Phishing Campaigns Use COVID-19 and FedEx, DHL, and UPS Fake Issues to Spread Malware

We are living through a pandemic. Coronavirus, or more precisely COVID-19, has gripped the world and caused ripples globally.
People get encouraged to stay home and implement social distancing in their daily routines. Government officials and representatives from the World Health Organization (WHO) and the Centers for Disease Control and Prevention (CDC) urge people to avoid contact with others as much as they can help it. Only essential businesses remain open – grocery shops, pharmacies, banks. Other shops that tend to entice us into spending our money there remain closed for the time being. That leads to an increase in online shopping. It's not only a tool that allows you to restock and resupply items deemed 'non-essential' (hair dye, lacquer, books, board games), but it's also a welcomed distraction. Not to mention, all the restaurants, coffee houses, and other various establishments that offer home deliveries that people can take advantage of nowadays. Since so many people online shop and use delivery services at the same time, naturally, it has drawn the attention of cybercriminals.
Malicious individuals with nefarious purposes chose to focus on online shoppers. There now exists a scam revolving around the most well-known couriers responsible for delivering packages – FedEx, UPS, and DHL.
Cyber crooks have decided to capitalize on the situation by crafting scams using Coronavirus delivery issues. They sent out emails that claim to revolve around people's deliveries, and state that due to Coronavirus complications, something has changed – dates, delivery method, prices. They attach a malicious document or plant a corrupted link, and ask the email recipient to click and view for themselves. If they do press the link or download the attachment, they unwittingly invite malware into their system. It's the simplest of scams, but efficient nonetheless.
These phishing scams exploit the COVID-19 pandemic to line their pockets.
The Tricks of the Trade.
The cybercriminals craft their emails by filling them with lies while making sure they're believable ones. The more palatable their claims, the more people fall for it. A lot of the emails they send out, claim that a package has gotten withheld due to the pandemic. They say that the government lock-down is to blame for the delay. One such deceitful email supposedly comes from DHL and blames the Coronavirus crisis for the unexpected holding of the package. The email then urges the recipient to make the necessary corrections to the attachment shipping document. As soon as that attachment gets opened, the Bsymem Trojan lands on your machine, and you're in trouble. Another email offers the same story with the same request but states that it comes from FedEx.
Fake delivery notification email. Source: media.kasperskydaily.com
Other emails claim to come from UPS and offer a slightly different story. Supposedly, the email comes from UPS customer service, and it informs you that your package remains at the facility, ready for pick up. The email offers the Coronavirus outbreak as an excuse for the inconvenience, and urges you to open the attachment it contains, so you can see the instructions on how to pick up your package. The attachment you get asked to click on is, in actuality, a malicious executable, which downloads and installs the Remcos Remote Access Trojan (RAT). As soon as the RAT settles on your system, the person behind it has access to everything you have on your computer.
Some scammers have resorted to attaching images in their emails. Well, at least what appears to be an image. The attachment they urge you to open is a 'jpg' file. To spike your curiosity, they often add an image into their email, making sure it's illegible, thus ensuring you'll have to open the 'jpg' file to check out the information on the image. They claim it's a receipt, delivery information, or anything else that might get you to want to check it out. The attachment is not a 'jpg' file, but an executable ACE (compressed file format) archive containing the spyware program Noon.
Bogus delivery service email with an archive with a double extension. Source: media.kasperskydaily.com
These crooks also exploit the government by using it to excuse 'delays.' One of the emails going around claims the government banned all import of goods, and therefore, your package got returned to sender. If you wish to get your item re-shipped, all you get asked to do is to open the attachment the email has. Presumably, that attachment contains an order tracking number and would allow you to request a reshipment after virus-related health restrictions subside. In reality, it has malware. Opening that malicious file earns you the installation of the Androm backdoor, which allows the cyber-attackers behind it remote access to your computer.
Scammers blame the government for failure to deliver the shipment. Source: media.kasperskydaily.com
Better Safe Than Sorry.
From the start of 2020, researchers report a 30,000% increase in phishing attacks exploiting the Coronavirus pandemic. New domains, taking advantage of COVID-19, pop up daily. Cybercriminals are not slowing down, but pumping up their malicious agendas. Their ultimate goal remains the same – to infect your system with malware, steal credentials and, generally, make money off of you.

