What's the Best Alternative to the Online Password Strength Meters?

People don't create online accounts for the fun of it. They do it because they want to use a particular service, and in many cases, they want to use it as quickly as possible. As a result, most users are in too much of a hurry to stop and think about the strength of their password when they're creating an account. Usually, they think about it after it gets cracked. What if there's something that could change this behavior?
You've all seen them. You enter a password during the account creation process, and the password strength meter tells you what it thinks of it. Some classify passwords as weak, mediocre, and strong. Others give you a score, and others still employ a red/amber/green indicator. The idea is that if you're trying to set a weak password, the strength meter will tell you about it and will also encourage you to think of a stronger one. It works. At least to a point.
People have been examining how effective password strength meters are, and they've concluded that overall, users are more likely to think of a more complex password when they're told that theirs is not up to par.
So, password strength meters are not just a gimmick. They do serve a purpose, and the fact that their presence leads to more complex passwords in some cases means that they should stay. The trouble is, most of them don't actually do what they say they do.
Table of Contents
Why you shouldn’t blindly trust password strength meters
Let's do a simple experiment. Go to Google, search for "password strength meter," and one of the first results you'll get is www.passwordmeter.com. NOTE: if you're going to test passwordmeter.com, make sure you don't use one of your own passwords. It's generally a bad idea to give out sensitive information to random websites on Google and to top it all off, this particular one is served over HTTP, and not HTTPS, which means that it's not terribly secure.
For our experiment, we're going to use "P@ssword!". We picked this one because many people might believe that, in addition to being easy to remember, it has reasonable strength with the "@" and the exclamation mark at the end. Indeed, this is what passwordmeter.com thinks as well. It gives "P@ssword!" a score of 68% and rates its complexity as "strong."
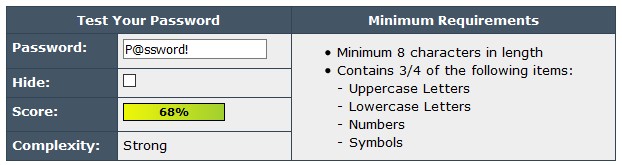
In fairness, there is a disclaimer on passwordmeter.com which says that the tool is "neither perfect nor foolproof," and this example hammers the point home pretty well. Most of you should know by now that "P@ssword!" is not a strong password and those of you who don't should open this link. It's a dictionary containing about 16 thousand common passwords, which anybody can download from GitHub. If you scroll down to line 2,692, you'll see "P@ssword!". So, a hacker using this particular dictionary will need to make less than 3 thousand guessed to get your password. That's not a lot with today's tools.
The problem with most password strength meters
The issue lies with the fact that most password strength meters rely on algorithms to estimate your password's resilience to brute-force attacks. Generally speaking, this depends on the number and variety of characters, but some password meters also look out for things like a succession of numbers (e.g., "123") and identical letters grouped together. Here's the thing – a brute-force attack is an old, ineffective way of guessing a password.
The hundreds of data breaches that occurred over the last decade or so exposed millions upon millions of passwords. As a result, dictionaries like the one we talked about earlier were compiled, which made the hackers' job quite a bit easier. Thanks to these dictionaries, the bad guys know the common words and the type of patterns (e.g., replacing "a" with an "@") people use for their passwords, and they can make informed guesses.
These informed guesses mean that while cracking "P@ssword!" with brute force could take a while, cracking it with a dictionary will take milliseconds.
zxcvbn – the exception to the rule
In 2012, experts from Dropbox developed and open-sourced zxcvbn – an improved algorithm for estimating the strength of a password. In addition to determining the ability of a password to withstand a brute-force attack, it also focuses on spotting some of the patterns we talked about as well as common words. Experts agree that it's the best algorithm for estimating password strength currently available, which is why, it's also implemented in Cyclonis Password Manager's Password Analyzer.
Of course, it's still an algorithm, and you can't assume that it's right 100% of the time. Nevertheless, zxcvbn takes more than one factor when determining how likely hackers are to crack your password which makes it stand out from the crowd.
Can password strength meters become obsolete?
People continue to create passwords on their own, and they continue to make mistakes which means that the need to encourage them to do better is definitely there. If they use password generators to create their passwords, the strength meters, regardless of which algorithm they're based on, will always say that the password is strong. That's because it will be.
An automatic password generator creates a random string of characters without employing patterns or words that would make the password easy to remember. If password generators become the norm rather than the exceptions, we might just wave strength meters goodbye. Until then, they are here to stay.








