Coronavirus Phishing Scams Decline After March Peak
As soon as the Coronavirus pandemic started, and people became home-bound, social distancing, working from home, and receiving online classes, crooks had a field day. Cybercrime spiked, and most cyber-attack campaigns began to revolve around COVID-19.
There were fake maps and bogus websites, crafted by crooks. There were fraudulent apps created to further the spread of malware. Hackers used every aspect of the pandemic for their agenda – to infect as many machines as possible. Ransomware attacks became rampant, and banking Trojans were on the rise, as well as infections that had been on a steady decline in usage suddenly got revived.
Table of Contents
Capitalizing on Coronavirus
Cybercriminals used a variety of tactics when it came to spreading infections. As stated, they used corrupted sites, links, apps, maps, and so on. But, probably, the most effective manner of spreading remains via malvertising campaigns. Phishing emails got sent out to businesses, government, and healthcare establishments, private individuals. Even if only a fraction of the emails did their job and infected the device with malware, it was still a large percentage of victims to spy on, steal from, or extort.
Here is an example of one such email from a phishing campaign, spotted in the UK.
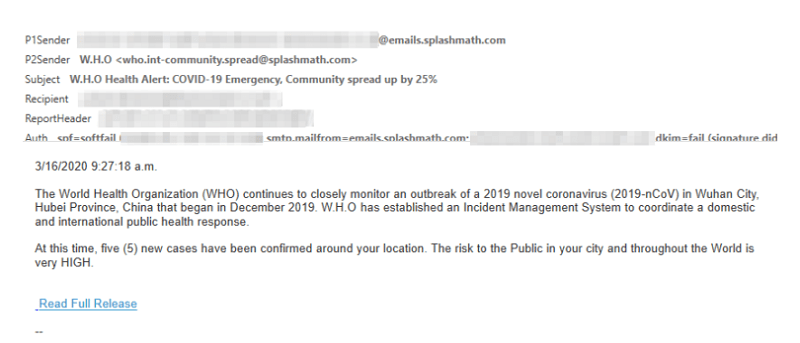
Example Coronavirus phishing email. Source: Microsoft
And, here's an example of a US phishing email that uses Coronavirus as a lure:
Example Coronavirus phishing email. Source: Microsoft
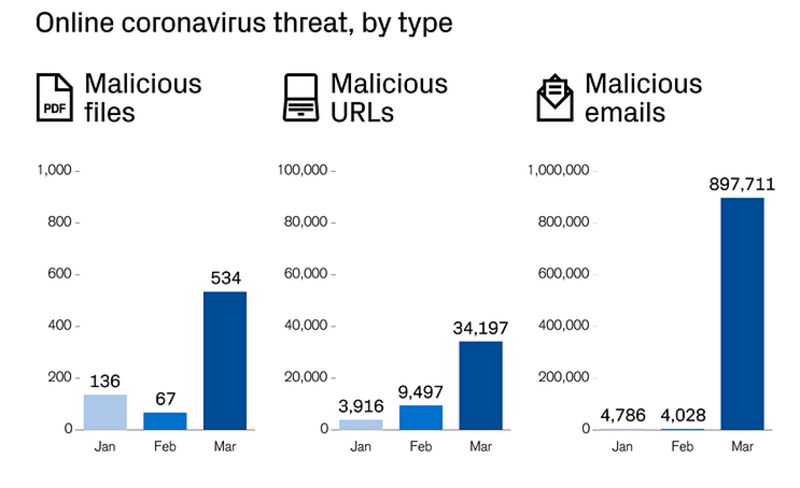
The first two weeks of March were the strongest for cyber-attackers with their newly-modified scams. As you can tell from the chart below, crooks tried to spread an array of infections, using Coronavirus as a bait.
The trend of COVID-19-related attacks after WHO brands it a global emergency. Source: Microsoft
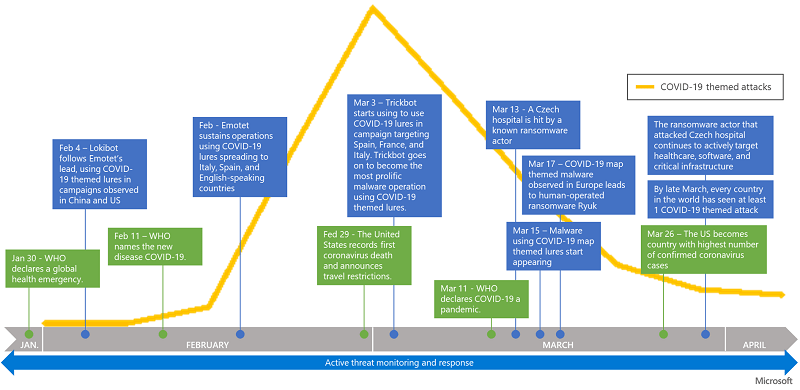
The peak of phishing campaigns spreading Coronavirus-related emails was in March. The scam was still going strong in April, but experts have noted that it has started to decline after that.
