Remove STOP/DJVU Ransomware [Decryption Explained]
Before you dive in
Exploring the internet requires robust protection. SpyHunter is designed to elevate your computer's security.
Take a step towards safer online experiences today. Download SpyHunter for Mac here! Shield your device from digital dangers and enjoy peace of mind with a secure browsing experience.

STOP/DJVU is a widespread ransomware family known for attacking individuals and organizations. It encrypts your files and asks for money to decrypt them.
This article will uncover the origins, operation, and impact of STOP/DJVU and offer insights into prevention and recovery strategies.
Learn how to protect your data and respond to this pervasive cyber threat. Read on:
Introduction to STOP/DJVU ransomware
Ransomware attacks are increasingly common and target users worldwide. Among these threats, the STOP/DJVU ransomware family has been notable since its appearance in 2018.
This family includes variants such as LKFR, LKHY, MOIA, MAAS, and FATP, which encrypt files on Windows and Mac computers and demand ransom for decryption keys.
STOP/DJVU typically enters systems through deceptive downloads, including software cracks and pirated content. It encrypts user files—such as documents, photos, and videos—applying extensions like .djvu, .lkfr, .lkhy, .moia, and .fatp. A ransom note is then left on the desktop, demanding payment.
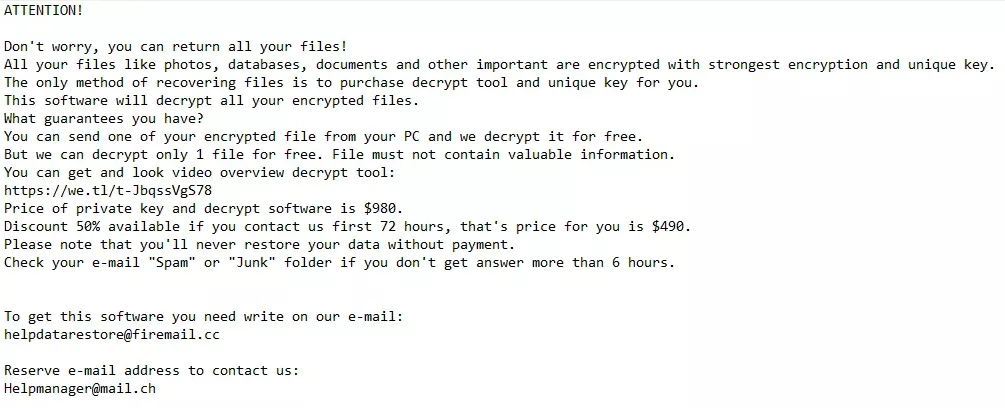
This ransomware uses public key cryptography, encrypting up to 5MB of files to keep the system usable for payment processing. With new variants constantly appearing, staying informed and practicing good cybersecurity is essential to protect against STOP/DJVU.
How STOP/DJVU works
How it spreads
STOP/DJVU mainly spreads through downloading cracked software or adware from unreliable websites. Once inside, it encrypts files and demands a ransom, putting users under pressure to pay to get their data back.
The evolution of STOP/DJVU
Since 2018, STOP/DJVU has constantly evolved, releasing new versions that alter how it encrypts files and demands a ransom. These changes make fighting harder, as it finds new ways to attack users, even targeting specific groups like Discord communities.
Recognizing STOP/DJVU infection
Identifying a STOP/DJVU ransomware infection promptly is critical to limit damage. Several signs indicate your device may be compromised:
- File Extension Changes: Your files have a new extension, such as .djvu or another variant-specific extension, appended to them.
- Ransom Note: A ransom note, usually as a
readme.txtfile, appears on your desktop or in the encrypted file folders. - Inability to Open Files: Attempts to open files lead to errors or the files open in a cluttered, unreadable format.
- System Performance Issues: A noticeable slowdown in computer performance, as the ransomware consumes system resources during the encryption process.
Isolating the infected device
When you suspect an infection, isolating the device is crucial:
- Disconnect from the Internet: Immediately remove the Ethernet cable or disable Wi-Fi to sever any connections to the Internet.
- Unplug External Devices: Disconnect all external storage devices to avoid further spreading.
- Sign out of Cloud Storage: Log out of any cloud storage accounts to prevent the ransomware from accessing and encrypting files stored in the cloud.
- Limit Network Connectivity: Disconnect the infected device from the local network to prevent the ransomware from spreading to other devices.
