Hackers Break Their Promise: Coronavirus Vaccine Test Lab Attacked by Maze Ransomware

Operators of the Maze malware announced earlier this month that they would stop targeting healthcare organizations. Not forever, of course. Only until the pandemic situation gets under control. Unfortunately, it seems that their promise is very short-lived, as malicious attackers have used Maze ransomware to hit a British medical lab that's slated to run COVID-19 vaccine tests.
Maze malware actors pledge to stop attacks on hospitals
The Maze team posted an official press release on March 18, 2020, making a promise to stop all activity against medical organizations for the duration of the crisis. They didn't comment on the issue of accidental attacks, so there's no official confirmation from their side that they'll provide free decryption for medical systems affected by mistake. Here's what the press release said:
“Due to situation with incoming global economy crisis and virus pandemiс, our Team decided to help commercial organisations as much as possible. We are starting exclusive discounts season for everyone who have faced our product. Discounts are offered for both decrypting files and deleting of the leaked data. To get the discounts our partners should contact us using the chat or our news resource.
In case of agreement all the info will be deleted and decryptors will be provided.
The offer applies to both new partners and the “archived” ones. We are always open for cooperation and communication.
We also stop all activity versus all kinds of medical organizations until the stabilization of the situation with virus.”
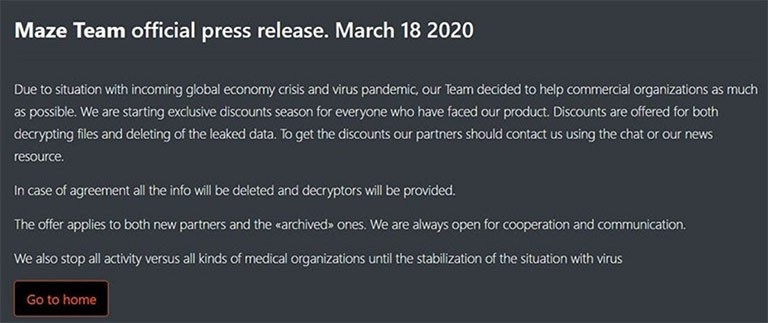
Figure 1: Image shows a screenshot of Maze Team's official press release on their website, posted on March 18, 2020
Maze ransomware attackers fail to keep their word, proving they cannot be trusted
Only days after they publicly made that promise, cyber crooks using Maze ransomware hit a company called Hammersmith Medicines Research (HMR), leaking the personal information of thousands of former patients. The company in question is known to have carried out tests to develop the Ebola vaccine, as well as drugs that can treat Alzheimer's disease, and was reportedly on standby to carry out trials for a possible Coronavirus vaccine before they were attacked with Maze malware. HMR state that their IT team discovered the attack on March 14, but were able to stop it and successfully restore all systems by the end of the day.
On March 21, the attackers released private medical records about thousands of former patients between the age of 8 to 20 years. The data included medical information, copies of their passports, driving licenses, insurance numbers, and more. Managing and clinical director and doctor at HMR said that they have no intention of paying the ransom: “I would rather go out of business than pay a ransom to these people.”
Here's where it gets interesting. On March 22, Maze released another official statement, explaining that the HMR attack happened on March 14, before they made the promise to stop all malicious activity against medical organizations. However, that doesn't explain why they decided to leak the private information after they made that very same promise. Fortunately, after the announcement, the Maze team took down from their website the stolen data from Hammersmith Medicines Research.
The thing is, even if they want to remain true to their promise, it's hard to say how much control they actually have over the choice of targets. You see, it's common for criminals to use a RaaS (Ransomware-as-a-Service) model, where they offer the malicious code to other crooks, called affiliates. It's up to the affiliates to deploy the actual ransomware, and later on, pay the creators of the malware. In most cases, the attack is conducted via scam email campaigns and attacks on RDP (Remote Desktop Protocol). So, hospitals can get attacked by mistake purely because malicious actors are targeting their victims by network vulnerability, not organization names.








