corporations. The group responsible for the attacks have been identified as ones that come out of Russia where the infrastructure is rented from other groups. Moreover, the groups associated with the infrastructure permits targeting of large companies and infecting them with LockerGoga.
Cyber experts revealed that most of the attacks were carried by "a professional criminal organization" in a rather organized manner. While one of the groups was dealing with the penetration efforts, another was deploying the malware. By using variations of TrickBot and Emotet malware threats, vulnerable systems may be infected with LockerGoga leading to it dropping its payload through a backdoor. They payload of LockerGoga may be executed through a renamed version of a system administration tool. The initial spread of LockerGoga commonly takes place through infected terminals to other connected systems in a network.
According to the researchers who analyzed MegaCortex ransomware, hackers were gaining access to a network first and then compromising the Windows domain controller. After compromising the domain controller, the criminals would install Cobalt Strike to open a reverse shell back to them.
After gaining full access to the network, hackers would use PsExec to spread a batch file and the ransomware called winnit.exe to the rest of the computers, as shown in Figure 1 below. Then the batch file would be executed, and all the workstations would be instantly encrypted.
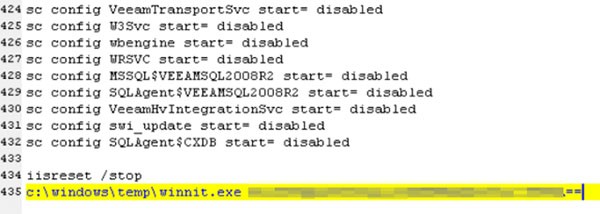
Figure 1. Batch File - Source: Bleepstatic.com
Once the winnit.exe executable is launched, a particular base64 encoded string should be provided so that MegaCortex could extract and inject a DLL into memory. When the ransomware encrypts a file, it will append the .megac0rtx extension to its name and a MEGA-G8= file marker, as shown in Figure 2 below.
According to the researchers, MegaCortex was developed to be monitored by a live hacker and then cleaned up after the execution is completed, similar to the methods utilized by LockerGoga.
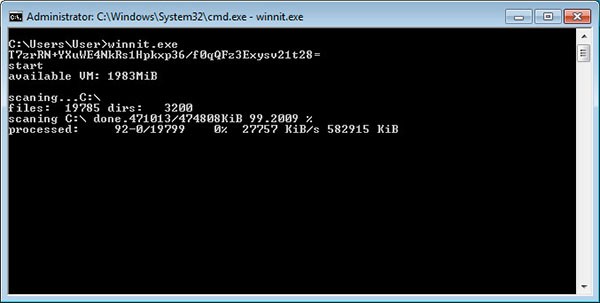
Figure 2. MegaCortex File Encryption - Source: Bleepstatic.com
The ransom note by MegaCortex is called "!!!_READ-ME_!!!.txt" and it is saved on the victim's desktop. It contains emails of the attackers and payment instructions. The ransom amounts usually range from 2-3 bitcoins to 600 BTC, as shown in Figure 3 below.
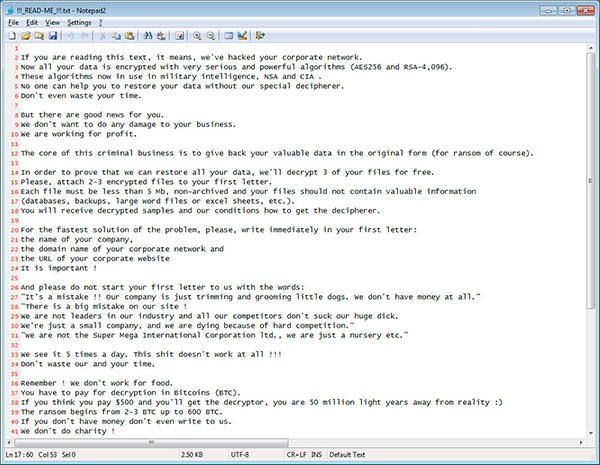
Figure 3. MegaCortex Ransom Note - Source: Bleepstatic.com
After analyzing Ryuk ransomware, the security experts stated that it uses the Wake-on-Lan feature (a hardware feature that allows a powered down a device to be woken up, or powered on, by sending a special network packet to it) to turn on powered off devices on a compromised network to have greater success encrypting them. Once Ryuk is executed, it will spawn subprocesses with the argument '8 LAN', as shown in Figure 4 below.