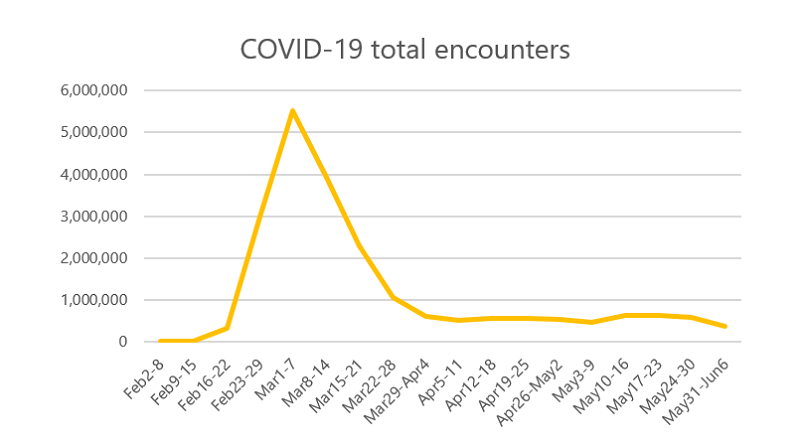
Spike in Coronavirus-themed campaigns in March, displaying a later decline. Source: Microsoft
Phishing Campaigns Using COVID-19 Lures Decrease
The Microsoft Threat Protection Intelligence Team made a recent report stating that phishing campaigns and other COVID-19-related shams have diminished in the past few weeks. Even more so than that, these experts claimed that these types of Coronavirus scams had never been a dominant threat.
The Microsoft researchers acknowledged that there had been a notable increase in COVID-19-connected scams, using the pandemic to bait unsuspecting users into allowing malware into their machines. But they also continued to account that these malicious campaigns made up only a small percentage of the threats observed in the last four months.
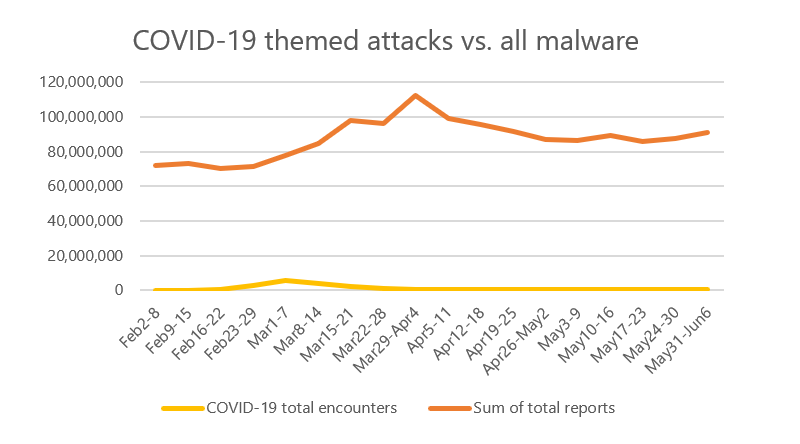
Coronavirus-themed malware campaigns in comparison to all other malware attacks. Source: Microsoft
As you can see from the chart above, Coronavirus attacks are not nearly as staggering as they initially got made out to be. Instead, they represent about 2% of all cyberattacks for every month observed by Microsoft.
These Microsoft experts inspected online fraud trends starting from February until now. They concluded that crooks began turning to Coronavirus lures after February 11, when the World Health Organization (WHO) declared COVID-19 a global health emergency.
Microsoft's team notes that the spike is easily explainable as hackers feed off current events, and adapt their scams to reflect what is happening locally and globally. They pick and choose to use whichever suits them best, either a global occurrence or a local one. Coronavirus initially got presented by the media as something that should not cause much concern until all that changed. Media outlets talked about the pandemic comparing it to the flu, and undermining the damage it can do until they didn't. It seemed as though overnight, the severity of the virus shifted.
