CoronaVirus Ransomware Emerges Amid Mass Panic to Cloak KPOT Malware Installation

It's evident that cyber attackers see the ongoing mass panic surrounding the COVID-19 pandemic as an opportunity to profit by delivering nasty malware. First discovered by MalwareHunterTeam, the CoronaVirus ransomware is a new strain that uses Coronavirus-related scare tactics, aiming to infect the machines of its unsuspecting victims. However, this particular threat is different from your typical ransomware.
Attackers use CoronaVirus ransomware as a distraction from KPOT Trojan installation
It appears that cyber criminals' master plan is to distribute the CoronaVirus ransomware and the KPOT Trojan simultaneously. Once CoronaVirus infiltrates the machine, a Trojan called KPOT gets downloaded in the background by the ransomware. KPOT is a nasty Trojan infection that has been circulating for several years now, programmed to steal sensitive personal information like passwords and financial credentials. After its successful installation, the Trojan begins to steal passwords, cookies, crypto wallets, banking accounts, credit card numbers, etc.
Meanwhile, the CoronaVirus ransomware starts file encryption and leaves a ransom note. The majority of researchers suggest that the ransom component of the attack is merely a distraction from KPOT's installation. This suggestion leads to the belief that the CoronaVirus ransomware is actually a wiper, a program that “wipes” data from an infected computer. If that proves to be true, there won't be a chance to retrieve the lost data, even if the victim decides to pay the ransom demanded by the attackers.
CoronaVirus ransomware spreads through a bogus app
Attackers distribute the ransomware through a website that poses as the legitimate Windows system utility page WiseCleaner.com. Users can easily get tricked if they fail to distinguish the bogus site from the real one.
Even though the downloads on this site aren't active, they can distribute a file called WSHSetup.exe. The file in question acts as a downloader for both threats – CoronaVirus, and KPOT.
After its execution, the program will download two files:
- file1.exe
- file2.exe
The first file contains the "Infostealing" KPOT Trojan. The second one is the CoronaVirus ransomware, responsible for the file encryption.
List of targeted file's extensions:
.bak, .bat, .doc, .jpg, .jpe, .txt, .tex, .dbf, .xls, .cry, .xml, .vsd, .pdf, .csv, .bmp, .tif, .tax, .gif, .gbr, .png, .mdb, .mdf, .sdf, .dwg, .dxf, .dgn, .stl, .gho, .ppt, .acc, .vpd, .odt, .ods, .rar, .zip, .cpp, .pas, .asm, .rtf, .lic, .avi, .mov, .vbs, .erf, .epf, .mxl, .cfu, .mht, .bak, .old
After the encryption is finished, a document (Fig.1) will be dropped on the user's desktop, saying the following:
"CORONAVIRUS is there
All your file are crypted.
Your computer is temporarily blocked on several levels.
Applying strong military secret encryption algorithm.
To assist in decrypting your files, you must do the following:
1. Pay 0.008 btc to Bitcoin wallet bc1q6ryyex33jxgr946u3jyre66uey07e2xy3v2cah
or purchase the receipt Bitcoin;
2. Contact us by e-mail: coronaVi2022@protonmail.ch and tell us this your
unique ID: - 56GH8709EE123KJK903IUMN018DGF71E
and send the link to Bitcoin transaction generated or Bitcoin check number.
After all this, you get in your email the following:
1. Instructions and software to unlock your computer
2. Program - decryptor of your files.
Donations to the US presidential elections are accepted around the clock.
Desine sperare qui hic intras! [Wait to payment timeout 25 - 40 min]"
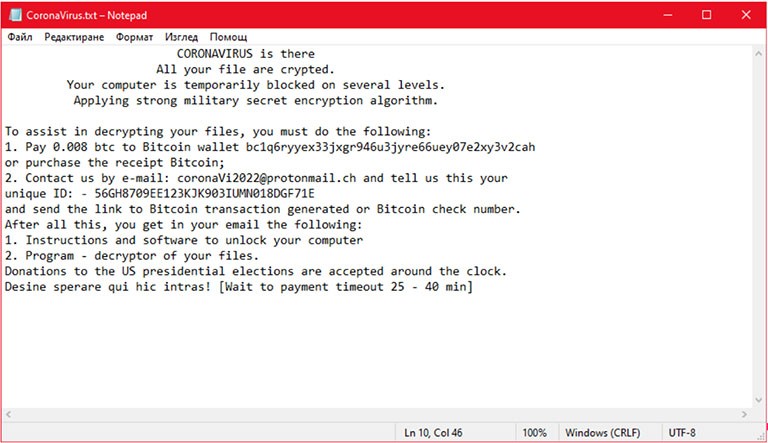
Figure 1: Screenshot of the ransom note left by the CoronaVirus ransomware
Symptoms that indicate the presence of CoronaVirus on your computer
- The system disk drive is renamed to "CoronaVirus (C:)."
- Encrypted files are renamed to the attacker's email address "coronaVi2022@protonmail.ch."
- It's possible for the email address to be prepended multiple times in the file name.
- Ransomware's process name is seen on Windows Task Manager as "xglhdi.exe," though process name may vary.
- A ransom note is presented on the victim's desktop, named CoronaVirus.txt.
- Even on reboot, the ransomware will display the same ransom note before Windows is loaded. Once the supposed payment timeout is up, another similar message will appear. Only this time, the timeframe is 15 minutes. After the time is up, it will boot back to Windows, and the original ransom note will be displayed again.
Note: The CoronaVirus ransomware also goes by the name CoronaVi22.
If you've fallen victim to the CoronaVirus ransomware, you should not worry too much about the $50 ransom. Instead, you should log into an uninfected device and reset every password you can think of, as soon as possible! Make sure to go through your banking and social media accounts, personal emails, or any other place where you've linked your credit card or have financial information saved. This way, you have a chance to protect your sensitive data.








