LIKEAHORSE Ransomware Lurks in Pirated Media and Software

LIKEAHORSE Ransomware is not a piece of malware you want to have to deal with. Instead of trying to steal your passwords or spy on you, it focuses on damaging your data. It does this by encrypting the contents of important files, and then offering to provide you with a paid decryption tool. The criminals behind the LIKEAHORSE Ransomware may ask for hundreds of dollars, and they will probably ask victims to use a cryptocurrency like Bitcoin to complete the payment. You should certainly not accept these conditions, because it is very likely that the criminals might take your money without giving you anything in return.
LIKEAHORSE Ransomware Creators Ask for Bitcoin
The LIKEAHORSE Ransomware is likely to reach the majority of its victims through the use of email spam, fake downloads, and pirated content. To stay safe from such attacks, you should stick to browsing reputable and secure sites. Also, make sure to keep your system protected by an up-to-date anti-malware software suite.
The LIKEAHORSE Ransomware attack is characterized by several changes to the infected system. In addition to encrypting the contents of files, this malware will also:
- Mark the names of files with the '.LIKEAHORSE' extension.
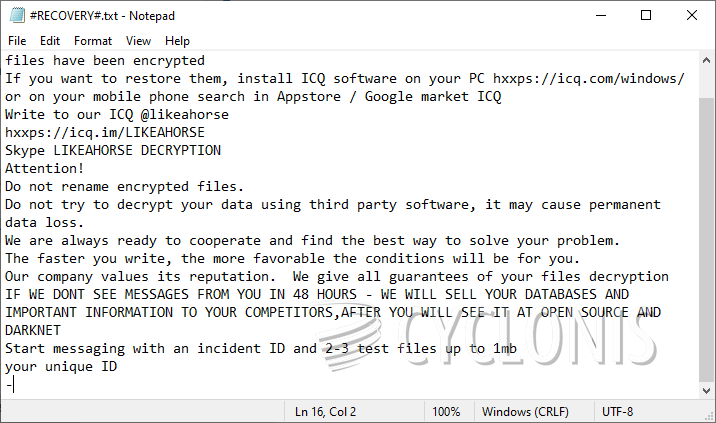
- Drop the ransom note '#RECOVER#.txt' on the desktop.
- Delete Shadow Volume Copies, and disable the System Restore service.
The criminals behind the LIKEAHORSE Ransomware provide two contact details in their ransom note. The ICQ profile @likeahorse, and the Skype ID 'LIKEAHORSE DECRYPTION.' We advise victims to avoid reaching out to the criminals. Instead, use antivirus tools to dispose of the file-locker, and then explore alternative data recovery strategies and software.