Mozart Malware Proves Elusive To Detection Thanks to Its Use of DNS Protocol

Mozart is the name of a backdoor Trojan. It created shock-waves in the webspace in February 2020. Even in its short lifespan since then, it has managed to rile people up. So far, it has claimed a mere few hundred people worldwide, but experts expect that number to grow as the infection is making a name for itself. Cyber researchers believe that the malware is still in its development stage, so they project that its impact regarding damage will expand.
However, web users should note that Mozart did not make its debut in February 2020, but instead made a comeback. Initially, the infection made waves in September 2014, when it hacked the Home Depot Inc., United States. That breach earned the hackers, behind the nasty cyber threat, the credit and debit card details of over 56 Million Accounts.
What follows after hackers steal your data? A stolen credit card price tag of $102.
There was an official investigation over the attack, led by the Secret Service in the USA. They concluded that the Mozart malware got customized for that specific attack – against Home Depot's systems.
Table of Contents
What to expect from Mozart malware?
The malicious software allows the cybercriminals behind it to execute an array of commands on the infected machine, once they slither their way inside it. Corruption is made possible with the use of the DNS protocol. That particular communication method between software and hackers makes it easier for them to avoid detection, and remain hidden from security software.
The Mozart malware turns to a plethora of obfuscation techniques to evade detection by anti-virus programs. And, even if you do manage to detect the threat, it makes sure to turn the process of removing it from your machine quite a difficult one. The Trojan may gain root access to your PC, and make its removal into a near-impossible feat.
The malicious malware bears all the traits we've come to associate with backdoor Trojans, as well as some new ones. It doesn't differ from other such threats with its operations of data corruption and data harvesting, malware proliferation, and additional privilege escalation. However, a feature that's unique to Mozart malware is its communication protocol. What makes it stand out from other infections of its kind, is the fact that it uses DNS protocol to communicate with remote servers. It chooses a DNS instead of a regular HTTP/HTTPS. And, in doing so, the malware evades anti-virus detection. Thus, prolonging its stay and ensuring maximum damage.
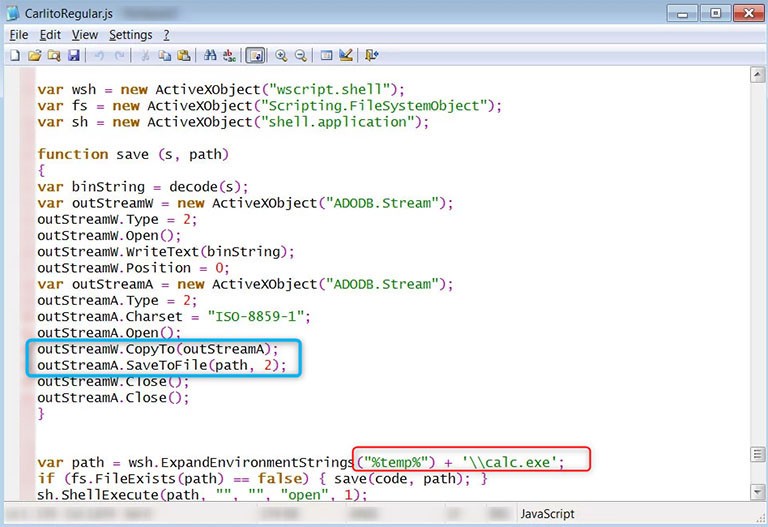
Mozart's use of DNS protocol. Source: virusremovalguidelines.com
A perk from using the DNS protocol is evasion from all the security applications that search for malicious activity by monitoring the HTTP traffic. Another advantage that comes from the DNS protocol, which may result in data deletion or malicious code execution, is the fact that commands given by the attackers can get transferred via the DNS TXT records.
DNS TXT records get used to issue commands. If you' 're unsure about what that means exactly, here's the gist of it. First off, you have to realize that DNS is a name resolution protocol that gets used to convert a hostname. The hostname gets turned into its IP address. Here's an example: www.example.com becomes 92.184.134.25. That allows the software to connect to the remote computer. It's a rather useful feature when one must verify their ownership over certain online services and email security policies. The DNS protocol doesn't only convert hostnames. It also lets you query TXT records that contain text data. The hackers behind Mozart use these DNS TXT records to store commands, which the malware retrieves and executes on the corrupted machine.
How does Mozart affect your system? Symptoms and disadvantages followed by its stay
You suffer a plethora of consequences because of Mozart's stay on your machine, but they may not get your attention as fast as, say, adware or ransomware would. By nature, backdoor Trojans are stealthy and sneaky. They keep a low profile and wreak havoc out of sight. It's in their best interest to keep off your radar for as long as possible. By the time you notice the infection's stay, there is quite a lot of damage already done. That being said, of course, you do face a set of symptoms, you can detect early on, courtesy of the Mozart threat. You discover a slowdown of your Internet speed every time you go online, and an increase in network activity. There's high resource usage, and a lot of application crashes. Lag becomes a daily nuisance.
