SARS-CoV-2 Malware Brings Terror with Data Encryption and Ransom Demands

It's an indisputable fact that the COVID-19 strain has created new opportunities for cyber attackers. Apart from running Coronavirus-related spam email campaigns, hackers have also used the strain to name their malware. That's why we see more and more threats with the words 'COVID', 'Corona', 'Coronavirus', etc. in their names. According to researchers, there's also a surge of web domains named after the virus. Most of them are suspected to be malicious.
Table of Contents
What Is Sars-Cov-2 Ransomware, and What Does This Threat Do?
SARS-CoV-2 is the name of a nasty threat from the ransomware family. Once it infiltrates the system, it will perform the following steps:
- The infection targets files and encrypts them.
- All encrypted files get the '.SARS-CoV-2' extension.
- The malware drops a ransom note named 'RECOVER MY ENCRYPTED FILES' on the desktop, demanding a bitcoin payment in exchange for a decryption tool.
This ransomware's targets are documents and files like .doc, .pdf, .docx, .xls, .txt, .png, .jpg, .jpeg, etc. After the files get encrypted, their extensions will be replaced with '.SARS-CoV-2', hence the name of the ransomware. The victim will then receive a ransom note, which contains instructions on how to recover the lost data.
The Ransom Note Left by the Sars-Cov-2 Malware
After the malware completes the data encryption process, it will drop a note (Fig.1) on the victim's desktop, which explains that the computer was hacked and every piece of data got encrypted. Here's the full text of the note:
“SARS-CoV-2
All your files was encrypted with a strong Ballistic Algorithm.
And your files encrypted have the extension : SARS-CoV-2
Don’t worry, you can return all your files!
must follow these steps carefully to decrypt your data
1. Pay $ 350 worth of bitcoin to this wallet : 33TfaP7jyjUgGkXL9ifjnqssy9TyAWfV3a
2. To get this software you need write on our e-mail : helpcov19@protonmail.comAfter all this, you get in your email the decryptor”
The ransom note urges the victim to send $350 to a bitcoin wallet if they want to regain access to their information. Once the payment is made, the user must get in contact with the attackers by writing to helpcov19@protonmail(dot)com. Supposedly, if all the steps are completed, the victim will receive a decryptor via email.
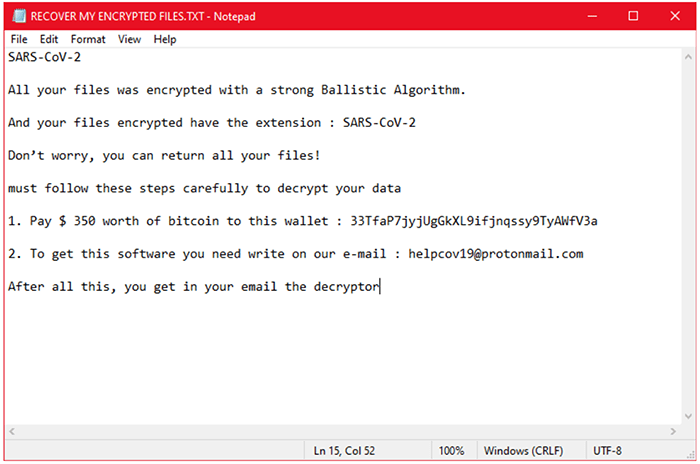
Figure 1: The image shows a screenshot of the note dropped by SARS-CoV-2 on the victim's desktop.
Sars-Cov-2 Ransomware Distribution Methods
The most common means for ransomware distribution are:
- Spam email campaigns
- Third-party installations
If you had the misfortune of getting your computer infected with this malware, chances are you've either interacted with shady emails or have installed free software from questionable sources.
Nowadays, everyone receives spam emails. Unfortunately, not all messages get filtered accordingly. Some emails can be very misleading, especially if they claim to be sent from established companies like Amazon, FedEx, DHL, or another organization. Messages with malicious content are also known to have attractive titles. Hackers will try to lure you with urgent emails that will prompt you to open attachments or follow links. It's very common for cyber criminals to lie about a compromised bank account in such emails. In most cases, the victim will not give a second thought about the legitimacy of the message, and will mindlessly interact with the provided link or attachment. That's why you should always get your software from trustworthy and official sources only. A little background check could go a long way and even potentially save your computer from getting infected.








