Thanks to StrandHogg, Malware Can Create Fake Login Screens to Steal Your Passwords

On Monday, researchers from a Norwegian mobile security company called Promon publicly disclosed a serious vulnerability in the Android operating system. It's rather aptly named after StrandHogg – the Viking tactic of raiding coastal lines and capturing indigenous people with the intention of trading them as slaves. The vulnerability affects all versions of Google's mobile operating system, including the latest Android 10, and according to Promon, with it, hackers can attack users of the 500 most popular applications on the Google Play store. If exploited, StrandHogg gives attackers the ability to do just about anything from reviewing call logs through phishing login credentials to spying on people with the device's camera and microphone. Before we see how StrandHogg works, however, we first need to learn how a typical attack on Android unfolds.
Table of Contents
How hackers usually attack Android users
It's a well-known fact that an Android device presents a pretty significant attack surface. Our smartphones are more or less glued to our hands, and we do pretty much everything on them nowadays. Hackers can indeed use them to steal sensitive information and spy on us, but doing it isn't as simple as tricking us into installing a malicious application.
Apps usually don't have access to every nook and cranny of the operating system. Before they can use the device's microphone, for example, they need to ask for explicit permission, and if they are to have more freedom of movement, they need administrative rights. In a typical scenario, the user is the one deciding which apps get which permissions, and attacks often fail because of this. Getting the required permissions without the owner's specific consent is possible if the device is rooted, but it must be said that not that many people know how or can be bothered to root their smartphones.
The trouble with StrandHogg is that it can work on devices that are not rooted, and in certain exploitation scenarios, it can gain all the permissions it needs without the user suspecting a thing.
How StrandHogg works
StrandHogg's strength lies in the fact that it lets hackers impersonate legitimate applications. The successful exploitation of StrandHogg requires the installation of a malicious application either by the user or by a dropper app. According to Promon, the malware can come with some sort of legitimate functionality. Its main purpose, however, is to use a weakness in Android's multitasking system, which lets it perform a clever trick that can fool even the more observant user.
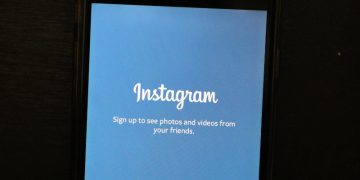
Because of that weakness, the malware can display a phishing login form the next time the user launches an application like Facebook, for example. After it sends the collected login credentials to the hackers, the fake app runs Facebook, which reduces the chances of the victim figuring out that something's not quite right.
Using StrandHogg, a malicious application can also impersonate a legitimate one and ask for permissions, which could be difficult to get in a more usual attack. For example, if a third-party weather app or a calculator is requesting access to the device's camera, you're unlikely to click the OK button straight away. If, on the other hand, Facebook is asking for the same permission, you'd think that this is perfectly normal because that's how you create posts and stories on the go. Because of StrandHogg, however, the app you're interacting with might not be Facebook at all.
Using StrandHogg, a malicious application can get pretty much any permission it needs, which is why the vulnerability can be used in such a wide range of attack scenarios. As if that wasn't enough, a successful exploit is very difficult to detect. Promon's experts did note that you might be able to spot the malicious app in the Recent Apps screen, but they said that the attackers have a way of hiding it from you. The really bad news is, cybercriminals already know how to take advantage of the vulnerability, and they are doing it as we speak.
StrandHogg is already exploited in the wild
Promon's researchers said that they've seen "tangible evidence" of hackers using the StrandHogg vulnerability. In fact, the entire investigation began after several banks in the Czech Republic sounded alarms about customers getting their accounts drained. Lookout, one of Promon's partners, identified a total of 36 malicious applications that have been seen exploiting StrandHogg in the wild. One of them was a BankBot variant dating back to 2017, and although none of the apps resided on Google Play, some of them were downloaded via droppers that were available on the Android's official store. Google removed the apps immediately after it was notified, but it then failed to say what it's doing to fix what is undoubtedly a serious problem.
Although Promon's researchers shared their findings with Google back in the summer, StrandHogg affects even the newest flagship devices running Android's latest version. This means that either fixing the vulnerability is proving too difficult or Google isn't in too much of a hurry to do it. Because the search engine giant hasn't issued an official comment, we can't be sure where the problem is. Promon's report tells us, however, that when aspects of the vulnerability were described by Penn State University researchers in 2015, Google dismissed StrandHogg's severity. Hopefully, with or without an official announcement, a patch is coming soon.