DeathRansom: Ransomware Hellbent on Killing Files on Infected PCs via Encryption
Ransomware has turned into such a global problem for computer users and businesses, victims of recent threats have turned to budgeting for an attack so they can pay the demanded ransom and get their computer back to working order without delay. Ransomware threats, such as DeathRansom, are more sophisticated and relentless in their quest to extort money from victims, leaving them without many options for recourse.
DeathRansom is a ransomware threat that encrypts your data and demands a ransom to recover it. Victims report they are required to pay in cryptocurrency in a specific time frame, which, if not met, would result in complete data loss. However, it's not suggested that you follow through with these demands, since they most likely will be ineffective, and could result not only in you wasting money for nothing but also putting your computer in danger of getting infected with other threats.
Table of Contents
What DeathRansom Does
What's curious about this particular ransomware threat is that it didn't encrypt the victim's files... or at least, not at first. It turns out that the initial version of DeathRansom ransomware was just pretending to encrypt data, and affected users were able to make their files usable again. In a perfect world, all a victimized computer user had to do was remove the .wctc extension on each file. An example of such an encoded file would be '1.docx.wctc'.
Sadly, simply changing the file extension of files affected by DeathRansom is not the solution any longer. Ever since the number of DeathRansom's victims increased, the threat changed its tactics and is now able to encrypt the personal files of its victims but without the inclusion of the .wctc extension. So far, the only way to find out if DeathRansom ransomware has encrypted your data is to open the affected file and check the marker at the end of the encryption. According to reports, the file marker should read 'AB EF CD AB.'
This malicious DeathRansom threat targets Microsoft Windows users. Right after infiltration, the threat encrypts all files on the victim's device, except for ones, whose full path names have the following strings:
- programdata
- $recycle.bin
- program files
- windows
- all users
- appdata
- read_me.txt
- autoexec.bat
- desktop.ini
- autorun.inf
- ntuser.dat
- iconcache.db
- bootsect.bak
- boot.ini
- ntuser.dat.log
- thumbs.db
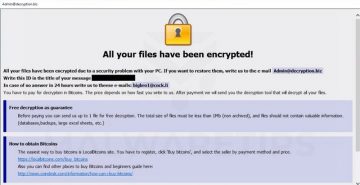
After the file encryption process, the ransomware will create a text file (read_me.txt) in every folder where there's encrypted data, so the victim can easily see it.
The Ransom Note
The read_me.txt file is a ransom note left by the creators of DeathRansom. As already mentioned, ransomware's 'updated' version is now able to encrypt data but without appending any extensions. It appears that slight changes were made to the ransom note as well. This message informs the user that their files got encrypted, and if they don't want to get them permanently deleted, they have 12 hours to follow the given instructions and pay in cryptocurrency.
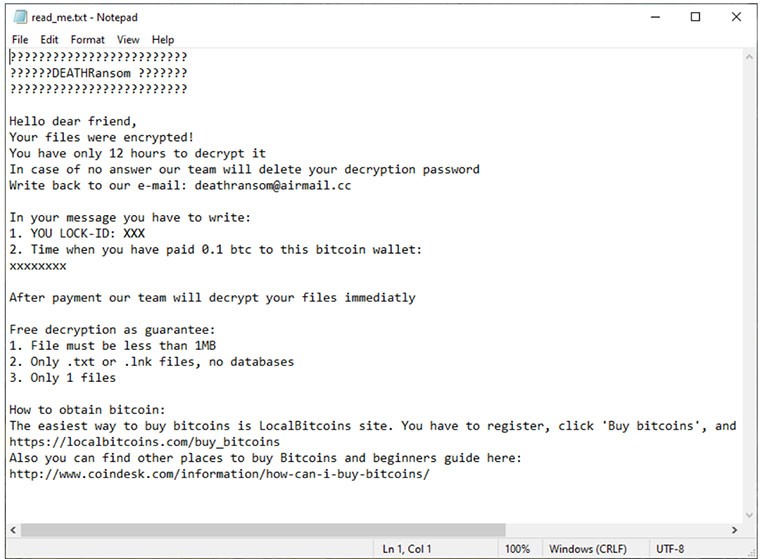
The note includes a personal LOCK-ID and the number of the bitcoin wallet you need to send 0.1 BTC to. Victims are instructed to write an email to the given address and include the LOCK-ID and the time of payment.
Interestingly, they offer to decrypt one file of your choosing for free, to prove they have a decryption tool and gain your trust. Other than the specified time frame and amount of money you have to pay, what's also new in the ransom note is the given specifications for the 'test file' you'll be sending. It has to be:
- no larger than 1MB
- either a .txt or .lnk file, no databases
Lastly, the ransom note provides sources from which you can buy bitcoins.
How Does Ransomware Spread
DeathRansom most likely spreads like other ransomware out there. Such methods include:
- deceptive spam emails
- torrent files
- malicious ads
- fake update messages
- unreliable third-party installations
- Trojan horse viruses
Traditionally, it's pretty easy for computer users to be misled by an email with an attractive headline. Such spam campaigns may try to scare users with titles like 'Your bank account will get terminated!!!'. Computer security experts will typically warn computers to not rush into opening every email you see or ones that have an enticing subject line or appear to come from your bank or favorite social media site. In some cases, messages might pretend to be from a well-known company or one of the largest social media networks, like Facebook or Twitter. It is best to check the email of the sender and compare it with the official address of the actual company. Then, you'll know for sure if the email is legitimate or not.
Malware researchers commonly recommend getting software updates from trustworthy sources only, rather than clicking on a random pop-up that wants you to follow a shady link.
Users are known to overlook essential details during an installation process. To ensure that computer users don't accidentally install malware along with a desired program, it’s best that they look out for additional software included in the installer. Malware is known to disguise itself as optional programs, so it's best to opt-out of such unfamiliar installations.
DeathRansom Removal and Data Recovery
Even if the creators of DeathRansom urge contacting them and pay for their decryption services, it’s best to avoid complying with their demands. Instead, specialists recommend getting rid of the threat entirely. For this purpose, the use of reliable software, which can safely detect and remove DeathRansom, is suggested.
As for the data recovery, the best option is to rely on file backups that are kept on cloud databases or external devices. Other than that, advanced decryption tools may be found from trustworthy sources, which work for this ransomware in particular. The main thing is, there are options apart from what the developers of DeathRansom may explain. It's best to think it all through before deciding what to do because there is no guarantee all encrypted files will be recovered if one chooses to abide by the ransomware's demands.