Beware of Malware That Is Spread via LinkedIn DMs

There seems to be not a single platform that hackers and cyber attackers are not ready to exploit. They can expose you to malware via your own email inbox. They can create fictitious websites to expose you to scams. They can even modify legitimate websites to include malware payload. In every case, there’s something to gain for the attackers. In this report, we discuss how hackers use LinkedIn to spread malware. More specifically, we discuss how they use direct messaging (DM) to help spread malicious infections. Whether you use LinkedIn on a daily basis, or you rarely log into your account, you want to learn how to keep yourself safe against LinkedIn malware.
Hackers use LinkedIn to spread malware
According to recent statistics, LinkedIn has 590 million users, and so it is not that surprising that cyber attackers have decided to look for ways to exploit security backdoors within the platform. It has been around since 2003, and so it has had its fair share of security issues throughout the years. In 2017, for example, it was reported that legitimate accounts were hijacked to send phishing messages. Even Premium membership accounts were compromised during the attack, and that allowed hackers to spread malicious links to unsuspecting LinkedIn users. During this attack, even LinkedIn’s InMail service was exploited to distribute corrupted links, and if anyone clicked them, they were routed to phishing websites that were built to trick victims into disclosing Gmail, Yahoo, and AOL usernames and passwords. Checkpoint researchers further explained how existing vulnerabilities could have been used to spread LinkedIn malware via file transfers. Overall, LinkedIn malware is not a new thing, and, unfortunately, it does not look like the company can stop it in every case.
Earlier this year, Proofpoint researchers warned LinkedIn users about an attack linked to More_eggs backdoor. According to the report, this backdoor is not targeting LinkedIn users specifically, but it is using the platform’s messaging service to target anyone and everyone. Down to its core, LinkedIn is set up for recruiters and those looking for new employment opportunities. In an environment like that, it is not uncommon to receive direct messages from unknown companies or companies’ recruiters with different offers. That is what the attackers behind LinkedIn malware are well aware of, and, at first, they attempt to create some kind of connection to the targeted victim in a non-aggressive manner. Most frequently, they send a message asking to join the target’s network, and to make the request appear more legitimate, the hackers might include a message with some kind of an offer. Here is an image captured by Proofpoint that depicts how attackers behind LinkedIn malware rope in victims.
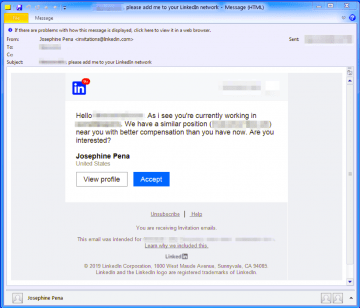
After some time has passed, if the target accepts the invite, they are sent a new message. This time, it might be sent to their personal email address, and it might contain a link to a website that, allegedly, has more information about a job offer. It all looks pretty legitimate, which is the strength behind this LinkedIn malware scam. If the target is tricked into following the link, they are routed to a fictitious website that might resemble a website of a genuine and trustworthy recruitment company. Once the website is loaded, a malicious file is downloaded automatically; however, the name of this file should trick the victim into thinking that they are opening a document file that contains information regarding a job offer. Without a doubt, this is a very clever scam because if the file is opened and macros is enabled, More_eggs malware is downloaded and executed silently, without the victim suspecting a thing. It was also found that attackers can easily adjust, and they can send malicious attachments or even harmless filler emails, which can be useful in those cases when the target is less gullible.
How to protect yourself against LinkedIn malware
It’s all pretty simple really. You just have to be vigilant. There is no doubt that hackers use LinkedIn to spread malware, and not much can be done to stop them. However, you can do a lot on your part. First and foremost, do not respond to every direct message or email you receive. If you are looking for a job, and you rely on LinkedIn to connect you to potential employers, you need to remember that you need to be smart. Always research the company that is contacting you, and never open links or documents sent via direct messaging or email before you are 100% sure that you are safe. Unfortunately, in some cases, it might be difficult to spot and unveil schemers. For example, if they manage to hijack accounts of people who have a good reputation on the platform, you are more likely to be scammed.
Speaking of LinkedIn account hijacking, who’s to say that your account will not be hijacked too? As we discussed earlier, phishing attacks could be employed to trick gullible users into disclosing sensitive login information, but if your login credentials are weak to begin with, attackers might take over your accounts even if you do not interact with them in any way. If you are not sure if your password is strong enough, you can check out this list. In general, any password that is short, memorable, and simple is the kind of password that cyber attackers can guess within seconds. They even have software and hardware that can do it for them! Do not make the mistake thinking that coming up with a good password is a challenge. For example, even something like ji32k7au4a83 is not considered to be a good password…
In conclusion, cyber criminals can drop malware onto your computer in various ways, and your LinkedIn direct messaging service could be exploited for successful LinkedIn malware attacks too. You want to be extremely careful about the messages and emails you receive and respond to because you never know when you could be communicating with an attacker. On the other hand, your own account could be used to spread malware too, and it is also your responsibility to ensure that hackers cannot take over and start spreading LinkedIn malware. Setting up a password that cyber criminals could not penetrate might be more complicated than you think. Luckily, there are tools that can save you the trouble and help you make your accounts secure. It would be a shame not to try them out.