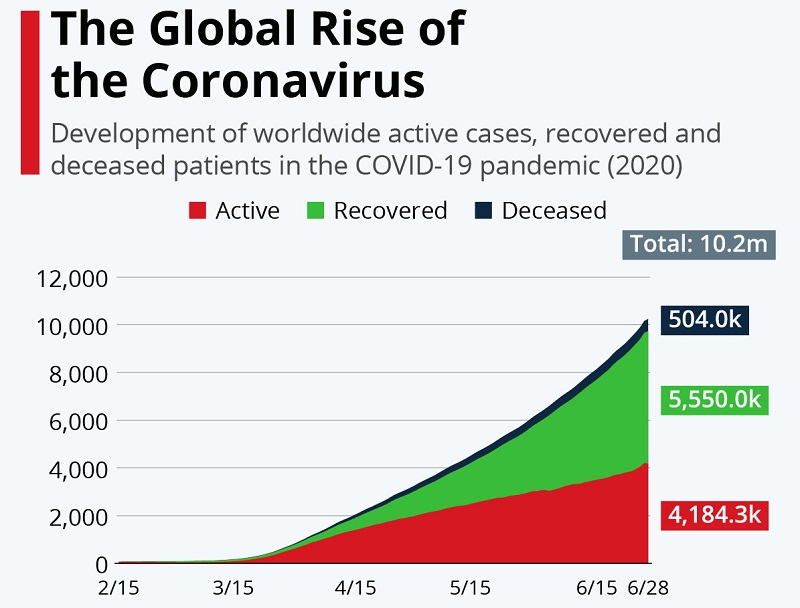
The global rise of Coronavirus. Source: cdn.statcdn.com
All of a sudden, it was something of extreme importance, and since it was such a new threat, a lot of people lacked information on it. As individuals were hungry for data on COVID-19 and looking to experts, healthcare, and media representatives, cybercriminals saw an opportunity.
Domains and hostnames started to get made with 'Corona,' included in the name, to mind-boggling numbers daily. Some made by legitimate sources, others by people with nefarious reasons.
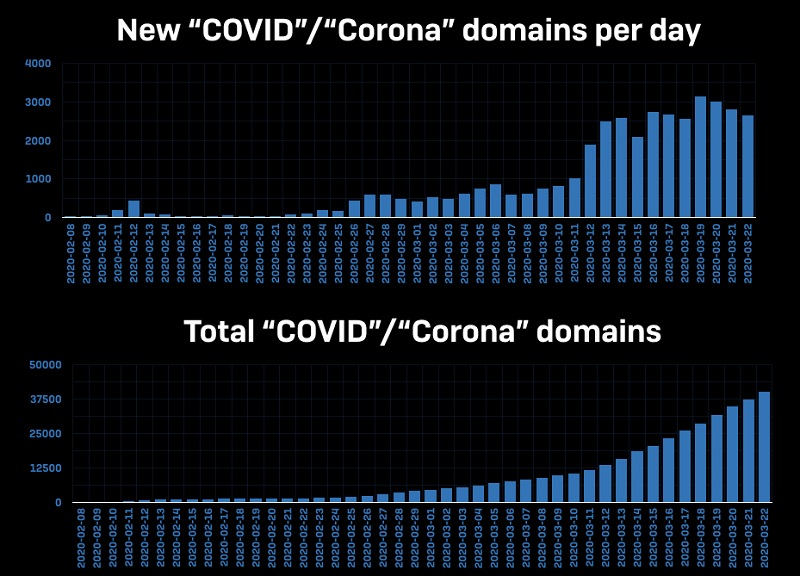
'Corona' domains per day - newly-created ones, and overall number. Source: news.sophos
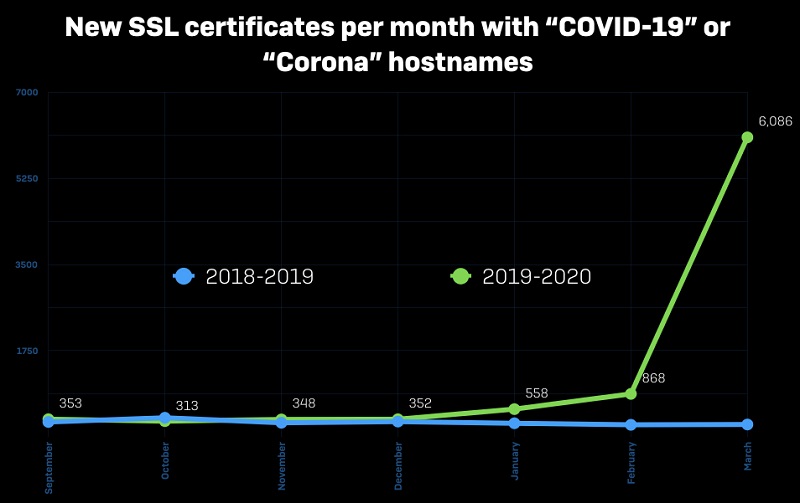
Newly-crafted certificates with the name COVID-19 or Corona hostnames, in March. Source: news.sophos
Carefully Crafted Attacks
Crooks exploited that COVID-19 curiosity for their gain, and modified their attacks to contain various Coronavirus 'information.' Many of their malvertising campaigns included emails claiming to come from government officials providing news on the development of the Coronavirus situation. They mimicked emails from official sources like the WHO and The Centers for Disease Control (CDC). Impostors became successful in tricking users into allowing malware on their devices by thinking they were downloading essential documents or clicking sites that contained crucial data.
