Coronavirus-Related Malware Lurking in Resumes and Medical Leave Files

Cyberattackers turn to every tool in their box of tricks to dupe you into allowing malware into your system. After corrupting a variety of files, maps, links, and whatnot connected to COVID-19, now they've turned to resumes and medical leave forms.
Due to Coronavirus, a multitude of individuals lost their jobs. Others have gotten sick. So, it's hardly surprising that the crooks have decided to switch their shenanigans to the use of these devices. There's a lot of people currently applying for both – resumes for work and medical leave requests. The malicious cybercriminals hope to slip through the cracks and infiltrate your machine.
Security experts have noticed an increase in the spread of banking Trojans and info-stealers. Crooks have begun to use the sham, as mentioned earlier, of corrupted CV and leave forms to spread the malicious tools. In the current pandemic state of the world, it seems to prove a somewhat effective strategy of infiltration.
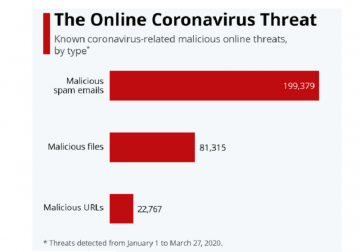
A chart of Coronavirus-related malicious threats by type, from January 01 to March 27. Source: Trend Micro
Having survived the first wave of COVID-19, and hoping to avoid a second one, more and more businesses, establishments and organizations, dare to reopen their doors. That reopening has triggered cybercriminals into amping up their attacks. Malware experts have estimated that, in comparison to March and April, May has suffered a 16% increase in overall cyber attacks. A peculiar fact is that May has seen a 7% decline in COVID-19-related attacks compared to April.
Table of Contents
A Truly Bad Record to Hold
The American network, CNN, reported that by the end of May, over 40 million Americans have filed for first-time unemployment benefits. A move, which directly correlates to the economic freeze in March, brought upon by Coronavirus. That's a mind-boggling number. This pandemic has led to more people filing for unemployment than they did during the Great Depression in the 1930s – one in four people.
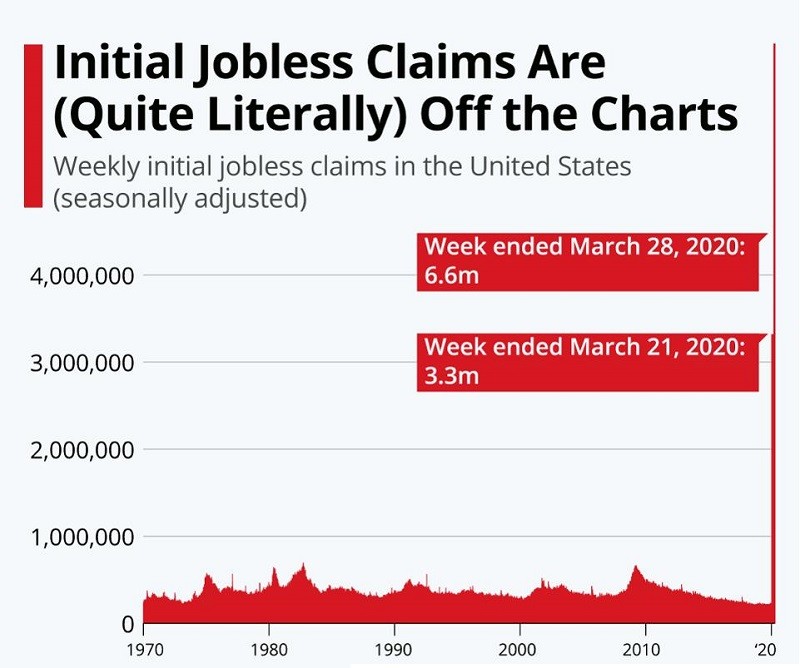
US unemployment claims chart from 1970 until March 28, 2020. Source: US Department of Labor
The misfortune of those 40 million people gave an idea to hackers. Cyber experts report that 250 new domains, containing the word 'employment' popped up in May. From all these domains, about 7% got classified as malicious, and 9% got deemed suspicious.
The US displays an increase in CV-themed campaigns. 1 out of 450 malicious files turned out to be a CV-related scam.
Researchers reveal a recent one of these shams to push the Zloader malware into your PC. Zloader is a banking Trojan, which is a variant of the notorious Zeus malware.
Once the infection makes its way into the victims' machines, the crooks behind it proceed to steal all private information, including credit card and bank account credentials, personal details like email addresses, phone numbers, pictures, videos. The hacker gets a hold of everything you keep on your device!
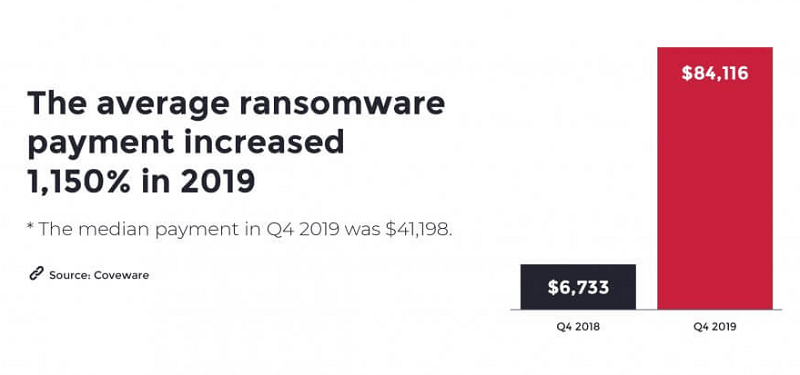
Example document. Source: Checkpoint.com
'About a Job' – That's How They Get You
The attackers send out corrupted 'xls' files. They name them 'applying for a job,' 'regarding a job,' and so on. In other words, the files carry names that lead you to believe they're actual CVs. If you get tricked into opening one, you get asked to 'enable content.' If you do that, a malicious macro starts running and downloads the final payload. Once the infiltration finishes, the people behind the malware have free reign over your system and can carry out financial transactions on your machine.