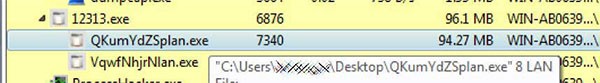
Figure 4. Spawning Subprocesses With the Argument '8 LAN' - Source: Bleepstatic.com
Then, the ransomware will scan the device's ARP table and check if the entries are part of the private IP address subnets of "10.", "172.16.", and "192.168", as shown in Figure 5 below. One aspect to also note is the fact that LockerGoga is able to relocate issues command line to a TEMP folder and rename itself to evade detection essentially. LockerGoga's also has child processes that have the task of encrypting data, which is a method that other ransomware threats have adopted.
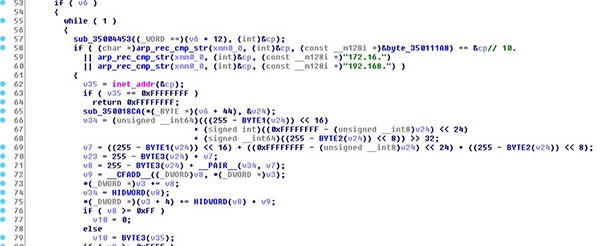
Figure 5. Checking for Private Network - Source: Bleepstatic.com
In case the ARP entry is part of any of those networks, Ryuk ransomware will send a Wake-on-Lan (WoL) packet to the device's MAC address to have it power up. The WoL request comes in the form of a 'magic packet' which contains 'FF FF FF FF FF FF FF FF', as shown in Figure 6 below.
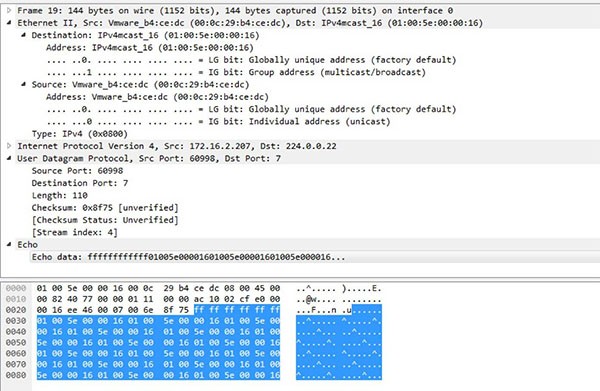
Figure 6. Ryuk Ransomware Sending a WoL Packet - Source: Bleepstatic.com
In case the WoL request was successful, Ryuk will attempt to mount the remote device's C$ administrative share. Once the share is mounted, the remote computer's drive will also be encrypted.
The associated email addresses with Ryuk ransomware are eliasmarco@tutanota.com and CamdenScott@protonmail.com, included in its ransom note, as shown in Figure 7 below.
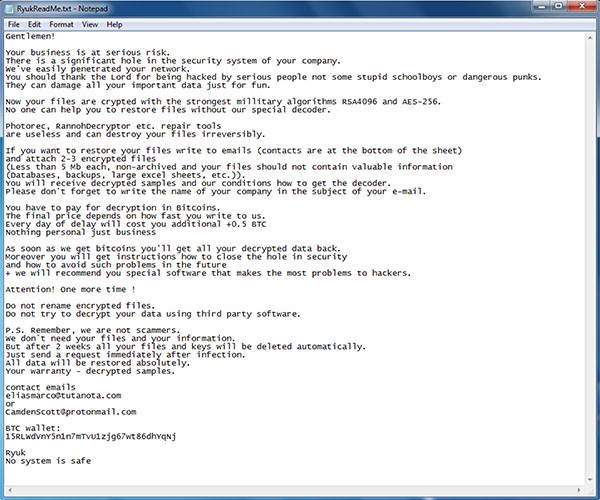
Figure 7. Ryuk Ransom Note - Source: Zdnet.com
LockerGoga, which has been leveraged by virtually the same group of hackers, was first spotted in January 2019 when the ransomware hit the systems of the French company Altran Technologies. Due to this attack, the company's network had to be shut down immediately.
According to the cyber experts, LockerGoga ransomware usually targets DOC, DOT, WBK, DOCX, DOTX, DOCB, XLM, XLSX, XLTX, XLSB, XLW, PPT, POT, PPS, PPTX, POTX, PPSX, SLDX, and PDF files. However, if the malware is launched with the '-w' command-line argument, it will attack all file types.
Other switches supported are '-k' and '-m' for base 64 encoding and for providing the email addresses included in the ransom note.