The global impact of Coronavirus, the fear, and the ever-present hunger of information revolving COVID-19, made it much easier for hackers to invade your computers.
Cyber-attackers modified their emails to suit the global state of the pandemic and altered them according to the news cycle in the location they were targeting. For example, the UK attacks spiked after the first death by the virus received news coverage. Then, again, after it became known that their prime minister tested positive for COVID-19. The USA suffered a spike after they revealed the first death by the virus, as well. Also, after their announcement to ban travel to Europe.
Below you can see detailed charts on the COVID-19 themed attacks in the UK and the USA.
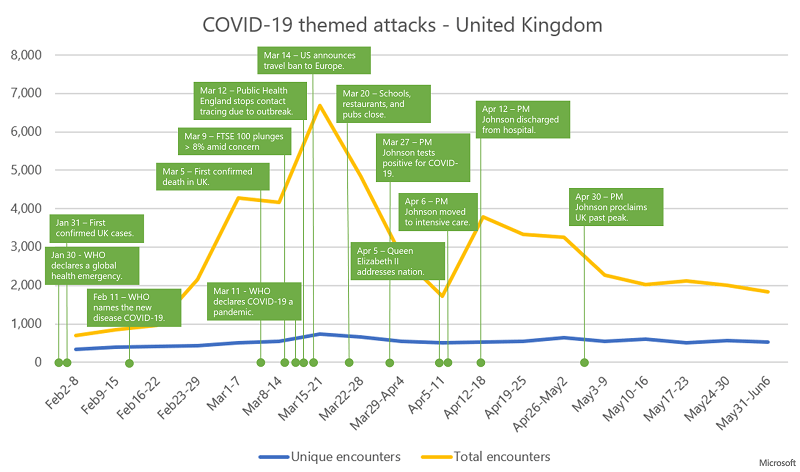
The trend of Coronavirus-themed attacks in the UK with unique encounters (distinct malware files) and total encounters (number of times the files are detected). Source: Microsoft
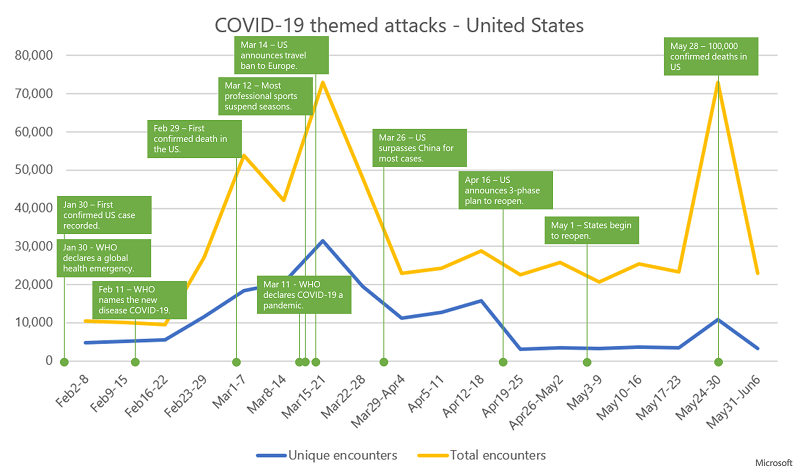
The trend of Coronavirus-themed attacks in the USA with unique encounters (distinct malware files) and total encounters (number of times the files are detected). Source: Microsoft
Coronavirus Malvertising Campaigns Remain a Threat
Make no mistake! Though these attacks display a decline, don't get duped! That does not mean they'll get gone altogether. They're likely to continue still. The Microsoft researchers state that as long as Coronavirus is on the news, they expect the attacks won't cease. Until there are no more victims of COVID-19, hackers will proceed to modify and adapt their scams to target users.
For example, reports have come out that crooks have begun crafting their shams to suit the times. Instead of offering emails that contain data on the pandemic, like maps and charts of the affected areas, deaths, and recoveries, they have switched their focus to layoffs, furloughs, and payouts. There was a recent scam about resumes and medical leave malware that tricked users into downloading attachments, which they shouldn't have.
If you wish to avoid falling victim to scams, Coronavirus-centered or not, be wary. Exercise vigilance when online. Avoid visiting suspicious websites or clicking links that seem off. Don't download an attachment without verifying its legitimacy. It's always better to be safe than sorry.
Verify every email you receive and thoroughly check whether it deserves your trust. Look for red flags – is the grammar okay? Can you find punctuation or spelling mistakes, do you recognize the sender, is there a chance it's a spoofed email? Be thorough, be vigilant, and your caution might pay off. Avoid falling prey to malicious cybercriminals seeking to exploit you.