How to remove STOP/DJVU ransomware
Removing the STOP/DJVU ransomware from an infected computer is crucial to regain access to encrypted files and restore the device’s integrity. Three primary methods to tackle this malicious software are manual removal, anti-ransomware tools, and system restore options.
Method 1: Manually remove STOP/DJVU
Manual removal is best suited for users with technical expertise. Here’s how to approach it:
For Windows users
- Enter Safe Mode with Networking: Restart your PC. As it reboots, tap F8 (or the key assigned for your PC) to access
Advanced Boot Optionsand selectSafe Mode with Networking. - Find and Delete Malicious Files: Use Windows Explorer’s search function to find files associated with STOP/DJVU. Typical locations include:
%AppData%%Temp%%LocalAppData%
- Remove Registry Entries: Open the
Registry Editorby typingregeditin the Start menu search. Then, navigate to the entries made by the ransomware. Exercise extreme caution; incorrect edits can cause system damage.
For Mac users
- Start in Safe Mode: Restart your Mac and immediately press and hold the
Shiftkey. Hold it until the login window appears. Log in to proceed inSafe Mode. - Locate and Delete Files: Use
Finderto search for any suspicious files related to STOP/DJVU. Focus on directories like:/Library/LaunchAgents/~/Library/LaunchAgents//Library/LaunchDaemons//Library/StartupItems//Library/Application Support//Applications/~/Downloads/
Manual removal requires careful identification of ransomware components without affecting essential system files. If unsure, consider seeking professional help or using dedicated anti-malware tools to ensure thorough cleanup.
Method 2: Automatically remove STOP/DJVU with SpyHunter
SpyHunter provides an efficient and reliable solution for those seeking a safer, more straightforward approach. SpyHunter is designed to detect and remove malware threats with minimal user intervention.
For Windows: SpyHunter 5
- Download the app here and follow the installation guide to set up SpyHunter 5 on your Windows PC.
- Open SpyHunter 5 and initiate a scan to find ransomware and other harmful software on your device.
- Follow SpyHunter’s prompts to remove any detected threats, safeguarding your PC from further attacks.
For Mac: SpyHunter for Mac
- Download SpyHunter for free here and complete the setup process.
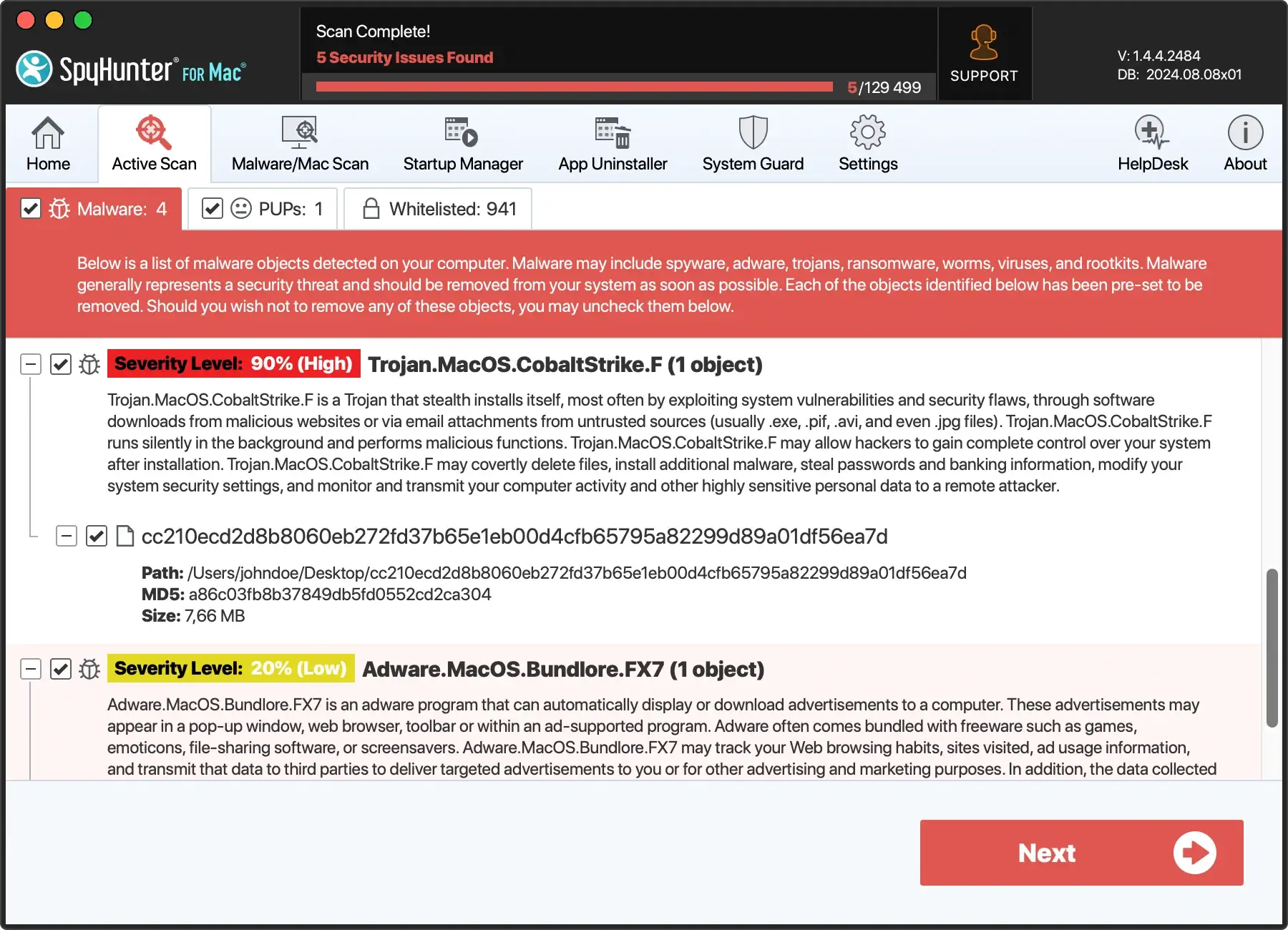
- Launch SpyHunter for Mac and run a full system scan to detect STOP/DJVU ransomware and associated malicious components.
- Use SpyHunter’s recommendations to eliminate any identified threats efficiently.
Method 3: System restore and recovery
When STOP/DJVU ransomware impacts your system, restoring it to a prior state can be an effective recovery strategy.
For Windows users
- Windows System Restore: This feature reverts your system to an earlier restore point before the ransomware attack.
