Advanced Persistent Threat (APT)
What is an Advanced Persistent Threat (APT)?
Advanced persistent threats (APTs) are among the most severe cyber threats facing organizations today. They are highly sophisticated and often difficult to detect, allowing attackers to remain hidden in a system for an extended period with potentially devastating consequences.
APTs differ from other forms of malicious activity because they can use multiple complex techniques to gain entry and remain undetected. APTs typically include a range of hacking techniques, such as phishing, malware injection, zero-day exploits, social engineering attacks, and more. These attacks can be used to steal valuable data or disrupt operations by creating chaos within an organization’s IT infrastructure.
What Are Some Common Targets of APT Attacks?
APTs are typically tailored towards organizations or individuals with high-value information, making them susceptible to higher levels of risk. Common targets of APT attacks include corporations, government bodies, financial institutions, critical infrastructure providers, military systems, and any other business or organization that holds sensitive data. The goal of an APT is to gain persistent access to the target’s system, often for extended periods, to gather intelligence or disrupt operations.
APTs can also be used as a form of economic espionage, where attackers attempt to steal trade secrets, confidential corporate data, and other information that can give them a competitive advantage. These attacks are particularly dangerous for both commercial and government organizations because even if the attackers do not gain access to sensitive data, they may still be able to disrupt operations or cause damage to systems or networks.
Organizations need to take proactive steps in order to protect themselves from APT attacks. This includes implementing strong security measures such as firewalls, antivirus software, patching systems regularly, and training employees in cybersecurity best practices. Additionally, organizations must be prepared to respond quickly and effectively to any potential attack to minimize damage and disruption.
The Anatomy of an APT Attack
As mentioned, APTs are typically conducted using advanced tools and techniques, such as custom malware, zero-day exploits, and sophisticated phishing campaigns. Attackers may also use social engineering tactics to gain access to a system or manipulate victims into giving away confidential information.
APTs are often conducted using various tools and techniques, such as malware, exploits, and phishing campaigns. These attacks aim to gain access to a system or otherwise manipulate victims into providing confidential information. APTs can spread through various means, such as file-sharing networks, malicious emails, instant messaging platforms, social media accounts, and more.
Once inside a network or system, attackers can use their access to install malicious programs or spyware, which allow them to collect data or modify system configurations without being detected. Additionally, attackers often use encryption to ensure that their activities cannot be traced back to them.
The best defense against APTs is a combination of technical controls, user awareness, and proper incident response plans. Technical controls can include antivirus software, web filters, firewalls, malware detection & removal tools, intrusion detection systems (IDS), and secure configurations for all devices on the network. User awareness should involve regular security training, providing users with information on potential threats, and using strong authentication methods. Finally, having an incident response plan in place will help quickly detect and respond to any attacks that occur.
The Startling Statistics Behind APT Attacks
Statistics indicate that APTs are becoming increasingly more common, with their prevalence growing exponentially since 2017. APT attacks have become so commonplace in the modern digital domain that they account for roughly 43% of all cyber-attacks. The consequences of this trend are staggering, as the number of stolen records due to APT attacks in 2020 alone reached more than 1 billion.
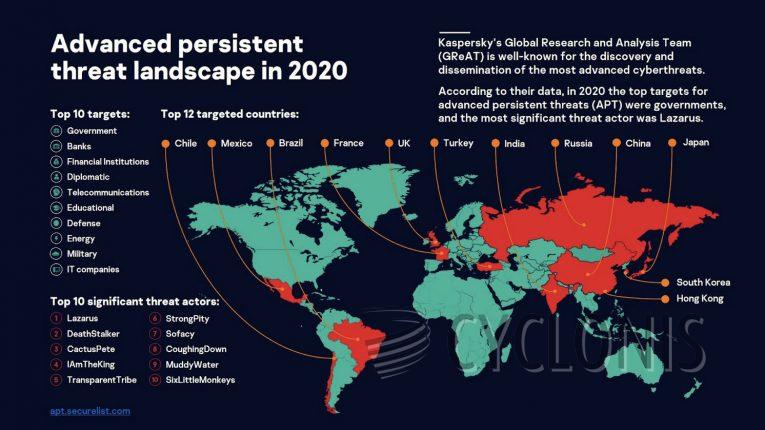
Source: Securelist
Furthermore, the number of organizations targeted by APT attacks has increased significantly in recent years. Over one-third of all companies surveyed in 2020 experienced a successful APT attack at some point during the year. Additionally, APTs have been identified as the most common type of attack used to target sensitive and confidential data, accounting for around 81% of such attacks.
The prevalence of APT attacks is expected to continue rising in the coming years as more sophisticated techniques are developed and deployed; this will undoubtedly lead to further significant losses in terms of stolen data and financial resources. Organizations need to be aware of the potential risks posed by APT attacks and take steps to protect themselves.
Examples of the Destructive APT Potential
One of the most high-profile examples of an APT attack was the hacking of the US Democratic National Committee (DNC) in 2016. This attack, which is believed to have been conducted by Russian government-linked hackers, resulted in the release of thousands of confidential documents related to the DNC.
Another high-profile example was the WannaCry attack in 2017. This attack targeted computers running Windows XP and was spread through a series of phishing emails. It is believed that this ransomware attack cost victims around $4 billion in damages, making it one of the most destructive cyber-attacks to date.
Another example of an APT attack is Stuxnet, which was first identified in 2010. This attack disrupted the operations of Iran’s nuclear program by specifically targeting industrial control systems (ICS). It did so by exploiting zero-day vulnerabilities in Windows systems and using modular malware code that allowed it to spread across networks.
APTs can also employ wipers, as was shown by Shamoon, also known as Disttrack, a malware strain that first appeared in 2012. It has been used to launch destructive attacks against various organizations and companies, most notably Saudi Arabian oil giant Aramco in August 2012. The attack resulted in the deletion of 30,000 computers, causing an estimated $10 billion worth of damage and disruption. It is believed that the attack was politically motivated, with most security experts pointing to a nation-state actor as the culprit.
In addition to these more well-known examples, there have been many other APT attacks in recent years. These include the Target data breach in 2013, which resulted in the theft of tens of millions of credit card numbers and other personal information, as well as a 2014 attack on Sony Pictures that made private emails and other sensitive documents public.
We have looked at the various types of Advanced Persistent Threats (APTs) and their destructive potential. We have also seen that no organization is immune to them and that they can successfully attack organizations of all sizes and industries. To protect your business from an APT attack, it is essential to be aware of the signs that one may be occurring and to have a plan in place for responding to one if it does happen. Finally, it is important to remember that the consequences of an APT attack can be severe, so organizations must take steps to protect themselves and respond quickly in the event of an attack. This includes implementing robust authentication methods, regularly updating software, educating staff on cybersecurity best practices, and investing in advanced security solutions.