Remove BLUE LOCKER Ransomware

The BLUE LOCKER Ransomware is yet another file-locker whose creators are actively spreading it online. This particular sample does not appear to have links to currently active ransomware families. This is likely to mean that it is a brand new project and, so far, there is no information about its potential. However, the BLUE LOCKER Ransomware attack is certainly damaging. This threat is able to lock all sorts of file formats, and then extort the victim for money.
How is the BLUE LOCKER Ransomware Spread?
Malware operators often rely on multiple tricks to propagate their implants. They often disguise them as game cracks, software activators, or other pirated content that is in high demand. However, they also rely on other tactics such as sending fake emails with a malicious attachment. This is why Internet users should remember never to blindly download and open email attachments. You must verify that their sender is legitimate, and also scan the attachment with a reputable antivirus engine.
Naturally, safe Web browsing is not enough to keep you safe from all potentially harmful files. You should also protect your system with the use of an up-to-date anti-malware tool at all times. Another neat way to counter potential ransomware attacks is to maintain backup copies of your data. This way, you should be able to recover it easily in case of a file-locker attack.
Identifying the BLUE LOCKER Ransomware Attack
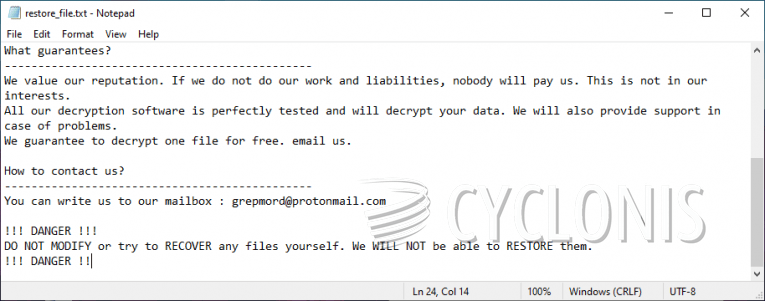
Files that this ransomware takes hostage are tagged with the extension '.blue.' Victims will also discover the document 'restore_file.txt' on their desktop. It contains a message from the authors of the BLUE LOCKER. According to them, victims should contact grepmord@protonmail.com to find out how to purchase the decryption tool. The latter's price is not included, but it is safe to assume that it will be at least a few hundred dollars.
Do not fall for the promises of the criminals. Paying them will most likely get you scammed. Instead, remove the BLUE LOCKER Ransomware with an anti-malware tool, and seek alternative recovery options.