An example email, directing you to the attached CV. Source: Checkpoint.com
Experts report that some emails arrive with a subject line 'CV from China.' They contained an ISO file (CV.iso), which, when downloaded and opened, dropped a malicious 'exe' file (CV.exe). It's that EXE file that runs an Info-stealing malware on your device.
As already stated, users aren't only suffering from fake CVs that drop malware onto their machines. Crooks have resorted to using false medical leave forms, as well.
Campaigns have gotten spotted using such forms to deliver the Icedid malware, which is another banking Trojan set to steal your financial information.
Attackers used a variety of domains, like 'medical-center.space ' or 'covid-agency.space' to send emails with subject lines like 'The following is a new Employee Request Form for leave within the Family and Medical Leave Act (FMLA).' Emails, which carried documents with names like 'COVID-19 FLMA CENTER.doc.' Every bit of their sham emails get crafted to best intrigue you into opening them, and following their instructions – download the attached file and open it. If you do, you get stuck with malware. In most cases, it ends up being a banking Trojan, like Trickbot.
Let’s Talk Numbers
In May, there have been 158,000 Coronavirus-related attacks each week. That may seem like a staggering number, but, in actuality, it's lower than the attacks suffered in April. You can see a visual representation below.
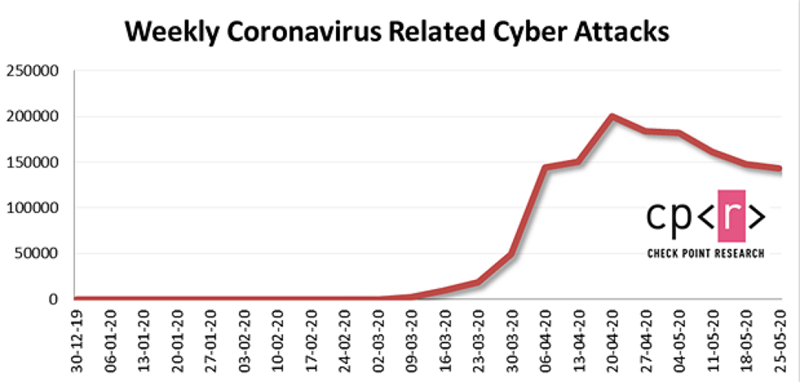
A chart depicting the spike and decline of Coronavirus-related attacks from December until May. Source: Checkpoint.com
In a mere four weeks, 10,704 newly-minted Coronavirus-related domains got registered. Upon closer inspection, experts branded 2.5% (268) of them as malicious, and 1.6% (171) suspicious.
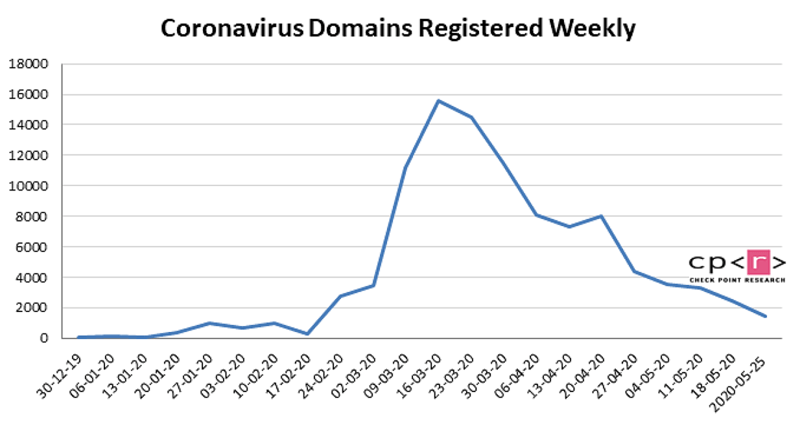
A chart depicting the number of Coronavirus-related domain registrations per week from December until May. Source: Checkpoint.com
How to Avoid Sham Emails and Stay out of Trouble
Be mindful that most scammers often spoof legitimate brands, sources, and institutions. They mimic a real logo, use domains you might recognize, and so on. They create lookalike accounts, but they aren't that difficult to spot if you're thorough.
Look for spelling and grammatical errors, that's one of the most straightforward telltale signs that something is a lie. Does anything seem off – some color in the logo, a letter missing from a title? Every little detail matters.
If you receive an email that looks off, consider whether you were expecting to receive it that day or if it caught you by surprise. Is it a known or unknown sender? If you open the email and see that it urges you into an action of some kind, that should raise a red flag for you. Emails that prompt you to click a link or download an attachment deserve extra scrutiny.
Also, be mindful of the 'special offer' emails you receive. They used to revolve around winning a new iPhone or getting a coupon code for an online sale. Nowadays, most offers are for COVID-19 'cures' that, of course, are nothing more than a sham.
Look at every email with a grain of salt, and be extra attentive before following any instructions it may contain. Even a little extra caution can save you a whirl of grievances.