How to Handle Login/Password Security Questions

Security questions, also known as secret questions, are arguably among the worst backup authentication and account recovery mechanisms you can possibly see at the moment. In the past they did work, but right now, they are neither secure nor, in an alarmingly large number of real-world scenarios, secret.
Here are a few what-were-they-thinking examples that should give you an idea of how serious the problem could be.
Offender #1:
This is one of the worst security questions I've seen. pic.twitter.com/iBm3kdaFDc
— Marie Huynh (@mariehuynh) October 9, 2014
This one is from 2014, and we couldn't verify if the system still operates in the same manner. As you can see, the user is forced to choose a "Security question" from a drop-down menu, and the first option is… *drumroll*… "What is the [sic] capitol of California?" Yes, the users are given the option of protecting their accounts with a question, the answer to which is located just a Google search away.
Now, you, like many people in the Twitter thread, can argue that users are not forced to answer the question correctly, but that's not the point. Users don't tend to think about security until the worst happens, and many would be tempted to show that they've been paying attention in school by entering Sacramento in the Answer field. And even if they don't, a hacker, armed with a list of cities, is still likely to guess the answer in a few tries.
Offender #2:
It's US' United Airlines. In 2016, they updated the login mechanism for their Frequent Flyer program. They said that the changes are a part of an effort to improve security. The 4-digit PINs their customers used were replaced by passwords which does seem like a step in the right direction (though some weak passwords could be even less secure than PINs). Then, however, they said that every time users log in from a new device or a new browser, they'll need to answer 5 "security questions." And they made users choose both the questions and the answers from drop-down menus.
There's a limited number of questions (which is an inherent problem in most systems of this type), and there's a limited number of answers (just 12 in the case of "During what month did you meet your spouse or significant other?"). The people who argue that answering not 1, not 2, but 5 different security questions might stop the hackers in their tracks shouldn't forget that cybercriminals have been faced with more serious challenges in the past, and they have come out on top. When United Airlines said that this design is there to protect users from keylogging malware, they showed just how poor their understanding of security is.
Offender #3:
This one deserves no comment. Described by security specialist Bruce Schneier as "a new low in secret questions," what appears to be a third-party authentication toolkit used by the website of US' National Archives gave users the option of choosing "What is your preferred internet password?" as their secret question.
Horrible Preferred Internet Password Challenge Question example image
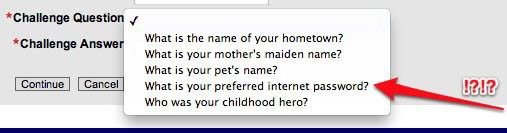
The three examples above show what happens when developers and vendors are in a hurry to launch and market a product without thinking about the potential consequences of its (in)security. Even when the implementation isn't as horrendous, however, security questions as an authentication mechanism still don't work.
In an ideal world, every single authentication mechanism would be a 50/50 blend of security and usability. Of course, we don't live in an ideal world, and all the mediums we use to prove our identity on the Internet today have their potential pitfalls. The thing about security questions is that they manage to be both insecure and hard to use.
The security aspect should be pretty obvious for anyone with interest in the subject. Unless you're still using mailing pigeons for communication and watch the news on an old-fashioned black-and-white TV, you can't get away from the fact that there's a ton of information about you and your loved ones on the Internet. Worse still, there's little you can do to control it.
This means that, in this day and age, protecting your accounts with questions like "What's your mother's maiden name?" isn't a terribly good idea. Pretty much the same thing holds true for "What is the make and model of your first car?", "What's the name of the town you grew up in?", etc. If it's not available on social networking websites, this information might be in possession of ex-significant others, relatives you've fallen out with, and other people you've trusted in the past. Even if they aren't included in your threat model, hackers might still be able to guess them, especially when the number of possible answers to a security question is limited (e.g., "Who is your favorite superhero?"). Incidents involving guessed answers to security questions have happened in the past, and if users and vendors don't do something about it, we might see them in the future.
All these things were detailed in a research paper published by Google back in 2015. The researchers aimed to prove that security questions are far from the perfect way of authenticating users and resetting their passwords. They did that quite conclusively.
In addition to the security aspect of secret questions, Google also examined how easy or difficult it is to set them up and use them. It turned out that memorability is a serious problem. For example, they observed that after just one month, about 26% of the people had forgotten the answer to their "Favorite food?" secret question. By the third month, nearly half of the users couldn't remember what their favorite food was, and after a year, only 47% were able to answer correctly. This problem amplifies when people answer untruthfully in an attempt to make their security questions more secure. When the nature of the question makes the answer more difficult to guess (e.g., "What was your first telephone number?"), memorability is an even bigger issue.
Google's conclusion was that if hackers can't guess the answers to the secret questions, users can't remember them. That's why, most websites and service providers have been slowly but surely removing secret questions from their registration forms. Yet, some still have them which is why users need to know how to handle them.
Experts seem to agree that the only way to deal with answers to secret questions is to make them as strong and as unique as your passwords. No hacker would ever be able to guess that your mother's maiden name is "5q*#!#0|@!-*E2" or that your favorite sports team is "=u-@:nL^!!:?9@". Of course, remembering long strings of letters, numbers and special characters is difficult, but Cyclonis Password Manager and its Private Notes feature can help. In fact, it can make the whole process quite a bit easier.
With the Password Generator you can create a random string of characters instead of trying to think of your second favorite Italian dish. Use it to answer your secret question and save it, along with the question, as a Private Note. Your Private Notes will be encrypted and stored in your personal vault. The only way to access them is with your master password.
Cyclonis Password Manager can remember your passwords for you, which means that you are unlikely to use the secret questions you save to regain access to your accounts. Some companies still use them as a means of authentication over the phone, however, which means that storing them in a secure place could save you quite a lot of hassle.
Although they are far from perfect, the security or secret questions still exist, and in some cases, they are still a part of the mechanism that is supposed to protect your sensitive data. Managing them is just as important as managing your passwords.