Chart depicting the increase of COVID-19-themed threats in a mere three months. Source: zscaler.com
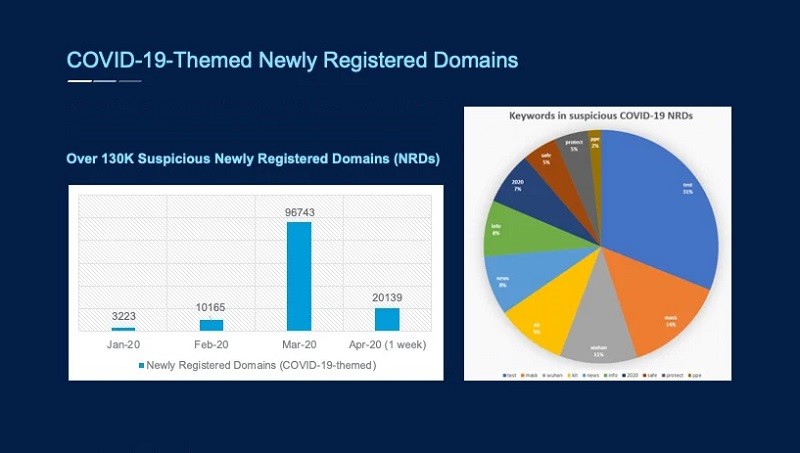
Newly-registered domains, starting January 2020 to the first week of April. Source: zscaler.com
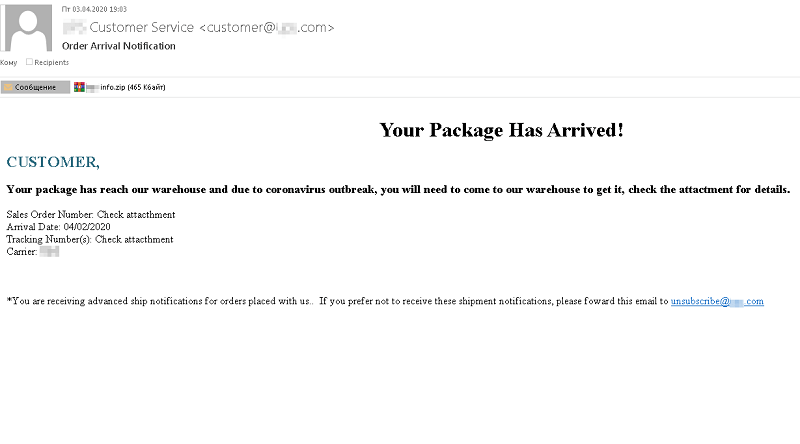
If you find yourself a recipient of such an email – one, claiming to come from a delivery company, be wary. It's best not to open them, but if you do, do NOT follow instructions in blind faith. Read through the contents, and look for anything that seems off – grammar, punctuation. Look for any mistakes as that's a dead giveaway for crooks. It may surprise you how mistake-ridden most of these phishing emails tend to be. Below you can see an example of one such email that claims to come from a delivery company, but the address begs to differ.

A phishing email that gives itself away with its address. Source: media.kasperskydaily.com
If you receive an email that doesn't seem to raise your suspicions but has you worrying about your package, do NOT click on anything on it, and do NOT open any documents it contains. Choose to, instead, go to your respective courier's website and track your package from there. If there are any issues with it, you will know from a reliable source. Sadly, emails rarely manage to classify as 'reliable' as they're often tools in cybercriminals' ploys for monetary gain. Bear that in mind, and remain vigilant when faced with an email that urges you to click or download anything. It's always better to be safe than sorry.