It is not overtly apparent what the infection's primary objectives are, although they must undoubtedly be financially motivated. Backdoor Trojans, like the Mozart malware, thrive on harvesting sensitive personal and financial information for the cybercriminals behind them, who can then pawn it off the dark web or use for other elicit malicious purposes. The same as Mozart did after the Home Depot breach and subsequent data theft. The malware can steal your information, conduct illegal money transfers, and that's only a few of its options.
Spreading the infection – Mozart’s preferred infiltration methods
Typical invasion tactics involve botnets sending out spam emails, in either targeted or random attacks. They can reach hundreds or even thousands of potential victims worldwide.
Mozart travels from system to system, infecting machines, with the help of malicious PDF attachments. You receive an email that's malicious but appears non-threatening on the surface level. You should always be cautious, and carefully examine emails you get even before you open them. Check the sender and see if you recognize them. Is it a known name or company with letters missing, or a logo that seems off? Investigate before you take any action, like clicking a link or downloading an attachment contained in the email. That's among the most common methods for cybercriminals to trick you and make their way into your PC. They prey on your negligence and naivety. Do your best not to give in to distraction, and be thorough. Avoid opening spam emails at all, and if you do open one, be wary with your clicks. Vigilance can prevent you from quite the trouble.
Naturally, that's not the only invasive way in Mozart's arsenal. The infection can turn to a range of alternative infiltration methods. Apart from wide-spread malvertising campaigns, the malware can also resort to a myriad of other invasive tools at its disposal. Peer-to-peer networks, corrupted links, sites and torrents, freeware downloads, third party downloaders, and that's to name a few. When it comes to infiltration, Mozart has quite a lot of methods it can resort to using. Files get used as a carrier, appearing harmless while disguising the presence of a threat. Fake software updaters do NOT install updates, but infections. System bugs and flaws also get exploited, so make sure to keep your machine well-updated, by turning to reputable updaters, of course.
If you do fall for the infection's deceptive tactics and download the PDF attachment, here's what follows. The PDF includes a malicious link to a .zip file. You receive instructions to execute, and if you do, that execution triggers a JavaScript command. Then, a file called calc.exe gets downloaded and placed in the Temporary subfolder.
As soon as all these steps get done, the system infection process gets triggered. A text file called mozart.txt gets created in the same Temp file folder, and inserts "12345" content inside.
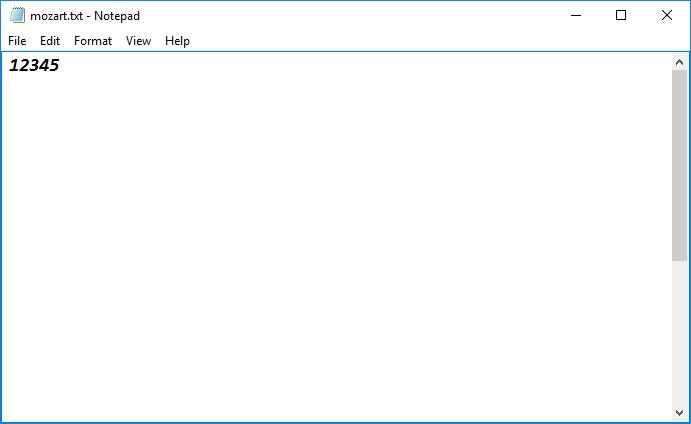
Image of the text file with the content already inside it. Source: virusremovalguidelines.com
What follows is the malicious infection imports an array of files into the Startup folder. Thus, ensuring that every time the Windows system boots, it loads.
Not only does Mozart malware make sure that it loads with every start and restart of your system, but it also arranges to receive updates. The malicious Trojan has programming to receive seven DNS request tasks (listed below). It's these tasks that allow the infection to update itself and check which updates got applied, to allocate memory, as well as a multitude of other commands.
- .getid
- .gettasks
- .gettasksize
- .gettask
- .reporttask
- .reportupdates
- .getupdates
List of the DNS request tasks received by Mozart malware
The cyber threat meddles with your system, implementing a myriad of changes, necessary for its prosperity and the benefit of the hackers behind it.
A backdoor gets established, which allows the cybercriminals to slowly but surely seize control of your machine. And, that's hardly desirable. If hackers find their way into your system, you suffer a range of repercussions, which range in severity – data loss, as well as personal and financial information loss. The hackers can steal your identity, which can cost you a lot of money, time, and energy, trying to sort out the mess they forced upon you. Not to mention, Mozart malware can open your PC to more outside threats.
Mozart has earned the classification 'malware loader.' That means it's able to download and install a variety of malicious software on your computer. With Mozart on board, you risk your machine getting flooded with adware, hijackers, more Trojans, even ransomware.
If you wish to avoid dealing with the cyber-hazard that is Mozart malware, caution is crucial. Vigilance, when browsing the web, proves essential if you want to prevent unwittingly allowing infections on your machine. Be careful what sites you visit and what you click and download. Pop-up coupons and ads that urge you to click the link for a 'bargain' are a no-no. Avoid giving in to the urge to trust them at all costs. Keep your machine updated, and find yourself a proper anti-virus tool. Install and enable security solutions, which can monitor DNS TXT requests.