- System Recovery or Clean Reinstall: In cases where the damage is extensive, a complete system recovery or a clean reinstall of Windows may be necessary.
For Mac users
- Time Machine Backup: If infected, you can restore your system to a pre-infection state from a Time Machine backup.
- macOS Recovery: If a Time Machine backup isn’t available, consider using macOS Recovery to reinstall macOS.
Techniques to decrypt STOP/DJVU files
Regaining access to encrypted data after a STOP/DJVU ransomware attack can be challenging. Understanding the decryption process is vital for adequate recovery.
The difference between online and offline keys
STOP/DJVU ransomware uses two main types of encryption keys: online and offline.
- Online Keys: When the ransomware communicates with its remote server during the infection, it uses a unique encryption key for each victim.
- Offline Keys: In scenarios where the ransomware cannot connect to its remote server, it uses a pre-defined offline key. This key is the same for all victims affected during a specific ransomware version.
Identifying whether your files were encrypted with an online or offline key is crucial for determining the approach for decryption.
Free decryptor tools for STOP/DJVU
Free decryptors created by cybersecurity experts can help victims whose files were encrypted with offline keys. Decryption is harder for those affected by online key variants since each victim has a unique key.
How to prevent STOP/DJVU ransomware attacks
Taking steps to protect your digital life can significantly reduce your risk of an attack.
Backup your data
- Use Local and Cloud Storage: Use both physical devices and online storage.
- Follow the 3-2-1 Rule: Have three copies of your data on two different media, one backup offsite.
- Encrypt and Check Backups: Make sure your backups are encrypted and check them regularly.
Keep software updated
- Patch Regularly: Stay on top of your software and operating system updates.
- Turn on Automatic Updates: This ensures you’re always running the latest software version.
Use security tools
Get trusted antivirus and anti-malware software to fortify your digital walls. A good security software like SpyHunter is your first line of defense, detecting and blocking ransomware before it can harm you.
Download SpyHunter and enhance your security today.
Stay informed
Understanding what STOP/DJVU ransomware is and how it spreads can help you avoid common traps, like clicking on suspicious links or downloading unsafe software.
Conclusion
Recovering from a STOP/DJVU attack means removing the malware, trying data recovery, and securing your system.
Although challenging, knowing your recovery options and when to seek professional help can increase your chances of success.
Not all encrypted files will be recoverable, so back up your data regularly.