After encrypting the targeted files, LockerGoga will append the .locked extension to them. This means that a file called test.jpg would be first encrypted and then renamed to test.jpg.locked, as shown in Figure 8 below.
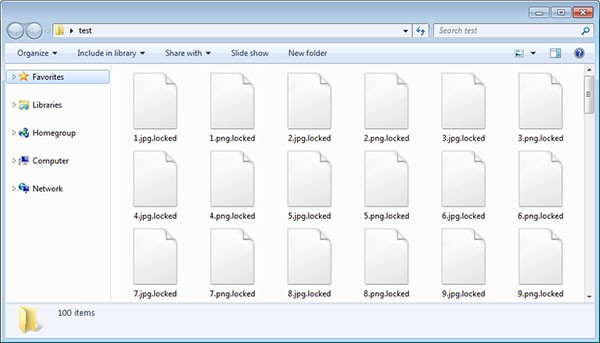
Figure 8. LockerGoga Encrypted Files - Source: Bleepstatic.com
When the ransomware encrypts the files on the computer, it will drop a ransom note called README-NOW.txt on the desktop, which includes email addresses for payment instructions in exchange for a decryption key, as shown in Figure 9 below.
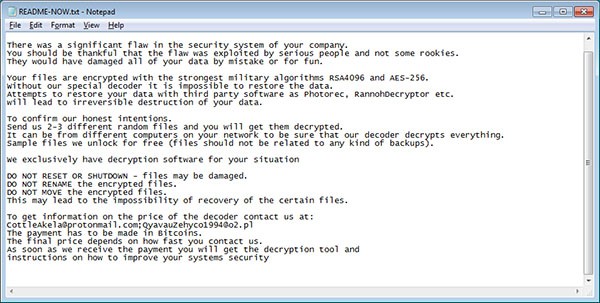
Figure 9. LockerGoga Ransom Note - Source: Bleepstatic.com
An interesting fact about LockerGoga ransomware is that it uses a valid certificate which increases the chances of its deployment on the victim's computer without raising any suspicion. However, if you pay attention to the Windows alert asking for authorization of the certificate, you would notice that something is wrong because it is for a host process for Windows Services and the signature is from MIKL Limited (an IT consultancy firm incorporated in the UK on December 17, 2014), as shown in Figure 10 below.
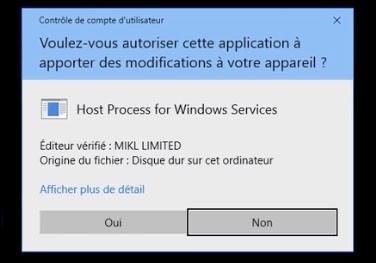
Figure 10. LockerGoga Certificate - Source: Bleepstatic.com
According to the researchers, the known file samples for LockerGoga ransomware so far, are 'worker' and 'worker32', and the ransomware launches a process with a name similar to what Microsoft uses for its Windows Services, such as 'svch0st' or 'svchub.'
The associated email addresses with LockerGoga ransomware are CottleAkela@protonmail.com and QyavauZehyco1994@o2.pl, included in its ransom note, as shown in Figure 11 below.
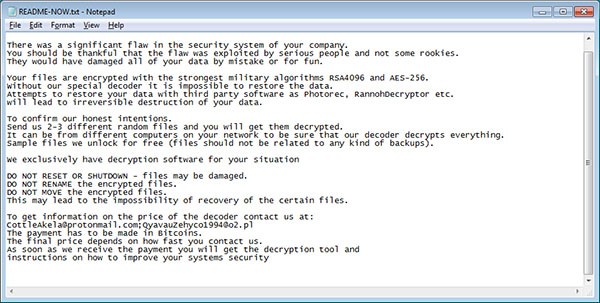
Figure 11. LockerGoga Ransom Note - Source: Bleepstatic.com
Ransomware Attacks Continue to Increase
The fact that three malware pieces were enough to shut down big companies' operations is more than disturbing. According to the security experts, the success of the ransomware attacks makes the attackers even more determined to achieve their goals, while the targeted businesses keep increasing.
Spreading ransomware on corporate victims is far from being the worst part of an intrusion. In some cases, file encryption is preceded by data exfiltration, which could be sold to other hackers or used for committing acts of sabotage. So, as long as the victims pay the ransom, the attacks will continue, and the only thing left for the companies is to increase their online security, cyber experts warn.





